GitHub will receive continuous threat monitoring from Microsoft's Sentinel
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Afraid malicious third parties will use GitHub to get their software into your PC?
- Microsoft is working on a scenario where all this can be prevented in the future.
- The Redmond giant announced that GitHub will soon receive better monitoring.
- This will provide capabilities such as new repository creation or deletion, etc.

It’s safe to say that almost all of us know what GitHub is and have probably used it at least once in our lives.
Now, the widely used code-hosting platform is about to receive enhanced security and continuous threat monitoring from Microsoft Sentinel.
The Redmond giant’s repository is receiving deeper integration with Microsoft’s Security Information and Event Management (SIEM) platform.
It is highly important to track the different activities in the company’s GitHub repository, to identify suspicious events, and to have the ability to investigate anomalies in the environment.
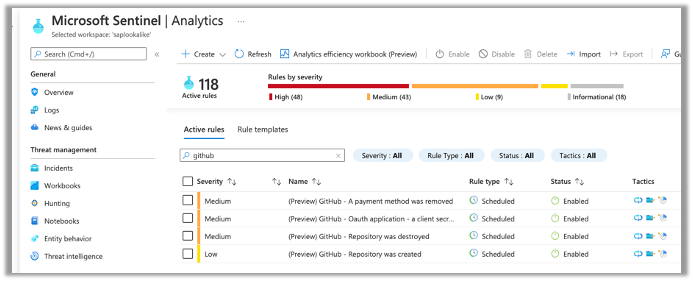
GitHub will a safer place thanks to the Sentinel
Yes, this new initiative actually allows Microsoft Sentinel to ingest GitHub audit logs, providing capabilities such as tracking for events, including new repository creation or deletion, and counts for the number of repository clones.
Tracking the different activities in the company’s GitHub repository is of paramount importance, in order to identify suspicious events, and to have the ability to investigate anomalies in the environment.
Sentinel’s customer base grew by 70% within a single year, and it currently has about 15,000 customers, according to Satya Nadella.
The company’s online security arm is growing rapidly, and Nadella added that it has managed to earn revenue of more than $15 billion in the past 12 months.
In the blog post, Microsoft also presented four different analytics rules:
- Repository was created – this alert is triggered each time a repository is created in the GitHub environment that is connected to the Microsoft Sentinel workspace. In addition to the repository name, we get the actor who created this repository, so there’s an option to track the repositories and who is creating them.
- Repository was destroyed – this alert is triggered each time a repository is destroyed in the GitHub environment. It’s critical to track the repositories being destroyed in order to verify that the users destroying repositories have the correct permissions, and these actions are not part of a malicious activity.
- A payment method was removed – this alert is critical to know about and is triggered each time there’s an action with the payment method configured for the GitHub repository. It’s important to know when the payment method is removed in order to validate who performed the action and that you’re aware of the issue.
- OAuth application – this alert is triggered each time a client secret was removed, which is another high-priority alert that you should be aware of. In case a secret is accidentally exposed, you’ll want to ensure that the old secret can be removed.
This security strategic move comes amid growing concerns about application security and the prevalence of insecure software supply chains.
High-profile incidents have included the SolarWinds and Kaseya breaches, while overall attacks involving software supply chains surged by more than 300% in 2021, Aqua Security reported.
Open-source vulnerabilities such as the widespread flaws in the Apache Log4j logging library and the Linux polkit program have underscored the issue.
Recently, The Open Source Security Foundation announced a new project designed to secure the software supply chain, backed by $5 million from Microsoft and Google.
What’s your take on this whole situation? Share your thoughts with us in the comments section below.