How to Prevent a NukeBot Trojan Attack
You should take immediate action
5 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- The NukeBot Banking Malware can affect banking systems but it may also infect your PC.
- This threat is actually a Trojan that mostly gets into your system via e-mail.
- Cleaning your e-mail inbox and spam folder in your account can clear this problem right away.
- You should also safeguard your computer with a powerful antivirus to block any intrusions.

While most of us use the Internet daily, not many of us are aware of the dark Web, a digital black market one can use to get their hands on literally anything.
And that includes even malware that can create havoc on your system, steal passwords and data, or just destroy them.
Nukebot is one such malware that was put up for sale in the cyber community. IBM X-Force Researchers were the first to find the malware advertised for sale.
However, unlike other malware that usually generates interest in the Dark Web community, NukeBot went almost unnoticed. The publisher of the malware was instead banned from several forums.
Thanks to the dented ego, the malware developer himself published/leaked the source code.
NukeBot turned out to be a Trojan that comes with a web-based admin panel that lets attackers control infected endpoints.
With the source code in the open apparently, the malware has been picked up, and NukeBot is currently being employed for attacks on the financial system.
As it happens with most of the leaked malware, the source code is most likely to be embedded into some other malware, and due to the variations, it is difficult to detect.
As the age-old saying goes, it is always better to be safe than sorry. One of the ways to do this is to put an end to malware even before it starts spreading and causing damage.
Banks and other financial services can actually take proactive measures before the malware hits their network. I have mentioned some elementary but practical steps in combating Nukebot.
How can I prevent NukeBot attacks?
1. Perform basic email hygiene
In most of cases, the threat’s first point of interaction is the PC or mobile endpoint. Social engineering is one of the most preferred methods to gain access.
It’s also advisable to install a comprehensive antivirus. Ensure that you toggle on the Safe Browsing feature on it.
Overwhelmed by an email attachment, you were not expecting? Think twice before opening such attachments, as this is one of the common ways to offload malware in your system.
Malicious e-mails usually seem to convey a rather exciting proposal and are most likely to have spell and other formatting errors.
Even if you are sure of the source, it’s always better to scan the attachments for malware before actually opening it.
2. Avoid transactions on the public networks
Malware is often injected via public Wi-Fi, so it’s advisable to use a VPN. This will help you prevent NukeBot from infecting your device.
And if you don’t know what solution to choose, we have an excellent selection with the best VPNs for Windows 10 that you can use right now.
3. Install a powerful antivirus
The danger is lurking everywhere online and in your inbox. Although you know precisely not to roam around dark places on the Internet, mistakes can happen anytime.
And if you make the mistake, you need a safety net that can identify, block, or delete the threat right away and that’s what the recommended antivirus below is for.
It will act as an active shield for your PC and protect your other devices, like the router and even the webcam.
This tool has a 30-day free trial period to see its protective power immediately before you buy it.

ESET HOME Security Essential
ESET’s security solution can protect your devices and stop all threats with a single license.4. Stay away from free stuff
As a rule of thumb, stay away from free stuff, especially on a computer that you use for online transactions. Malware is often baked into free campaigns and exploit kits are injected into the victim’s computer.
The free offers usually come with a backdoor to the endpoint eventually pushing the spyware, ransomware, or banking trojans to the endpoint.
5. Update all your devices
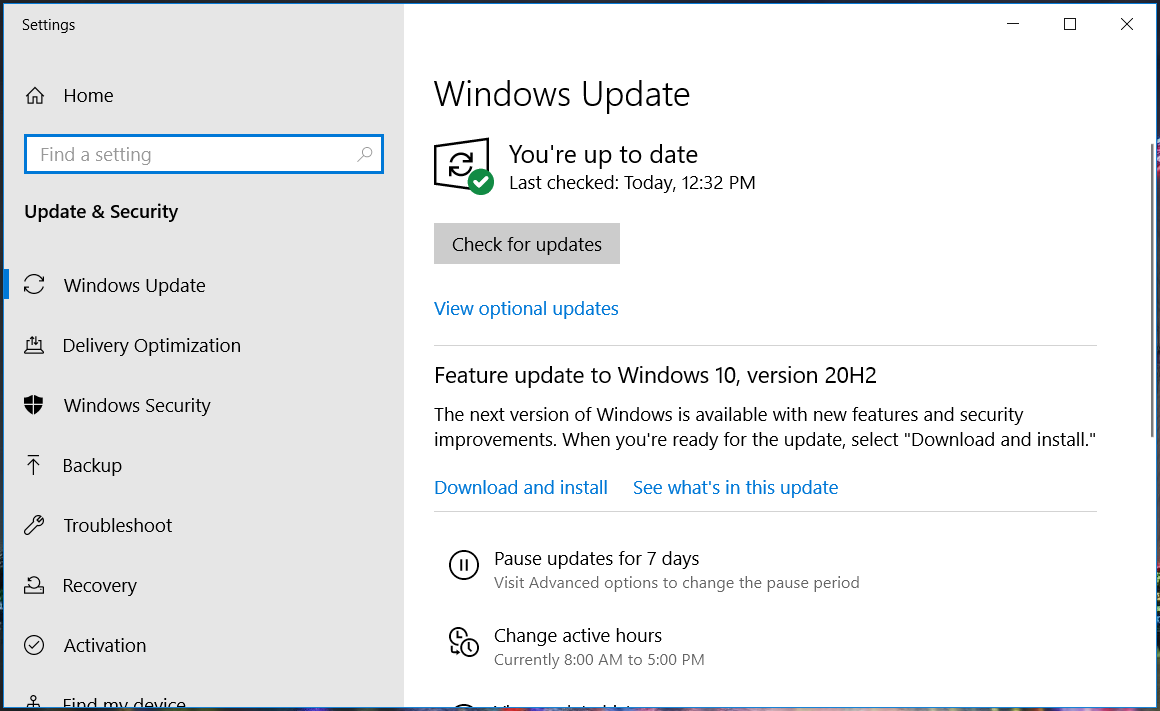
- Type update in the Windows Search bar and click in Check for updates.
- Click Check for updates and install all available updates.
- Restart your PC for the changes to take effect.
A healthy and updated system is always harder to penetrate than a neglected one so start by updating your Windows 10 as shown above.
Make sure that you update all your devices, including smartphones, to the latest security update. This is very crucial as the manufacturer usually deploys a patch for exploits in every security update.
Lock both your smartphone and computer with a password. It’s also advisable to not root or jailbreak your phone as this might help intruders find more back doors.
6. Use additional security measures
Look out for odd behavior and ensure that you switch on the two-factor authentication for all the third-party apps. Furthermore, it’s also advisable to use a security app for mobile devices as well.
The steps above will help you prevent a NukeBot attack and safeguard you from other malware with similar traits like Zeus malware.
As this malware’s point of entry is regularly the e-mail, you should also consider installing one of the best e-mail scanning software for your PC.
If you’ve been a victim of this NukeBot virus or have any other suggestions on tackling this problem, tell us everything about it in a comment below.