Microsoft introduces new capabilities to Windows Hello that make it stronger
Windows Hello is the way go passwordless.
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
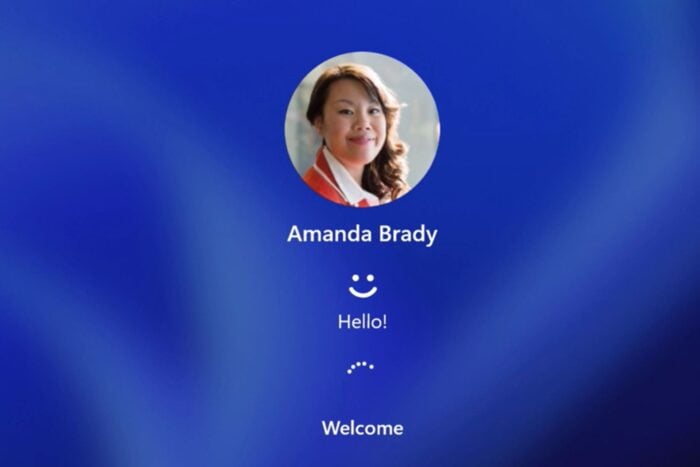
In a time when digital safety is crucial, Microsoft’s Windows Hello for Business has made a big leap to improve it. This new capability substitutes passwords with powerful two-factor confirmation.
Signing in requires an enrolled device and a PIN or biometric input, such as fingerprint or face recognition. This strategy boosts security and smooths the user’s experience. Just think about it: You no longer need to recall or alter intricate passwords frequently. It sounds handy.
According to the official blog post, Windows Hello for Business fits well with Microsoft’s current identity structure, making remote entry solutions simple. This system is a component of Microsoft’s wider Zero Trust security plan, which focuses on ensuring user identity security by using strong authentication and completely removing passwords.
It’s simple yet powerful in its approach. It uses public key or certificate-based authentication, which is more robust against breaches, thefts, and phishing.
If you are curious about the technical aspect, Windows Hello for Business can authenticate users to a Microsoft or Active Directory account. It is also possible to have a Microsoft Azure Active Directory (Azure AD) account.
This feature works well on devices with a trusted platform module (TPM) chip because the PIN is supported by strong security hardware called TPM. Additionally, certificate renewals occur automatically, making this procedure simple for users.
Microsoft’s use of Windows Hello for Business spread across more than 100,000 devices running on Windows 10. They utilized present infrastructure such as Intune, System Center Configuration Manager, Public Key Infrastructure, and Azure Active Directory.
This large-scale use demonstrates Microsoft’s dedication to improving security without causing difficulty for users.
Enrollment of users can happen in different ways, depending on the scenario. Some might need a smart card or multi-factor authentication for creating PINs.
The system can handle several enrollment scenarios, such as on-premises Active Directory domain-joined devices and Microsoft Azure AD-joined devices managed by Microsoft Intune.
The physical structure and server tasks necessary to activate “Windows Hello” as a company credential are detailed. They include elements like a Microsoft Azure AD subscription, Microsoft Intune for enrolling devices, AD FS handling federated identities, etc.
This complex arrangement ensures that all parts of the process verifying user identity are secure and effective.
Establishing policies for Windows Hello for Business requires setting up domain-based Group Policies on devices joined to a Windows 10 domain and Intune policies on non-domain-joined devices. These policies help you specify the complexity and length of PINs and control whether Windows Hello is enabled.
The user experience should be easy to use and understand. For domain-joined computers operating on Windows 10 Anniversary Update or later, Group Policy settings will start the certificate enrollment process and Windows Hello for Business policies.
When users sign in, they are asked to make a PIN, which starts the setup of Windows Hello for Business.
Microsoft’s actions with Windows Hello for Business show its commitment to security and progress. It is using powerful two-factor authentication, which is a big move in ensuring the safety of access to business resources.
This change not only improves security but also makes the experience better for users, showing an important advancement in the battle against online dangers.





User forum
0 messages