Microsoft Defender XDR's new AI features will block malicious OAuth apps
It can block attacks in less than three minutes
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

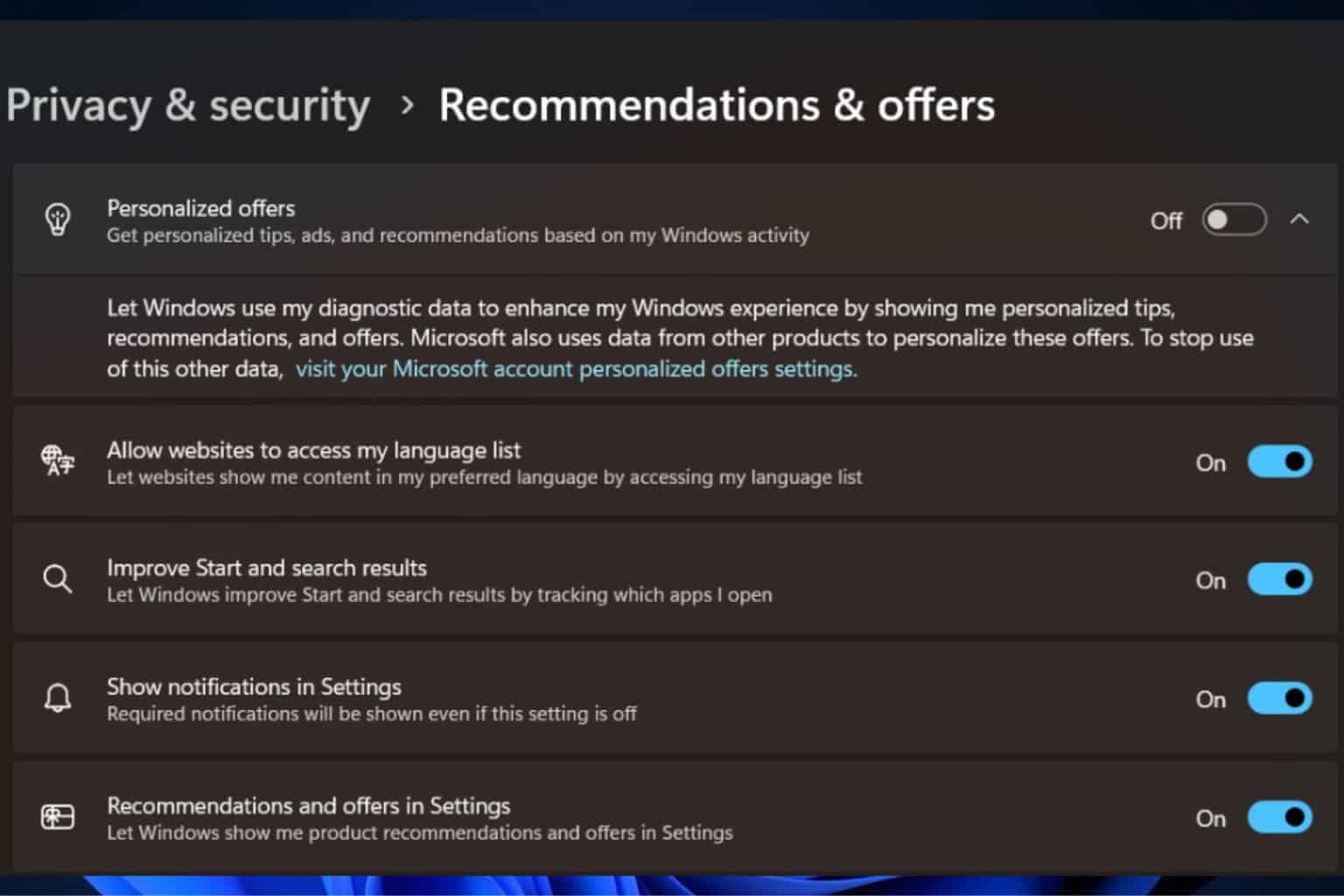
Threat actors are increasing their efforts to hack into cloud-based systems and applications. Some of their campaigns are using malicious OAuth apps. Thus, Microsoft improved its Defender XDR with automated attack disruption capabilities to prevent intrusion attempts.
OAuth, long-form Open Authentication standard, applications allow you to log on to multiple accounts without requiring your credentials every time. Also, you can use them to protect your data. Thus, the new features will block malicious OAuth apps with the help of AI and machine learning.
How does the automated attack disruption work?
The automated attack disruption feature of the Defender XDR operates by correlating signals from many sources into a single incident. According to Microsoft, the feature uses insights from endpoints, identities, email and collaboration tools, and SaaS apps. On top of that, it identifies assets controlled by the attacker. Afterward, it uses relevant Microsoft Defender products to isolate the attack and affected assets.
The new automated attack disruption capabilities of Defender XDR prevent hackers from further exploitations. As a result, they won’t be able to access your data. Also, according to Dark Reading, the Microsoft XDR can stop ransomware, business email compromise, and credential-stuffing attacks in less than three minutes.
How do hackers use malicious OAuth apps?
Cybercriminals can access your account and retain access to various applications if you enter your credentials on malicious OAuth apps. However, you can prevent their attacks with defense suites like Defender XDR.
Unfortunately, wrongdoers can also use corrupted OAuth apps to gain control over your system. After all, they can create, modify, and grant broad privilege access using the breached user accounts for Microsoft cloud services.
In addition, if you lack strong authentication measures like MFAs, threat actors could use phishing and password-spraying attacks. On top of that, with elevated permissions, they could launch various spam campaigns.
Microsoft added more protections and features to the Defender XDR to deal with other issues. For example, now, the platform has native protections for operational technology (OT) and industrial control systems (ICS). Thus, defenders can deal with OT system threats and verify their ICSes directly from the Defender XDR portal.
In a nutshell, Microsoft keeps enchanting its security systems with AI features. Also, the Defender XDR can protect you from malicious OAuth apps and other malware. On top of that, AI technologies are faster than classic methods and can defend you in real-time. So, their development is crucial since hackers can perform a complete attack chain in two hours.
What are your thoughts? Are you using Defender XDR or an alternative? Let us know in the comments.