Introducing OpenHCL: Microsoft’s new, open source ‘paravisor’ for confidential VMs
There is a new open-source VM on the horizon.
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Microsoft has announced a new open-source paravisor called OpenHCL. It is designed to provide a rich set of virtualization services to confidential and non-confidential virtual machines (VMs) running on confidential computing hardware.
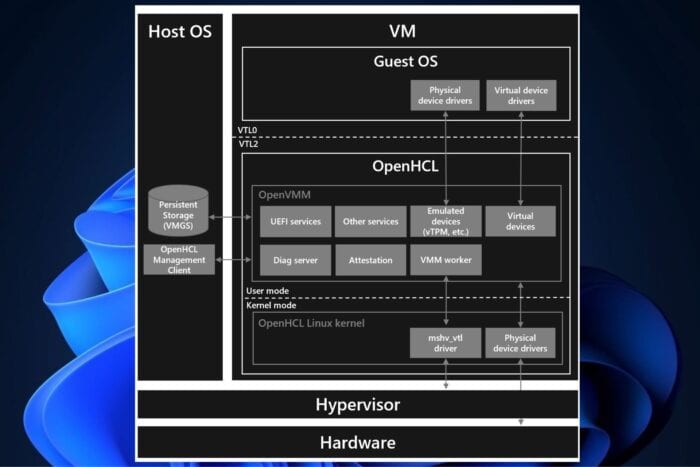
Microsoft’s James Myers explains in a blog post that OpenHCL is a host-independent solution that can run on top of various hypervisors to provide confidential and non-confidential services to VMs. OpenHCL is designed to work with Microsoft’s other OpenVMM-based confidential computing projects or other providers’ projects that are compatible with the OpenVMM API.
The OpenHCL paravisor contains several key components, including a VMM that runs in guest VMs to provide services like device emulation, device translation and diagnostics support. OpenHCL’s VMM is itself powered by a small, customized Linux kernel that’s designed to be lean and mean, with minimal Kconfig to reduce binary size and runtime RAM usage.
The OpenHCL VMM is what provides the rich set of services to a guest. The VMM runs as a collection of processes in VM user mode (VMPL0 or VMPL1) and is higher privileged than the guest OS. The VMM also provides a set of standard interfaces to the guest, allowing the guest to interact with hardware and devices as if it were running natively on the platform in question. This allows VMs to run on top of a paravisor without any guest OS changes.
Since September, OpenHCL has been generally available in Microsoft’s Azure cloud computing service, with the para visor running on over 1.5 million VMs in the past month alone. Microsoft has also started rolling out a new class of confidential VMs in Azure called Azure Boost that use OpenHCL, and the company plans to use OpenHCL in future confidential VM offerings.
To start, OpenHCL is supported on x86-64 and ARM64 platforms, and the paravisor is compatible with Intel TDX and AMD SEV-SNP confidential computing hardware. OpenHCL has a few “core” services that it provides to both confidential and non-confidential VMs. These services include:
- Device emulation: OpenHCL presents standard device interfaces to the OS, allowing existing device drivers to work unchanged. OpenHCL ships with emulated devices (such as a virtual TPM and serial ports) that the VMM and the hardware platform support.
- Device translation: OpenHCL translates hardware interfaces like NVMe to virtualized interfaces, like para-virtualized SCSI, so hardware devices can be assigned directly to VMs without requiring guest OS changes. This enables VMs to take advantage of the performance of modern hardware devices.
- Diagnostics support: OpenHCL provides a set of standard interfaces to the guest that tools can use to inspect the guest environment. This enables debugging and performance analysis of the guest from the host or another VM.
OpenHCL allows VMs running older OS versions to run on confidential computing hardware without requiring the OS to be updated to understand confidential VM features.
The official announcement provides more information, and if you’d like to try it for yourself, OpenHCL is now available on GitHub.




User forum
0 messages