Users without MFA are easy prey for new phishing device registration trick
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Microsoft warns users everywhere about a new, evolved phishing campaign.
- These attacks are much easier to carry out undetected in this hybrid work era.
- The plan is to join an attacker-operated device to an organization’s network.
- Security experts state the victims are even more exposed without the MFA.

Just because you haven’t heard of any recent major cyberattacks, doesn’t mean that they’ve stopped. On the contrary, malicious third parties are always cooking up new and ingenious ways to get into our devices.
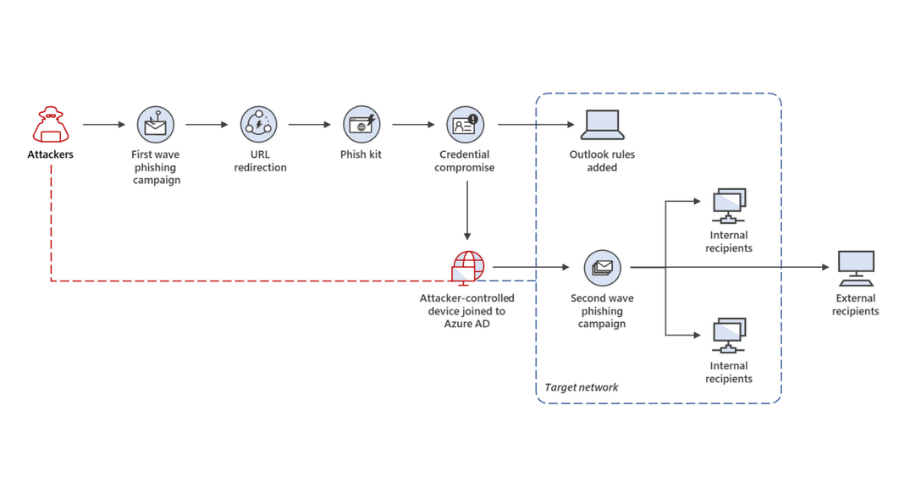
Recently, Microsoft uncovered a large-scale, multi-phase campaign that adds a new technique to the traditional phishing tactics by joining an attacker-operated device to an organization’s network.
Redmond security experts claim they observed that the second stage of the campaign was successful against victims that did not implement multifactor authentication, which is an essential pillar of identity security.
Microsoft exposes a new, evolved phishing campaign
The first phase of this hacking campaign actually focuses on stealing credentials in target organizations located predominantly in Australia, Singapore, Indonesia, and Thailand.
Afterward, attackers used compromised accounts to expand their foothold within the organization via lateral phishing as well as beyond the network via outbound spam.
Needless to say, connecting a compromised device to the network allowed cybercriminals to covertly propagate the attack and move laterally throughout the targeted network.
And while in this case device registration was used for further phishing attacks, leveraging device registration is on the rise as other use cases have been observed.
Furthermore, the immediate availability of pen-testing tools, designed to facilitate this technique, will only expand its usage across other actors in the future.
This campaign demonstrates that the continuous improvement of visibility and protections on managed devices has forced attackers to explore alternative avenues.
And, because of the increase in employees who work-from-home, which shifts the boundaries between internal and external corporate networks, the potential attack surface is further extended.
Malicious third parties deploy various tactics to target organizational issues inherent with hybrid work, human error, and shadow IT or unmanaged apps, services, devices, and other infrastructure operating outside standard policies.
It’s easy for these unmanaged devices to be ignored or missed by security teams, making them lucrative targets for compromising, quietly performing lateral movements, jumping network boundaries, and achieving persistence for the sake of launching broader attacks.
Microsoft security experts are more concerned about when attackers manage to successfully connect a device that they fully operate and is in their complete control.
In order to stay safe and not fall victim to the increasing sophistication of attacks, organizations need solutions that deliver and correlate threat data from email, identities, cloud, and endpoints.
Microsoft 365 Defender coordinates protection across these domains, automatically finding links between signals to provide a comprehensive defense, which is how Microsoft was able to uncover this campaign.
Are you taking all the appropriate measures to ensure the safety of your sensitive data? Share your opinion with us in the comments section below.