Install KB5037768 to patch the PLUGScheduler vulnerability in Windows 10
Upon exploitation, the vunerability grants threat actors the SYSTEM privileges
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Microsoft has flagged a PLUGScheduler security vulnerability (CVE-2024-26238), which allows threat actors to gain access to the affected system.
Titled Microsoft PLUGScheduler Scheduled Task Elevation of Privilege Vulnerability, it was reported to Microsoft by Synacktiv. The latter has a dedicated page detailing the vulnerability and its effect on Windows 10 devices. The issue’s description reads,
The PLUGScheduler.exe binary performs file operations such as deletion and renaming as SYSTEM, in a directory where standard users have partial control. This leads to arbitrary file write as SYSTEM.
This vulnerability is an arbitrary file write. It can be used to execute code as SYSTEM by writing a DLL file in C:\Windows\System32\SprintCSP.dll and triggering the SvcRebootToFlashingMode method of the StorSvc service.
The vulnerability was first reported on Jan 22, 2024, acknowledged by MSRC (Microsoft Security Response Center) on Feb 1, 2024, and a patch for it was released on May 14, 2024, alongside the KB5037768 update. Microsoft has assigned the PLUGScheduler vulnerability a severity rating of Important!
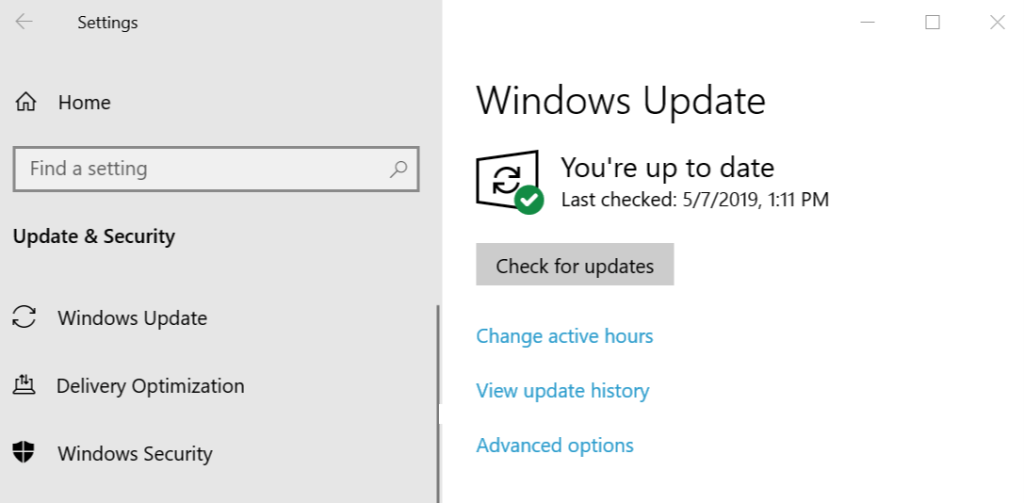
To patch the CVE-2024-26238 vulnerability, open the Settings app > go to Update & Security > click on Check for updates > install KB5037768 > then restart the PC for the changes to come into effect.
When we checked, several users were facing installation issues with KB5037768, but these are easily fixable with a few quick workarounds. You can also manually download KB5037768 from the Microsoft Update Catalog!
Besides, several critical threats to Windows 10 devices have been identified in the recent past, including the ShrinkLocker ransomware. And given the fact that Windows 10 will be out of support in less than 18 months, questions arise about the future course.
On our part, we picked out the most viable upgrade options for Windows 10 users that would boost overall security and privacy.
Do you know more about the PLUGScheduler vulnerability? If so, share it with our readers in the comments section.