FakeNet finds out what malware is up to by monitoring network traffic
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
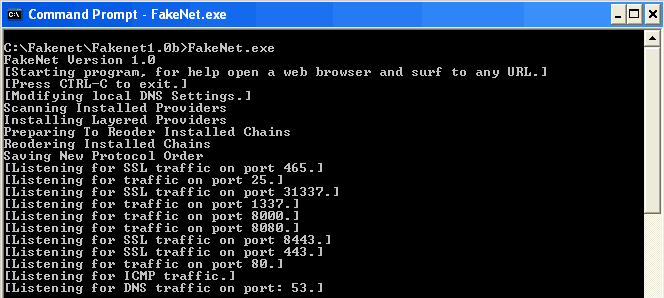
FakeNet for Windows allows you to see what malware is trying to do online. This tool is not like any other packet capture tool out there: FakeNet actually redirects internet traffic and handles it locally. In other words, if you notice that malware is trying to download another infected file from the internet, this will NOT succeed.
You will not need to install FakeNet on your computer to have it work. You only need to unzip the download file and launch it. Once you run FakeNet, it will change your DNS settings to point at localhost, which means all the traffic will be redirected to your own machine and will not get out on the internet.
By opening the browser, collecting emails or doing anything else web-related, FakeNet will display the DNS, URL and other details in a console window. FakeNet will detect and display details of HTTP traffic, ICMP, HTTPS, DNS and will also listen to common ports such as 1337, 8080, 8000 and others. While testing it, we noticed what some applications were capable of doing and are happy to report they couldn’t due to the tool. FakeNet is expected to support even more protocols in the future, but you will have to write Python scripts in order to do it.
This tool should be used with caution by default it will change your DNS settings. However, DNS settings will change only if you close the tool properly. In other words, if you run FakeNet and you close the command window by just clicking the top-right “X”, the DNS will not be restored and you will have to manually restore them.
Have you used FakeNet before? Tell us your thoughts about it!
RELATED STORIES TO CHECK OUT: