Oracle Releases Security Patch to Eliminate Java Vulnerabilities on Windows
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

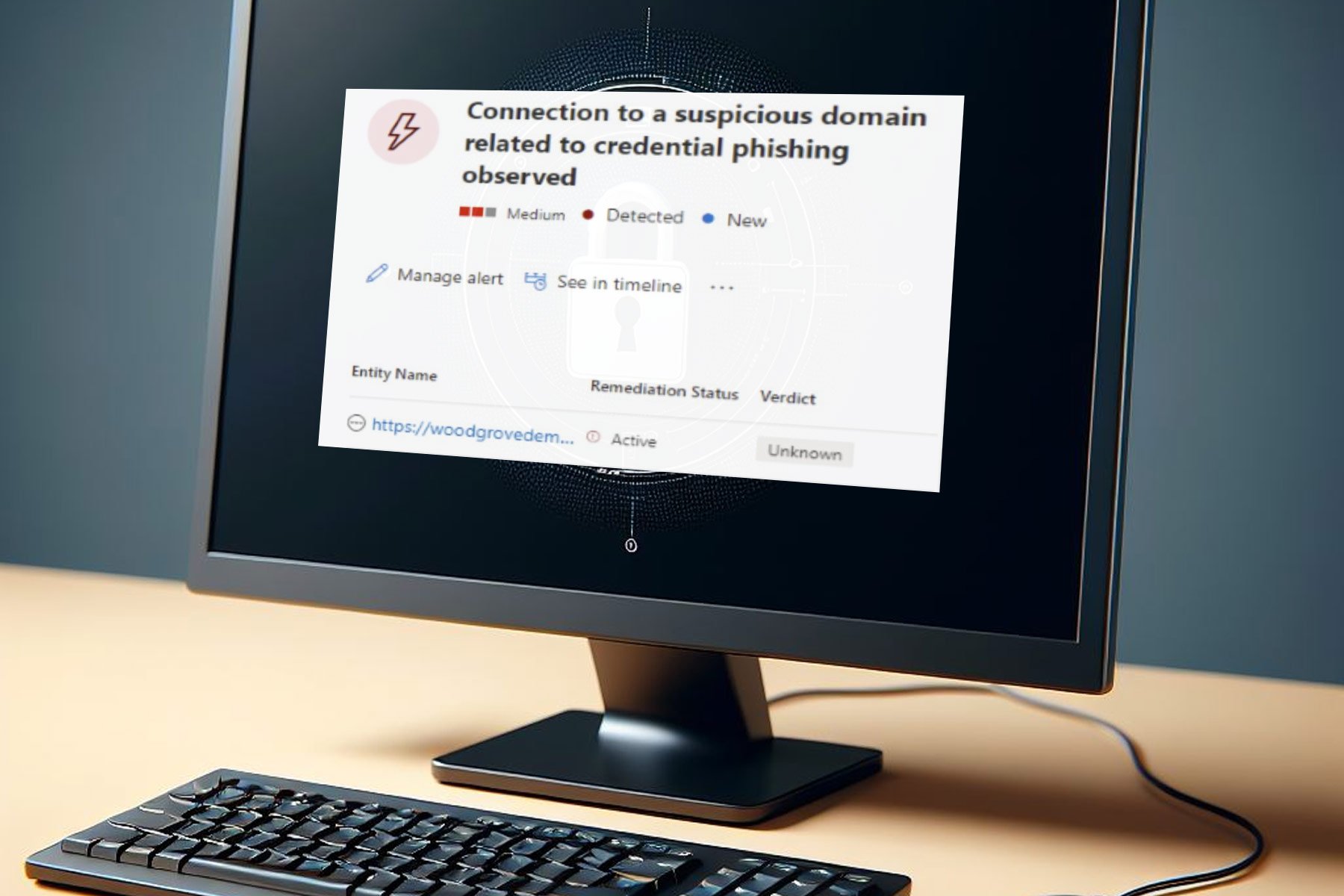
Oracle just issued a security patch for a Java vulnerability, which can be exploited when installing Java 6, 7 or 8 on the Windows platform. The latest Java security patch is labelled as Security Alert CVE-2016-0603. As Oracle says, the vulnerability could cause a ‘complete compromise of the system,’ if successfully exploited.
The vulnerability allows malicious software to be installed on users’ computers when they visit a malicious site, and download suspicious files on their computers. However, the vulnerability is present only during the installation process of Java 6, 7 and 8, which makes it relatively complex to exploit, but additional security measures can’t hurt.
“Because the exposure exists only during the installation process, users need not upgrade existing Java installations to address the vulnerability. However, Java users who have downloaded any old version of Java prior to 6u113, 7u97 or 8u73, should discard these old downloads and replace them with 6u113, 7u97 or 8u73 or later, “ says Oracle.
Security Alert CVE-2016-0603 is cumulative, which means that once you download it, you will also receive all previous Critical Patch Updates and Security Alerts released by Oracle
Use official Java downloads only!
Along with the announcement, Oracle also warned users to download all Java installers from its official site only, because downloading Java from an unofficial site could lead to downloading a malicious software.
“As a reminder, Oracle recommends that Java home users visit Java.com to ensure that they are running the most recent version of Java SE and that all older versions of Java SE have been completely removed. Oracle further advises against downloading Java from sites other than Java.com as these sites may be malicious.”
Attackers are looking for various ways to “break into” users’ PCs, mainly through third-party programs and services. We remind you that Adobe also released a security update for its Flash Player, some time ago, which tells us that companies are aware of the possible vulnerabilities, and they’re constantly working on new security patches to make users as safe as possible.