Microsoft's Patch Tuesday January updates address 8 zero-day vulnerabilities from a total of 159 CVEs
Three new zero-day vulnerabilities were discovered
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
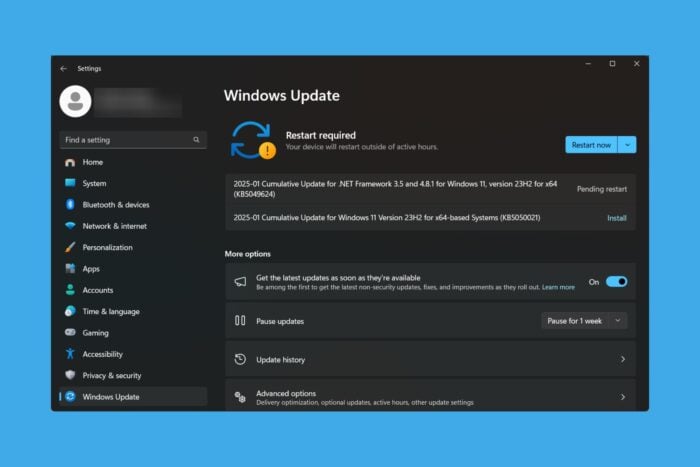
Microsoft issued the first security updates for Windows, that include the KB5050009 patch for Windows 11 version 24H2 and the KB5050021 patch for Windows 11 23H2 and 22H2.
The new updates fix 159 vulnerabilities out of which 8 are zero-day possible threats. The bad news is that 3 of them were already exploited in attacks and concern elevation of privileges.
The most dangerous Windows vulnerabilities in January
The most dangerous vulnerabilities are CVE-2025-21333, CVE-2025-2133, and CVE-2025-21335, which involve elevation of privilege within Windows Hyper-V NT Kernel Integration VSP. Microsoft says that the vulnerabilities were exploited by attackers to gain system privileges on Windows 10, 11 and Windows Server 2025.
Another important flaw was detected for the Windows App Package Installer. It’s a zero-day threat addressed by the CVE-2025-21275 vulnerability report. Attackers could have gained system privileges through elevation of privileges on this component. Luckily, the vulnerability was not exploited.
You should also be careful when changing the themes in Windows because there was also discovered a Windows Themes Spoofing vulnerability code named CVE-2025-21308. Here’s how Microsoft’s advisory describes this flaw:
An attacker would have to convince the user to load a malicious file onto a vulnerable system, typically by way of an enticement in an Email or Instant Messenger message, and then convince the user to manipulate the specially crafted file, but not necessarily click or open the malicious file.
In a few words, just by loading a attacker modified theme in Windows Explorer that uses the Wallpaper or BrandImage options, you could have given them privileges to your system.
When a Theme file is viewed in Windows Explorer and utilizes BrandImage and Wallpaper options that specify a network file path, Windows automatically sends authentication requests to the remote host, including the logged-in user’s NTLM credentials.
Other three important vulnerabilities implied a Microsoft Access remote code execution vulnerability. CVE-2025-21186, CVE-2025-21366, CVE-2025-21395 address the same problem concerning malicious Microsoft Access documents.
This is more of a phishing situation because the attacker needs local access on the computer by manipulating the recipient to use the malicious file. Basically, if you received files named accdb, accde, accdw, accdt, accda, accdr or accdu, Microsoft blocked the execution for them to fix the problem.
If you were targeted by this Microsoft Access exploitation, you might have received a notification indicating that an email contained a blocked extension.
Zero Day Initiative also reports about other software developers patching their software as well. For instance, Adobe addressed 14 CVEs in Photoshop, Substance 3D Stager, Illustrator on iPad, Substance 3D Designer and Animate. Cisco, Ivanti, Moxa and even GitHub released security updates for their software.
The list of vulnerabilities is one of the longest from Microsoft, so we definitely recommend installing the January Patch Tuesday updates as soon as they are available for your system. You can do that by going to Settings > Windows Update or by manually downloading and installing them from the Microsoft Update Catalog by searching for KB5050009 or KB5050021.
If you have any questions or information requests, refer to the comments section below and leave us a note.

User forum
0 messages