What is Event ID 4769 & How to Fix It?
Change your authentication level to a more secure encryption type
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- A security alert on your Windows server should be treated as urgent and dealt with immediately.
- The Event ID 4769 is one such issue and indicates the presence of a malicious entity or a brute-force attack.
- You can elevate your authentication level to prevent such issues from occurring in the future.
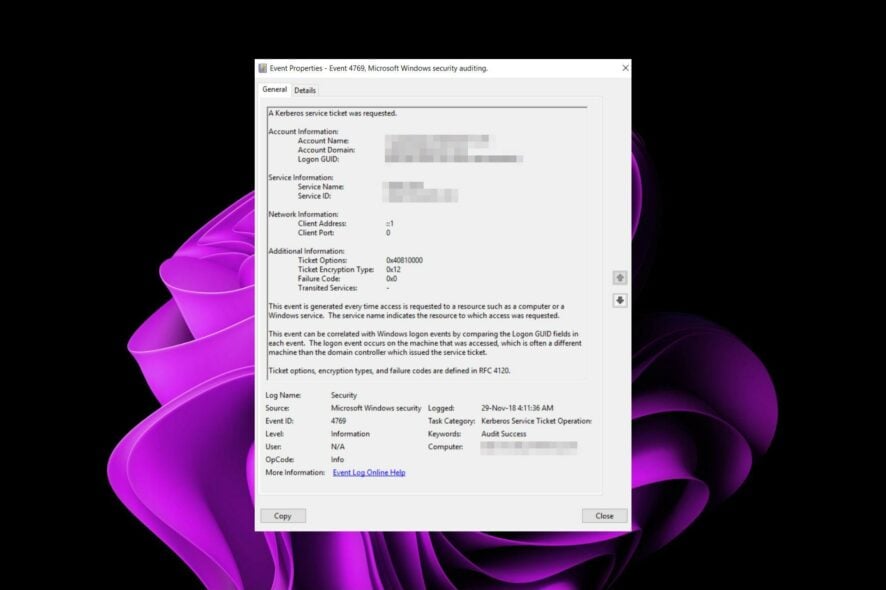
The Event ID 4769 Kerberoasting is a security alert. This event can be used to detect the presence of malicious users who are attempting to use Kerberos to impersonate another user or service.
It is generated every time a DC is contacted to validate the security token. The Kerberos authentication protocol is used to prove the identity of a client who wants to access a network resource on behalf of an end user. So, if you spot this particular Event ID, here is what you should do.
What causes the Event ID 4769?
This event indicates that the server attempted to request a Kerberos service ticket for the user account specified in the Event ID. Usually, the user’s security token was sent to a domain controller (DC) for validation.
This can happen because the requested user account is not in the domain or because of an error in the KDC database. Other reasons include:
- Server has an expired database entry – This event is logged when a client tries to connect to a server using Kerberos authentication. The KDC cannot verify that it is still in possession of a valid TGT ticket for the client.
- Client has an expired entry in the database – When a client’s entry has expired, Kerberos failure audit Event ID 4769 0x17 will be recorded. This happens when a client computer cannot renew its ticket-granting ticket (TGT).
- Multiple entries – A Kerberos ticket is generated for each principal to identify the user (or service) when they connect to other computers on the network. This ticket contains information about what services they can use and what they have access to after they log in.
- Unsupported protocol version – When a client tries to connect to a server using an old protocol version, the Kerberos failure audit event 4769 is logged in. The server will reject the login attempt because the client may be using an outdated version of Kerberos. It’s also possible that the user is attempting to log in with a compromised account.
- Weak passwords – An Event ID 4769 Kerberoasting occurs when a malicious entity obtains and uses the victim’s Kerberos tickets. A user may be performing a brute-force attack on the service principal names of a domain controller or was able to obtain and decrypt the target’s encrypted ticket-granting ticket (TGT).
How can I fix Event ID 4769?
1. Raise the authentication level
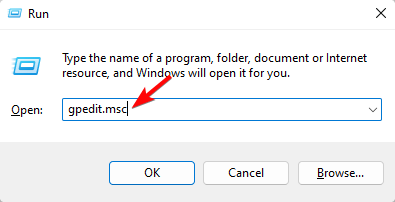
- Hit the Windows + R keys to open the Run command.
- Type gpedit.msc in the dialog box and hit Enter to open the Group Policy Editor.
- Navigate to the following location:
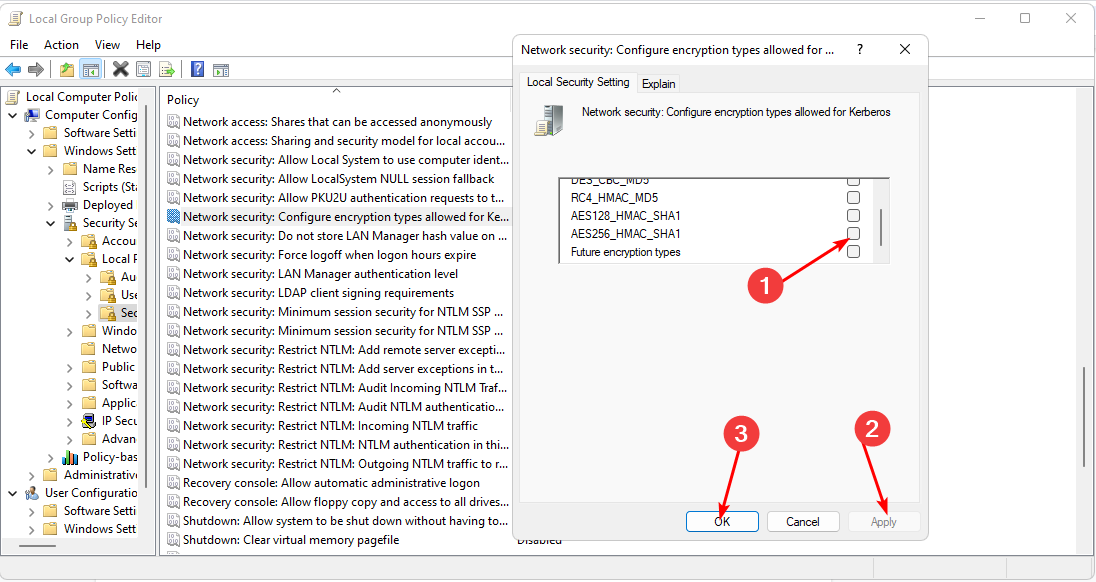
Computer Configuration/Windows Settings/ Security Settings/Local Policies/Security Options - Locate Network security: Configure encryption types allowed for Kerberos and double-click on it.
- Under the Local Security Settings tab, select AES256_HMAC_SHA1, then select Apply and OK.
It is important to change the Event ID 4769 ticket encryption type. This is because the authentication level of your encryption algorithm determines the strength of your password. The stronger the password, the more difficult it is for someone to hack into your online accounts.
2. Enable auditing
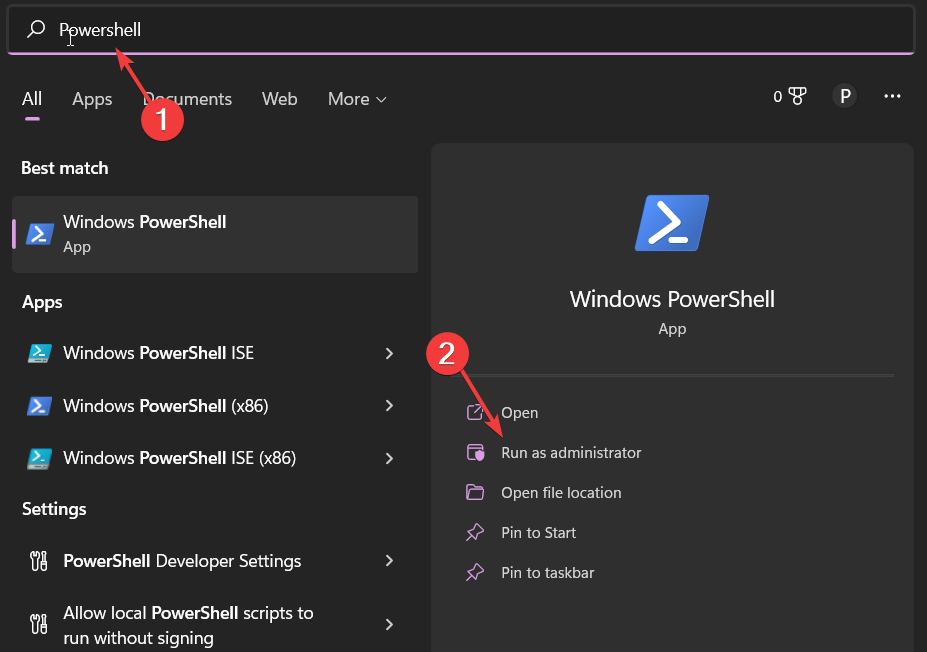
- Hit the Windows key, type Powershell in the search bar, and click Run as administrator.
- Type the following command and hit Enter:
auditpol /set /subcategory:”logon” /failure:enable
If you have enabled Kerberos auditing, you can see this event. When unauthorized users attempt to log in, you’ll get a notification. It will also list the error code for users trying to obtain tickets using the credentials of other users or services in your environment.
You can then take the necessary steps to block the users. This is especially important for the Event ID 4769 failure code 0x1b. Such errors can be hard to detect as they do not pass through client-server authentication.
3. Reset Kerberos password
Kerberoasting is a technique to harvest Kerberos tickets from Windows domain controllers. It’s one of the most effective ways to gain elevated privileges in a domain environment.
To resolve this issue, you must reset the user’s password in Active Directory Users and Computers (ADUC). Usually, these are privileges exclusive to the administrator, so you need to get in touch and request a password reset.
You may also encounter the Event ID 4771 error where Kerberos pre-authentication has failed, so don’t hesitate to check out our guide for more.
Let us know if you have been able to solve this error in the comment section below.



User forum
0 messages