Here are the new Microsoft Entra recommendations for a healthy and secure system
Microsoft also added new recommendations to Entra's Identity Secure Score.
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Microsoft added new recommendations to its Entra platform, and the Redmond-based tech giant agrees that these will be keeping systems healthy and secure for thousands of customers.
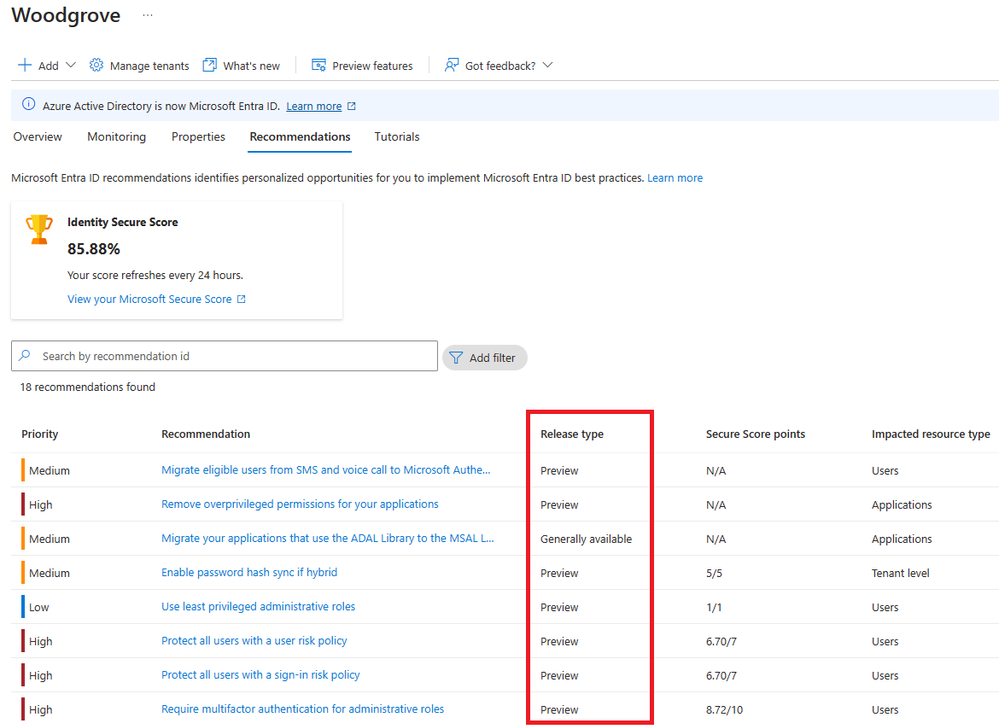
Alongside the new recommendations, Microsoft also made changes to its Identity Secure Score, which functions as an indicator for how aligned you are with Microsoft’s recommendations for security, according to the official blog post.
Today, we’re thrilled to announce the upcoming general availability of four recommendations, and another three recommendations in public preview. We’re also excited to share new updates on Identity secure score. These recommendations cover a wide spectrum, including credentials, application health, and broader security settings—equipping you to safeguard your digital estate effectively.
Microsoft
There are the new Microsoft Entra recommendations:
- Remove unused credentials from applications
- Renew expiring service principal credentials
- Renew expiring application credentials
- Remove unused applications
- Migrate applications from the retiring Azure AD Graph APIs to Microsoft Graph
- Migrate Service Principals from the retiring Azure AD Graph APIs to Microsoft Graph
Regarding the Identity Secure Score, Microsoft updated it with a new recommendation, now in public preview:
- Protect your tenant with Insider Risk policy: Implementing a Conditional Access policy that blocks access to resources for high-risk internal users is of high priority due to its critical role in proactively enhancing security, mitigating insider threats, and safeguarding sensitive data in real-time.
However, the Identity Secure Score also has the following recommendations that users should take into account to ensure their organization’s infrastructure remains safe and secure.
- Enable password hash sync if hybrid
- Protect all users with a user risk policy
- Protect all users with a sign-in risk policy
- Use least privileged administrative roles
- Require multifactor authentication for administrative roles
- Ensure all users can complete MFA
- Enable policy to block legacy authentication
- Designate more than one Global Admin
- Do not expire passwords
- Enable self-service password reset
- Do not allow users to grant consent to unreliable applications
These new recommendations came days after Microsoft Entra caused a bit of controversy in Europe, due to unfair business practices.



User forum
0 messages