Locky ransomware spreading on Facebook cloaked as .svg file
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Spamming and ransomware are the most common forms of cyber crime encountered today. FBI records suggest that there has been $1 billion of money secured by cyber criminals in 2016 alone. As dangerous and untraceable as these crimes may be, encountering them on well-known, trusted sites make them even more perilous. This time, spammers have targeted Facebook.
Facebook has been marked quarantine after falling prey to a ransomware attack that has spread like wildfire over the social network. The notorious spam campaign involves the spreading of the Nemucod malware downloader among users, which in some cases was seen downloading the Locky ransomware. To make it even worse, there is no free decryption program available for Locky.
Locky ransomware is known to lock up an infected computer, encrypt its files then hold them ransom for a Bitcoin payment. There is still no concrete solution developed for Locky’s encryption so users have little hopes of ever recovering the damage.
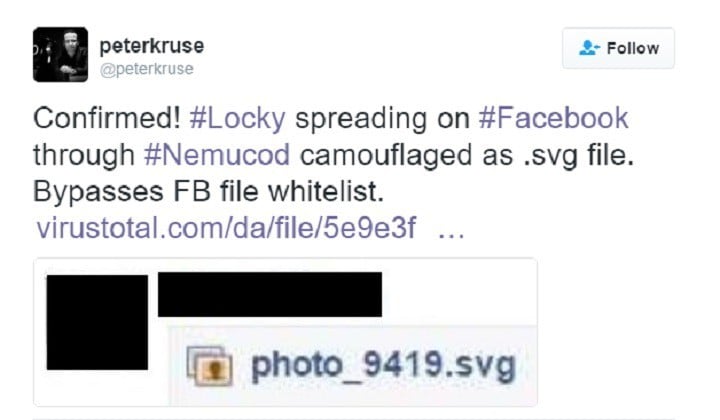
The threat was spotted by two security personnel specialized in internet-based crime and malware, Bart Blaze. who handles Threat Intelligence for multinational financial services company PricewaterhouseCoopers and Peter Kruse. an eCrime specialist for the Danish CSIS Security Group A/S. The peril was generated in the form of spam messages spread via Facebook’s IM system.
The virus evaded Facebook’s whitelisting by pretending to be a .SVG image file and was sent from compromised Facebook accounts. The infected files, unlike other common file types, have the ability to contain embedded content like JavaScript and can be opened in a modern browser. The reason the crooks opted to share SVG images is because it is XML-based and allows dynamic content so it was easier to cloak JavaScript code right inside the photo itself, which in this case was a link to an external file.
Opening the infected file redirects users to a spammy site, a copycat version of YouTube. The website doesn’t raise any red flags until it prompt users to install a malicious codec Chrome extension in order to watch the video. Upon allowing, the unsubstantiated extension will give it the capability to alter user’ data regarding the sites they visit.
As reported by Blaze, the extension will also spread the malware further on Facebook, compromising the victim’s account. The spammers can take over your account and further spread the malware among your social media friends by sending them spammy messages with the same SVG image file.
Safety Measures
For starters, and this one is pretty obvious: do not click any SVG file. If your close ones send you a message with the ransomware attached, you should warn them ASAP about their account being compromised.
Deny installing the Chrome extension and even if you do somehow click on the SVG file, one way to revert it is to go to the menu, navigate to ‘Extensions’ via Select More Tools, find the extension and then remove it before Necumod infects your system.
The next step would be to download a powerful internet security software. System Watcher is one of the most reliable tools to tackle the problem, developed by Kaspersky Lab. System Watcher is available on all of Kaspersky Lab’s main products like Kaspersky Anti-Virus, Kaspersky Internet Security, and the ultimate in computer security, Kaspersky Total Security.
But if you have gone past this, the safety ship has sailed and the most you can do now wipe your hard drive to get rid of the Locky ransomware and be more judicious about strange Facebook images next time.
RELATED STORIES YOU NEED TO CHECK OUT: