Be careful, your Lenovo laptop could be vulnerable to a nasty bug
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Lenovo users should be really careful with how they protect themselves.
- A new bug allows attackers to execute commands with admin privileges.
- Needless to say that this could have severe consequences on all involved.
- The only workaround available for this bug is actually considering updating.
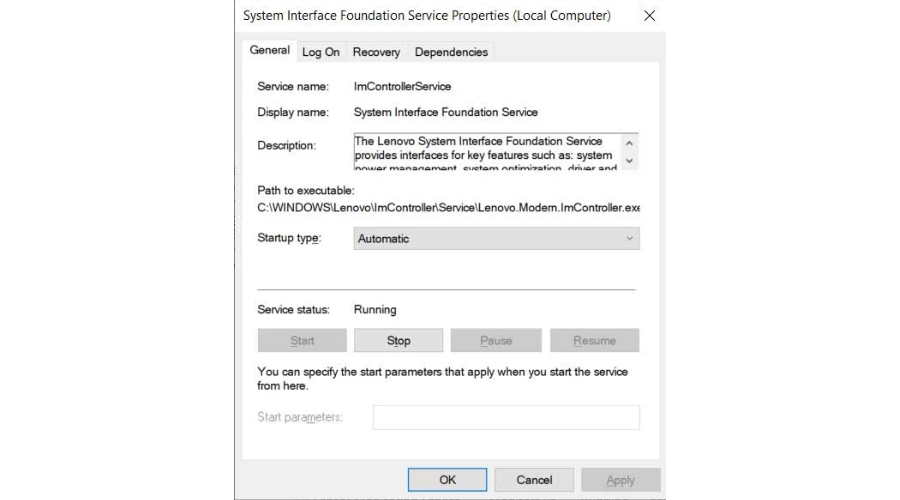
You might want to know that Lenovo laptops are now vulnerable to a privilege elevation bug in the ImControllerService service.
This nasty glitch can actually allow attackers to execute commands with admin privileges on your Lenovo device.
These flaws are tracked as CVE-2021-3922 and CVE-2021-3969 and affect the ImControllerService component of all Lenovo System Interface Foundation versions below 1.1.20.3.
And, when viewing the Windows services screen, this phenomenon has a display name of System Interface Foundation Service.
Lenovo laptops vulnerable to bug allowing admin privileges
This service is actually a component of Lenovo System Interface Foundation, which helps Lenovo devices communicate with universal apps like Lenovo Companion, Lenovo Settings, and Lenovo ID.
Also, the above-mentioned service is preinstalled by default on numerous Lenovo Models, including Yoga and ThinkPad devices.
The Lenovo System Interface Foundation Service provides interfaces for key features such as system power management, system optimization, and driver and application updates.
Furthermore, it also provides it for system settings to Lenovo applications including Lenovo Companion, Lenovo Settings, and Lenovo ID.
These vulnerabilities were discovered by a group of researchers at NCC Group, who reported their findings to Lenovo on October 29, 2021.
Lenovo released the security updates on November 17, 2021, while the relevant advisory was published on December 14, 2021.
Needless to say, system privileges are the highest user rights available in Windows and allow someone to perform almost any command on the operating system.
Thus, if a malicious third party gains access to system privileges in Windows, they gain complete control over the system to install malware, add users, or change almost any system setting.
The service will in turn spawn further child processes, which open named pipe servers that the ImController service used to communicate with the child process.
Unfortunately, the service doesn’t handle the communications between privileged child processes securely and fails to validate the source of XML serialized commands.
How can I fix this problem?
If you were thinking about taking matters into your own hands and fixing this serious problem, updating is the only way to do it.
All Windows users with Lenovo laptops or desktops running the ImController version 1.1.20.2 or older are advised to upgrade to the latest available version (1.1.20.3).
To determine what version you’re running, follow these steps:
- Open File Explorer and navigate to C:\Windows\Lenovo\ImController\PluginHost\.
- Right-click on Lenovo.Modern.ImController.PluginHost.exe and select Properties.
- Click on the Details tab.
- Read the File version.
However, Removing the ImController component, or the Lenovo System Interface Foundation, from your device, is not officially recommended because it may affect some functions on your device, even if it’s not considered essential.
Have you also encountered these types of problems on your Lenovo setup? Let us know in the comments section below.