MysterySnail exploit creates havoc on Windows systems
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- The MysterySnail zero-day exploit negatively impacts Windows Clients and Server Versions.
- IT companies, Military and Defense organizations were among the parties most affected by the malware.
- IronHusky was behind the attack on the servers.
According to security researchers, using a zero-day elevation privilege exploit, Chinese hackers have been able to attack IT companies and defense contractors.
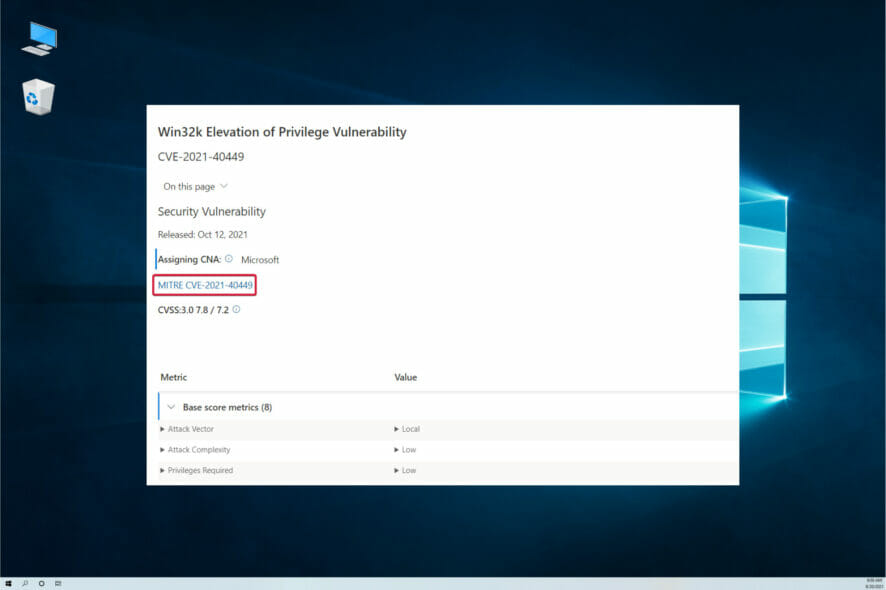
Based on the information gathered by Kaspersky researchers, an APT group was able to leverage a zero-day vulnerability in the Windows Win32K kernel driver in the development of a new RAT trojan.
The zero-day exploit had plenty of debug strings from the previous version, the CVE-2016-3309 vulnerability. Between August and September 2021, a couple of Microsoft servers were attacked by MysterySnail.
The Command and Control (C&C) infrastructure is quite similar to the discovered code. It is from this premise that researchers were able to link the attacks to the IronHusky hacker group.
Upon further research, it was established that variants of the exploit were being used in large-scale campaigns. This was mainly against the military and defense organizations as well as IT companies.
The security analyst reiterates the same sentiments shared by researchers from Kaspersky below on the threats posed by IronHusky to large entities using the malware.
MysterySnail attack
MysterySnail RAT was developed to affect Windows clients and server versions, specifically from Windows 7 and the Windows Server 2008 up to the latest versions.
This includes Windows 11 and Windows Server 2022. According to reports from Kaspersky, the exploit mainly targets Windows client versions. Nevertheless, it was predominantly found on Windows Server Systems.
Based on the information gathered by researchers, this vulnerability stems from the ability to set user-mode callbacks and execute unexpected API functions during the implementation of these callbacks.
According to researchers, executing the ResetDC function a second time triggers the bug. This is for the same handle during the execution of its callback.
Were you affected by the MysterySnail zero-day exploit? Let us know in the comment section below.