Microsoft Word has become the facilitator of an extremely dangerous phishing scheme
Beware of any suspicious Word documents.
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
A new phishing campaign has been discovered that uses corrupted Microsoft Word documents to evade security software and steal login credentials.
The campaign was discovered by malware-hunting firm Any.Run, pretends to come from payroll and human resources departments and uses a wide range of themes, including employee benefits and bonuses.
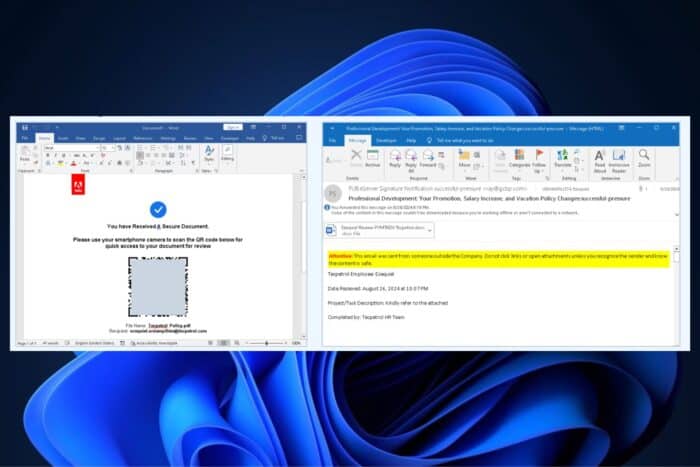
The documents, such as “Annual_Benefits_&Bonus_for[name]IyNURVhUTlVNUkFORE9NNDUjIw_.docx,” are intentionally corrupted and include a base64 encoded string that decodes to “##TEXTNUMRANDOM45##.”
When opened, Microsoft Word detects that the file is corrupted but still recovers the text. The recovered document states that the file is inaccessible, and the target should scan a QR code to retrieve it.
These documents are branded with the logos of the targeted company and contain images of employees, making them appear more legitimate.
Scanning the QR code will bring you to a false site that pretends to be a Microsoft login, and it will successfully steal your credentials there.
The phishing attack’s goal is not news. However, its use of corrupted Word documents is a novel tactic to evade detection.
It’s also worth noting that a Microsoft Word document does not contain malicious code but a QR code that sends the user to a credential-gathering phishing site.
What should you do, then? Simple. Before opening any suspicious email containing attachments (like the recent sextortion emails from Microsoft), an admin must delete or validate it.



User forum
0 messages