Be careful when installing Telegram, you might also get Purple Fox malware
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- A lot of people are using Telegram nowadays, as a safer means to communicate.
- But all this privacy can come at a cost if we are not paying attention to the signs.
- A Telegram for desktop installer has been seen spreading more than just privacy.
- Embedded deep in the Telegram installer is the dreaded Purple Fox malware rootkit.

Everyone knows by now that Telegram is among some of the safest software choices for communicating with others if you really value your privacy.
However, as you will soon find out, even the safest options out there can turn into security hazards if we’re not careful.
Recently, a malicious Telegram for desktop installer started distributing the Purple Fox malware to install further dangerous payloads on infected devices.
This installer is a compiled AutoIt script named Telegram Desktop.exe that drops two files, an actual Telegram installer, and a malicious downloader (TextInputh.exe).
Telegram installers will install more than just the app itself
It all starts like any other banal action that we perform on our PCs, without actually knowing what goes on behind closed doors.
According to security experts from Minerva Lab, when executed, TextInputh.exe creates a new folder named 1640618495 under:
C:\Users\Public\Videos\
Actually, this TextInputh.exe file is used as a downloader for the next stage of the attack, as it contacts a C&C server and downloads two files to the newly created folder.
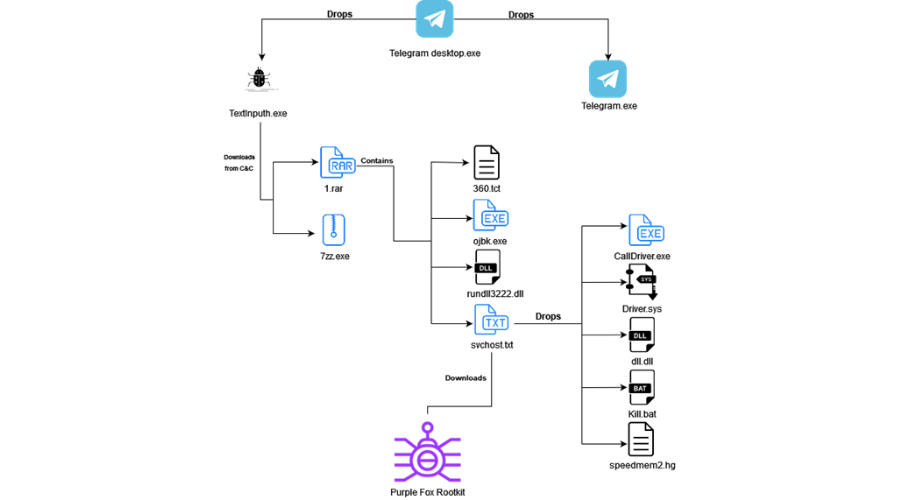
In order to get a more in-depth view of the infection process, here’s what TextInputh.exe performs onto the compromised machine:
- Copies 360.tct with 360.dll name, rundll3222.exe, and svchost.txt to the ProgramData folder
- Executes ojbk.exe with the “ojbk.exe -a” command line
- Deletes 1.rar and 7zz.exe and exits the process
The next step for the malware is to gather basic system information, check if any security tools are running on it, and finally send all that to a hardcoded C2 address.
Once this process is completed, Purple Fox is downloaded from the C2 in the form of a .msi file that contains encrypted shellcode for both 32 and 64-bit systems.
The infected device will be restarted for the new registry settings to take effect, most importantly, the disabled User Account Control (UAC).
It’s unknown for the time being how the malware is being distributed but similar malware campaigns impersonating legitimate software were distributed via YouTube videos, forum spam, and shady software sites.
If you want to get a better understanding of the entire process, we encourage you to read the full diagnostic from Minerva Labs.
Do you suspect to have downloaded a malware-infected installer? Share your thoughts with us in the comments section below.








