Employee Monitoring Software: 8 Best in 2024
15 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- A successful business means having hard-working and dedicated employees who will do their job even remotely.
- As a business owner, you need to make sure your employees aren't doing non-work-related activities during their working hours.
- We've included both paid and free employee monitoring software, from developers that are more or less known.
In the modern competitive business world, all organizations are facing new challenges regarding sustained productivity. Things are no different when it comes to creating the most committed workforce.
Obtaining the target output in any organization depends mostly on the consistency of the productivity level of the employees.
In today’s business environment, no organization can perform at its highest levels of productivity unless each employee is committed to improving the organizational levels of productivity.
This means that the employees will contribute to the business’ growth. But unfortunately, some business owners tend to fail in monitoring the daily productivity of their employees.
The result is the fact that their job performance will be detrimental to the business’ growth and this thing will not be able to be detected and controlled.
Such a thing would ruin the business’s ability to achieve its objectives. Thanks to workforce management apps and the software tools for monitoring employee productivity, things are easier for organizations.
They don’t have to wait for a much too long duration of employees’ performance appraisal programs to know how they’re doing at work.
Why should I buy an employee monitoring software?
Emails are the primary source of data breaches for companies because employees have to exchange information through business correspondence. It’s crucial to secure and track data when you are required to comply with HIPAA laws, GRAMA requests, and FINRA regulations.
There are some simple email surveillance solutions available on the market. Use them to monitor employees’ emails to make sure that critical data is not being shared purposely or inadvertently.
Employee monitoring programs include email-monitoring abilities and more tools for monitoring other activities of the employees while they’re doing their jobs.
Another central aspect of employee monitoring software is the capacity to check their activity while using the company’s equipment such as its laptops and desktops.
Such solutions will be able to let you see which websites are being accessed by your employees. You can also discover who are the employees that usually download files, and when they connect or remove USB drives.
These tools will also be able to alert you when particular keywords are being searched that require concern from your company. These include job searching, pornography search, or searches related to competitive contacts.
The best tools for monitoring the workplace will offer you administrative control. This will allow you to block such kinds of activities and also restrict access to inappropriate or unsecured websites.
You can successfully use tools for monitoring your employee’s work for finding out what an employee is up to these days.
Here are our best picks for monitoring employees’ activity.
What is the best software to monitor employees?
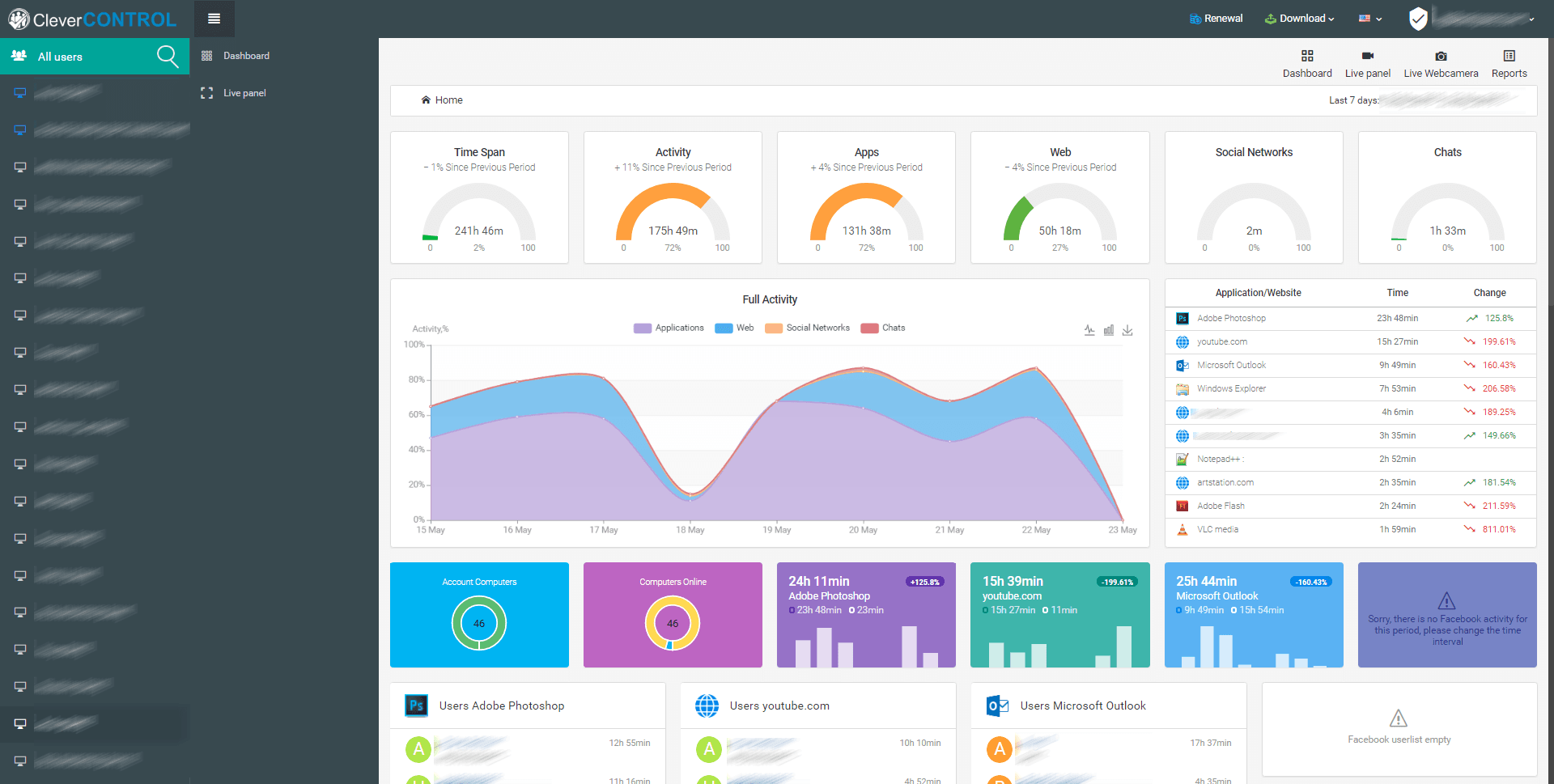
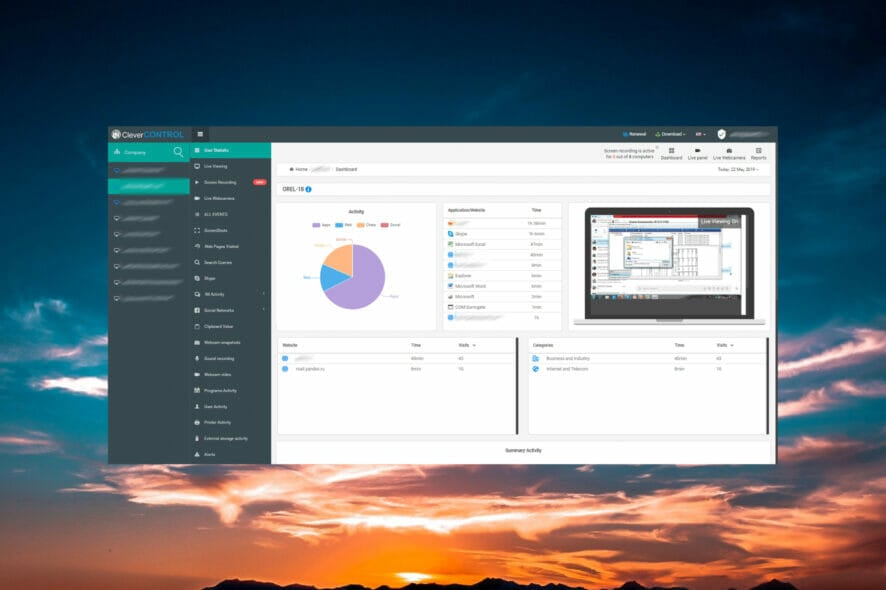
CleverControl Employee Monitoring – Best employee monitoring
CleverControl Employee Monitoring is a tool you can use to control computers remotely with a simple secure web account.
The app is perfect for employee monitoring but it can also be useful for parental control. Its job is to record all computer activity and sends the new data straight to your online dashboard.
It’s so effective that you may even block websites or the use of certain keywords. Not only that but if you set a filter for certain keywords, you will be notified if someone uses them.
Of course, the IT manager will be able to monitor all URLs from the devices to know what websites and pages the users visited.
For short, CleverControl Employee Monitoring provides total control over employees’ computers, a perfect tool to detect slackers, prevent data leakage and investigate potential unlawful actions.
After you install the CleverControl Agent on target computers, all new data collected from the devices is sent to your online dashboard.
Then, you can sign in to your online account via any device or check the logs locally in the application.
The app also delivers the logs via email so you will still get them over a specified time interval.
Let’s review some of its best features:
- Web-based cloud dashboard accessible from any device
- Full control of all the employee computers
- Set keyword filtering and block websites
- Monitor and filter websites visited by the employees
- Easy to implement and use

CleverControl Employee Monitoring
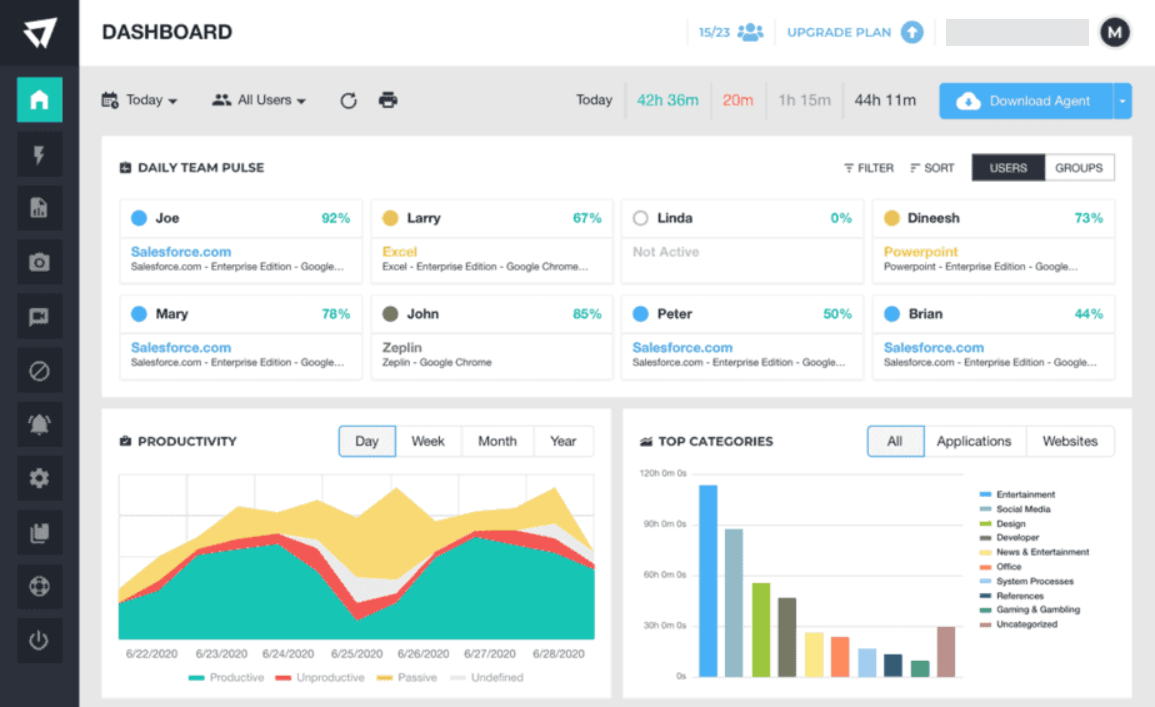
Control all the computers of the employees with this smart app that features full logging.ActivTrak – Detailed reporting and graphs
Monitoring your employees can be time-consuming, so that is why ActivTrack’s main focus is transparency and easy setup.
Monitoring your employee’s work habits has never been easier, thanks to the detailed graphs that show you exactly everything you need to know.
This is further emphasized by the automated reports, flexible productivity settings, and granular reporting to deliver immediate transparency with precise detail.
The program is easy to set up, and it manages to do the job regardless of whether the monitored parties are in the office building or working remotely.
More so, the program integrates perfectly with other apps that you would commonly find in an office environment, including Slack, GitHub, QuickBooks, Trello, and more.
All in all, it does an excellent job at finding hidden productivity killers, so that your workforce stays focused on the project at hand throughout their entire designated work shift.
Take a look at some of its key features:
- Detailed graphs on employee activity
- Great app integration including Slack, GitHub, and many more
- Provides automated reports
- Easy to set up and use
- Remote computer captining

ActivTrak
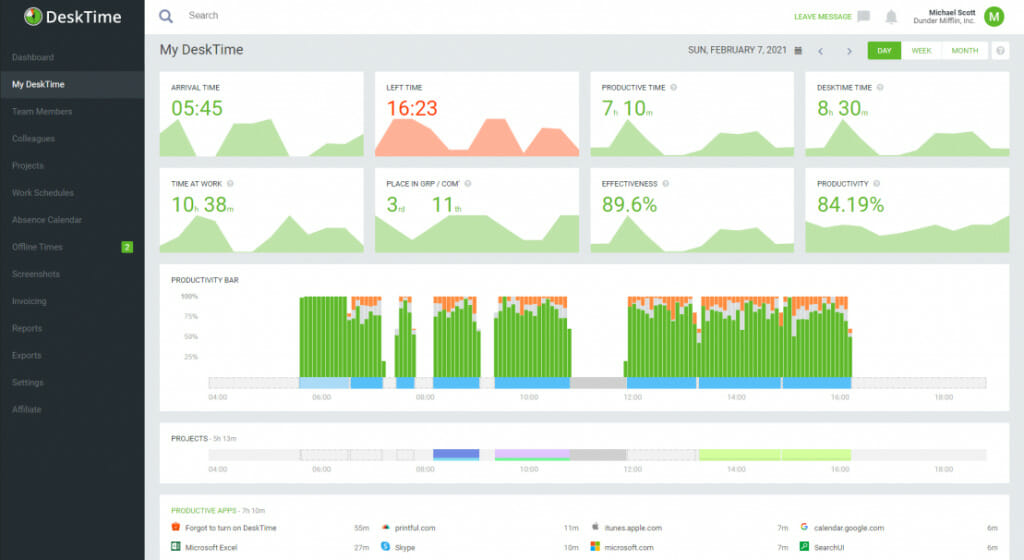
Get the insights you need to boost productivity and efficiency in the workplace with ActivTrak.DeskTime – Great time-management tool
DeskTime is a simple and secure time tracking app that allows you to increase your company’s efficiency and productivity.
Using this tool, you can monitor the daily activity, sick leaves, overtime work, and vacations of your employees easier. You will be able to get a clear overview of your team’s workflow.
With DeskTime you can track apps, URLs, and also offline time and access detailed data regarding the ways that your employees are using apps and websites and what they’re doing when they are not online.
The tool offers your auto screenshots and activity rate trackers which will allow you to follow the time spent on individual projects.
DeskTime provides in-depth insights and reports for billing, and you can use it to customize easily download, and also send CSV reports to give your clients the most precise information regarding the amount of work and time spent on all the projects developed by the business.
You can oversee local and remote teams from both your mobile and your desktop and this way you’re able to save time by looking over the reports on the performance of your business while you are on the go.
The tool’s support team is available via chat, voicemail, and also email. The team from DeskTime follows the industry security standards to secure the personal information that they are provided with.
Check out its best features below:
- Monitor the daily activity, sick leaves, overtime work, and vacations of your employees
- Track apps, URLs, and offline time
- Automatic screenshots and activity rate trackers
- In-depth insights and reports for billing
- Accessible from mobile and desktop platforms

DeskTime
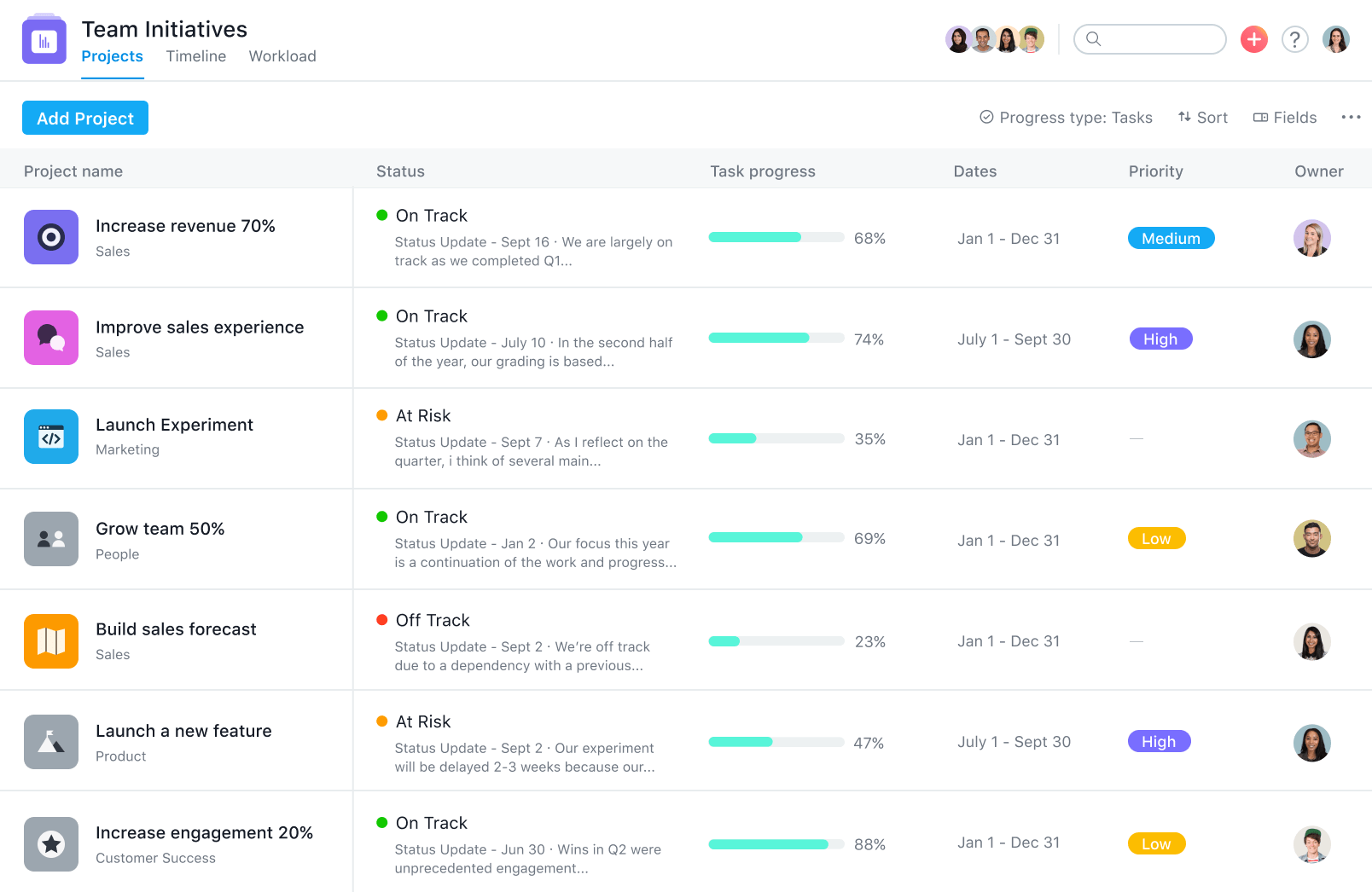
A desktop and mobile app for time tracking, attendance tracking, and effective workflow management.Asana – Ideal for project management tracking
Asana is a tool that offers tasks, projects, dashboards, and conversations in order to allow teams to move work more efficiently from start to finish.
You can use it to see the progress of any project without scheduling a status meeting or without having to send emails.
With this tool, you will be able to use custom fields to track anything that is of great importance to you whether it’s bugs, job applicants, or leads.
You can organize your tasks into shared lists or boards for all of your meetings, programs, and initiatives.
The sections and columns will let you customize Asana in order to match your workflows and to add structure to all of your projects.
You will be able to break up the work of a task into smaller parts or divide the work among multiple projects and when a single task becomes a big and important initiative you will be able to quickly turn it into a project.
Take a look at its key features:
- Tasks, projects, dashboards, and conversations management
- Detailed insight into development projects
- Organize your tasks into shared lists or boards
- Advanced reporting features

Asana
Run your business efficiently with trustful employees and monitor their productivity for better results.Wrike – Great for project management
Wrike is a great collaboration tool and World’s number one project management tool and it will surely help you to monitor and boost your employee’s productivity when you’ll see some changes in your company.
These are just some major features that will help you monitor and manage your employees but you can use Wrike to find more functionalities that will work for you.
Remember that this tool must be a friend for you and your team, not a reporting channel to make your employee’s life harder. We suggest you try it, as it offers a free version.
Let’s see what Wrike can offer you in terms of managing employees and teams of employees:
- Real-time work progress visibility
- Advanced reporting for project progress
- Efficient resource management
- Standardize repetitive processes

Wrike
Crush your 2022 goals and keep moving forward with Wrike’s work management platform.Screenshot Monitor – Simple and light monitoring app
Screenshot Monitor is a great tool for working remotely. This lightweight desktop application allows employees to start and stop monitoring themselves.
The program automatically tracks time and screenshots the tasks that users make while it’s running.
Afterward, the screenshots are sent to the software’s official site securely, where they can be viewed in real-time.
Moreover, the app can be used from any device directly, without any installation. Therefore, the app ensures your employees are spending their time working.
Take a look at some of its most important features:
- Light application
- Auto monitoring features for employees
- Automatically tracks time and screenshots the tasks
- Can be used from any device directly, without any installation

Screenshot Monitor
Simple, but powerful tool you can start using in your business in 10 minutes.Teramind – Ideal for analyzing employee behavior
Teramind provides software that streamlines the process of collecting employees’ user behavior on PCs in order to identify suspicious activity, monitor efficiency, and effectiveness, detect possible threats and ensure industry compliance.
Teramind’s mission is to reduce security incidents by providing real-time access to user activities by offering warnings, alerts, redirects, and user lock-outs for keeping businesses and organizations as secure and as efficient as possible.
The software comes in both on-premise and Cloud-based deployment options to meet any organization’s requirements.
Teramind can successfully identify which users are most risky to your business by analyzing the trends in their behavior.
You can check out what particular policies they have violated and then educate them in order to prevent future incidents.
With this tool, you can also write rules that react to any observable user activity such as blocking an email from being sent or alerting when a particular document is being printed.
You also have the ability to record and log all activity, and they play it back like a video and analyze session metadata.
To get started with the software you have to follow these steps:
- Sign up to Teramind Basic Cloud employee monitoring software for free
- Full or part time options for control
- Customize alerts and monitoring settings to tailor the platform to your needs
- Access all features from the software’s platform to enhance both security and productivity
WorkiQ – Great employee activity analysis
WorkiQ is a tool that tracks employees’ computer behavior and provides reports on their time spent on non-productive and productive applications.
The tool’s dashboard provides clear visuals which will tell you which employees and actively engaged in their work and which ones are being continuously distracted.
This tool offers you the power to categorize all kinds of activities, track processes across all applications, and compare how different users process similar units of work.
The management dashboards will provide the following advantages:
- Identifying unproductive behaviors at the moment of occurrence
- Spotting and also rewarding productive behavior
- Comparing actual employee productivity
- Managing remote workers
- Identifying top performers to replicate their processes across time
- Improving the distribution of work through the identification of certain criteria
What should you take into consideration legally and technically speaking?
Monitoring employees’ emails may seem an infringement of employees’ privacy. The US Supreme Court ruled back in 2010 that it is legal for organizations and companies to monitor the actions of employees while they’re at work and while they’re using the business’ equipment.
This includes pagers, laptops, USB drives, and mobile devices. Programs for monitoring key logs and for capturing passwords can be used even if there is some ethical controversy around the subject of their usage.
It is important to remember that the federal government doesn’t place restrictions on employee internet monitoring. On the other hand, there are some individual states that put protection first.
More and more states are currently requiring employees to notify their workers in case their company monitors employees’ online activity and this includes keystrokes and emails.
Such notifications can be disclosed within the employee handbook or as an email reminder.
Stealth mode vs. transparent mode
When employers are using such monitoring tools, they can choose the option of using their stealth or transparent mode.
Stealth mode is also known as a silent mode. This means that the employees cannot see the fact that they’re being monitored. High-quality monitoring tools will run unseen and undetected by employees.
The transparent mode of surveillance will allow your employees to see the surveillance program on their systems. Such software requires installation on each individual computer including the administrative portal.
This will not be as easy as stealth mode since the admins will have to check each and every single report from each system to see how the employees are doing.
How do monitoring tools work?
Employee tracking tools must be installed on multiple systems including a central station in case employers want them to go undetected by users.
In order for this type of tool to work properly, you must first turn off the firewall, and it will be turned back on once the installation process is complete.
On the other hand, it is virtually impossible for the program to work without additional patches and programming to enable PC-monitoring software to work around the program.
This will puncture a hole in the security system. It will make the network vulnerable to all kinds of malware, viruses, spyware, and so on.
Be cautious at viruses in disguise
You should be aware of the fact that there are many employee surveillance tools that are actually viruses in disguise and while they may give you keylogging and password-capturing capabilities, they’ll also collect the data behind the scenes and sell it to breach the organization’s security.
Most of the tools for monitoring employee activity can work around the firewall, but it is still possible that some threats pass through undetected. There is plenty of antivirus software that will keep employees and the company safe.
Deploying the software: Cloud and on-premises
Another important aspect to consider is the way that you are implementing the software. On-premises is the most commonly used option, and most tools offer it.
This will allow you to host the program and the data it collects on your own server. This solution requires a bit more IT knowledge, and it can take longer to set up.
Cloud solutions, on the other hand, are easier to manage and they can be set up quicker than on-premises deployment.
Solutions that suit your needs
Parental software and monitoring software are two solutions that monitor personal computer usage. They are both installed and used on a single computer. Also, they don’t pose the same threats as the email surveillance tools, for instance, that we already said work around firewalls.
Monitoring software and parental software come with additional options that are designed to prevent cyber attacks. There are also tools for monitoring children and spouses when they go online.
There are lots of businesses that are also on the lookout for email software and for apps that monitor outbound and inbound messages for spyware, viruses, and Trojans.
There’s also email encryption software that can safeguard personal data and critical information when it is transmitted to third-party recipients.
Such tools will make sure that the sensitive data is only accessed and used by individuals who really need the info while also keeping it as secure as possible.
Employees’ behaviors are unpredictable. With the help of these great tools, you will be able to increase their efficiency at work and your business’s overall productivity.
Browse through all of them and choose your favorite one, according to your needs. We guarantee high quality for all the tools we have discussed above for monitoring your employees’ activity at work.