5 Best Cyber-Security Tools For Complete Network Protection
Cyber-security software can protect all your network environment
6 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Cyber security software is extremely important if you want to protect your network environment.
- The tools below offer all the features necessary for endpoint management and protection.
- Some of them have antivirus and backup capabilities while others provide complete control over all devices.
Regarding your network environment, there is no effort spared for its protection. Luckily there are some powerful cyber-security solutions out there that can help you with all the tools you need for that.
In this article, you will find the best software tailored to any enterprise size and network.
How can cyber-security solutions protect my network?
Managing a small network makes it relatively easy to check on each asset individually. However, when you’re dealing with over 10 endpoints and other servers and equipment, things can get complicated.
Whether you need on-premise or cloud protection, patching your systems, or simply ensuring authorized entries, you need a network cyber-security tool to manage the workload.
We recommend reading our article about cyberattack statistics to get the complete picture of the threats you are facing.
With such management tools, you can automate all security events seamlessly from a single console.
What are the best network cyber-security solutions?
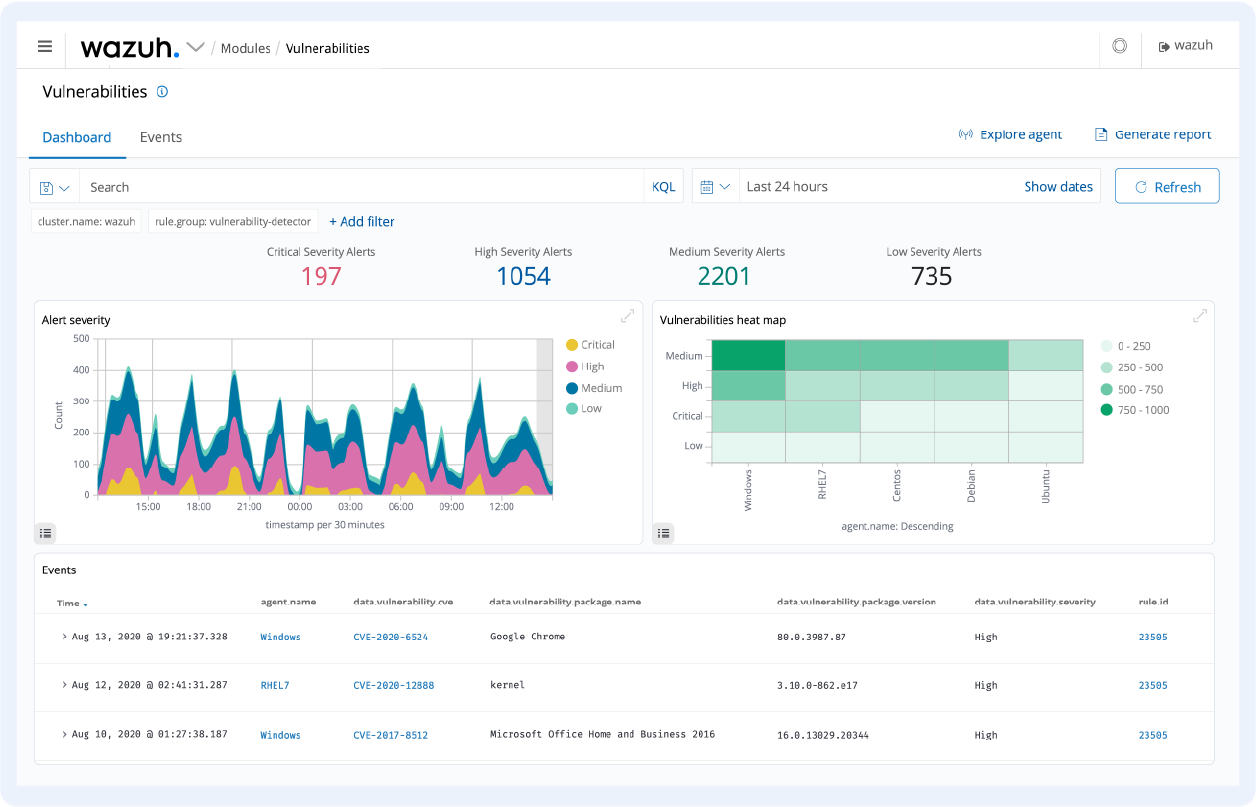
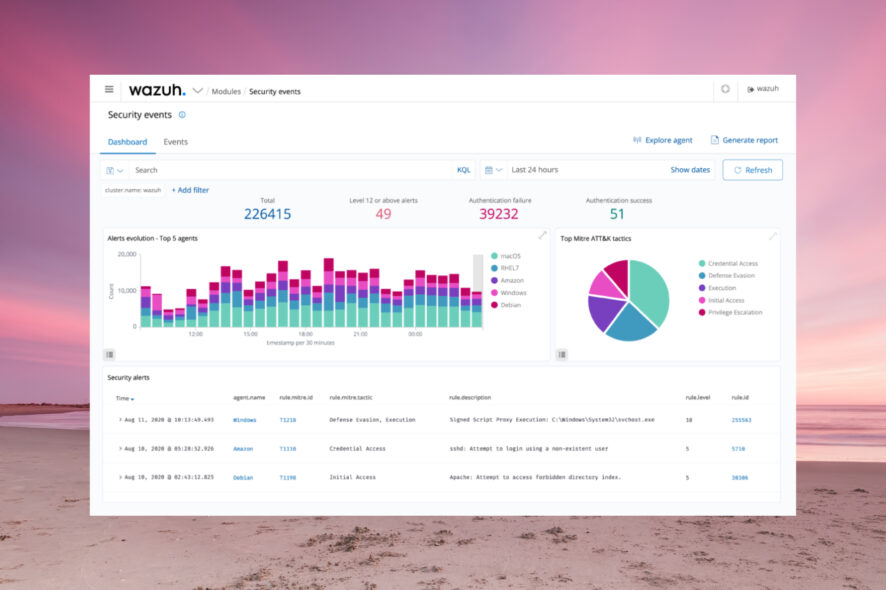
Wazuh – The best network vulnerability detection
Wazuh has lightweight agents for Windows, Linux, macOS, Solaris, AIX, and HP-UX systems that detect any unusual or rule-breaking behavior on the system.
That includes cloaked processes, hidden files, unregistered network listeners, and many more security issues.
After it gathers information from the system and app logs, the software sends the data to a central manager to be analyzed and stored.
The apps and files are monitored constantly to detect any configuration or attribute changes and to supervise compliance with the security policies you have enforced.
After detecting such problems, Wazuh can block access to a system, execute predetermined commands, or make further queries on the affected systems.
The software is open source, so you can modify it to your needs, but it also supports a wide array of integrations such as AlienVault, Amazon Macie, VirusTotal, and a lot more.
Let’s review some of its best features below:
- Ready-made Windows, Linux macOS, Solaris, AIX, and HP-UX systems agents
- Advanced threat intelligence technology
- Web user interface for data visualization, analysis, and platform management
- Cloud and Container security, including Docker hosts and Kubernetes nodes and down to the container level itself
- Extensive reports for compliance, vulnerability, and file integrity
- It protects public clouds, private clouds, and on-premise data centers

Wazuh
Get complete endpoints and cloud workloads protection from an open-source tool with many integrations.Acronis Cyber Protect – Extensive network security features
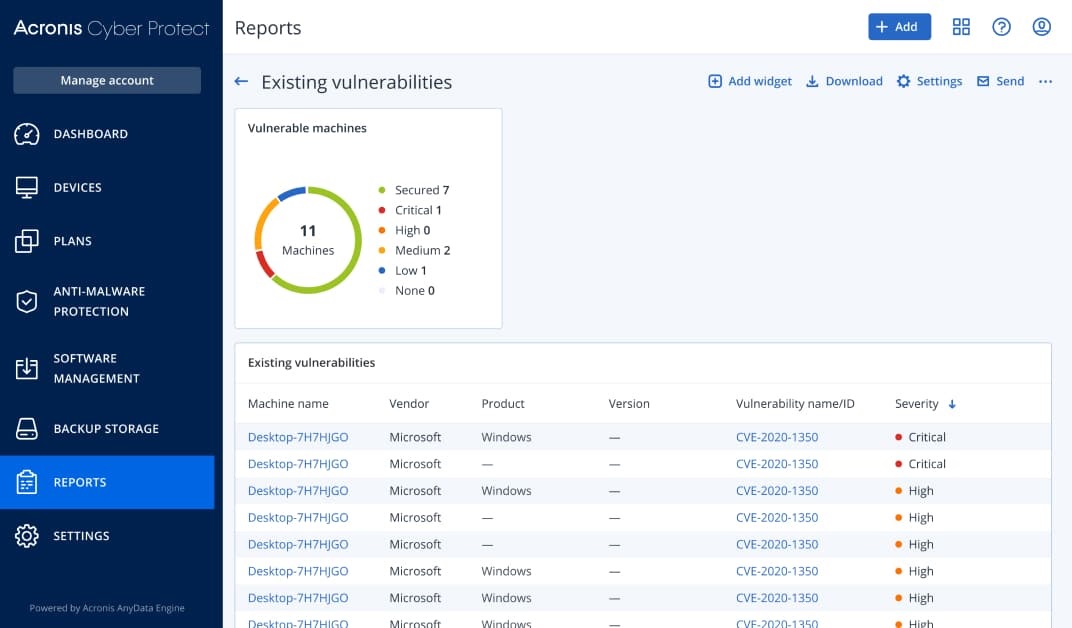
Acronis Cyber Protect is more than fit for this purpose if you’re looking for backup and anti-malware for all your devices.
It comes with AI-based ransomware protection and integrated patch management tools, so you don’t need to worry about any loopholes in your systems.
The solution can also provide vulnerability assessment and will allow your network manager to control the endpoints remotely.
Therefore, you will have full control of all your network environment and assets from a single console and fend off any cyber threats.
Here are just some of the best features of Acronis Cyber Protect:
- Full antivirus and antimalware protection with AI-based ransomware protection
- Integrated patch management and backup
- Intuitive web-based interface with multi-tenant administration
- Remote desktop capabilities
- Multi-level encryption

Acronis Cyber Protect
Acronis Cyber Protect will ensure that all of your enterprise data is safe from both internal and external threats!Security Event Manager – Great log monitoring
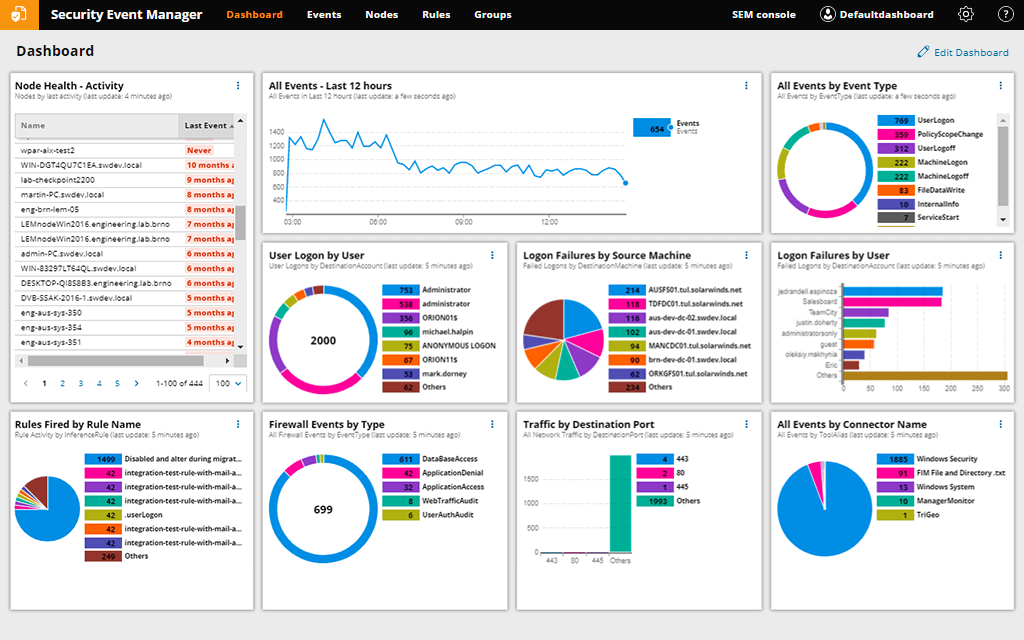
Detecting failed logons and firewall events is a big part of network security and Security Event Manager covers that area very well.
It comes with hundreds of pre-built connectors that gather logs from various sources, compiles their data, and gathers them in a central location for you to investigate potential threats, prepare for audits, and store logs.
Basically you can create any network or user-based rules and program the too to respond accordingly.
For instance, you can respond immediately by blocking IPs, changing privileges, disabling accounts, blocking USB devices, terminating applications, and a lot more.
Here are some of its key features:
- Advanced pfSense firewall log analyzer
- Keep track of logon and logoff events with a centralized monitor
- Advanced compliance reporting with predefined templates for PCI DSS, HIPAA, SOX, and more
- Cross site scripting prevention tool
- Blocks IPs, change privileges, disable accounts, block USB devices, and more
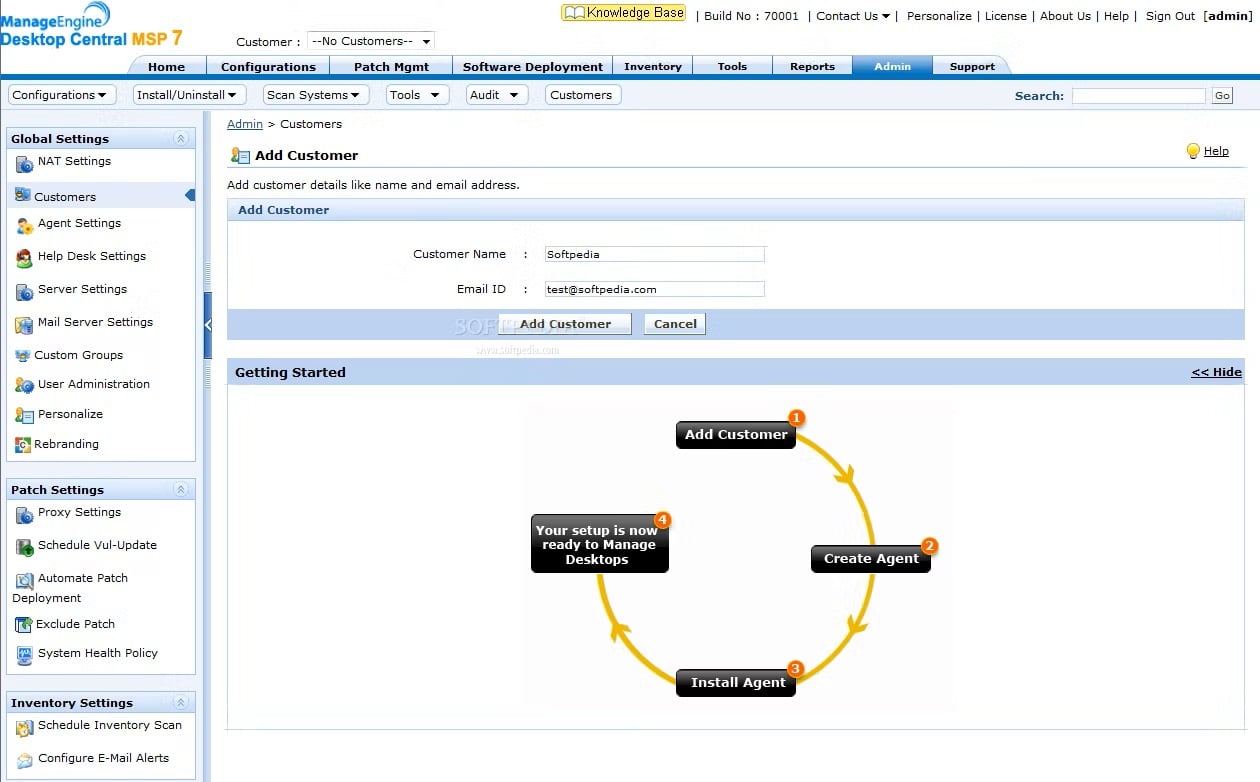
Endpoint Central MSP – Great patch management system
Endpoint Central MSP is a holistic endpoint management software for MSPs that helps you administrate desktops, servers, laptops, and mobile devices from a central location.
This tool comes with 50 pre-defined configurations and over 100s of scripts that will allow you to manage any and all types of customer environments.
You will be able to track granular asset data for hardware and software and pull critical information including usage statistics, blacklisted applications, warranty, licenses, etc.
And if you need to cater to a specific endpoint, you can do so with remote desktop features that include video and audio call support, file transfer, shortcuts, session recording, and more.
Here are some of its key features:
- Automate patch deployment for over 850 first and third-party applications
- Remotely deploy applications to client computers
- Manage Windows, servers, Android, iOS, and Chrome devices
- Manage up to 25 endpoints with the free version
- Restrict and control the usage of USB devices

Endpoint Central MSP
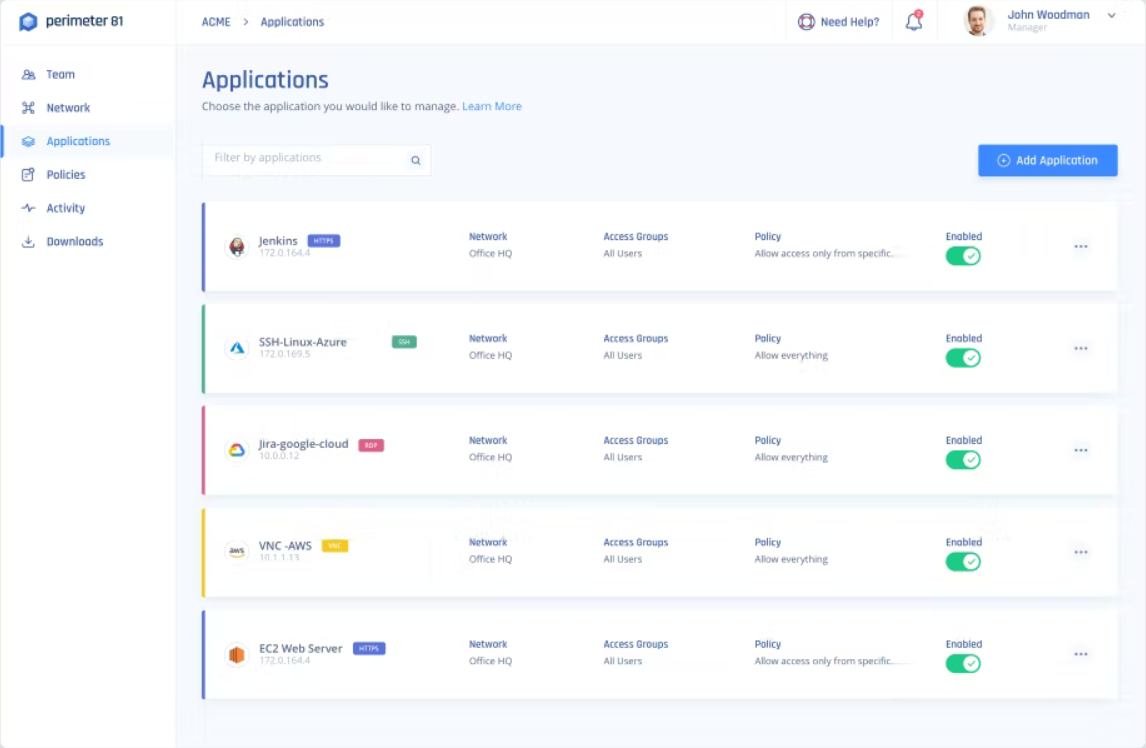
Manage your endpoints securely and provide backup and patching to all network devices.Perimeter 81 – Great network VPN
Perimeter 81 is an enterprise-level security platform you can use to monitor all traffic and network activity.
The tool comes with a Software-Defined Perimeter that allows you to restrict network access and provide secure channels to the shared systems.
With multi-layered security tools, including always-on encryption, two-factor authentication, and single sign-on, Perimeter 81 prevents data loss and unauthorized access to your network.
The devices are verified before accessing the network and the resources within, which translates to increased security.
Perimeter 81 is also a cloud-based VPN solution that is scalable to your growing network.
Check out these Perimeter 81 main features:
- Secure remote access
- OpenVPN, L2TP, IKEv2, and PPTP security protocols
- Integration with all major cloud services and on-prem resources
- Compatible with all major platforms, including Windows, Mac OS, iOS, and Android
- 30-day money-back guaranteed policy

Perimeter 81
Secure your network with this professional enterprise VPN solution.This concludes our list of the best network cyber-security tools for enterprise networks. While some of them focus on vulnerability detection, others come with active protection and backup.
All you need to do is to assess the needed level of security and features to make the right decision.
You might also be interested in our selection of the best enterprise cybersecurity tools in terms of antivirus and backup features.
Have you decided on a solution from our list? Tell us how you made your decision in the comments section below.