Microsoft Mail users targetted in new phishing campaign
4 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Online safety is only relative, an illusion in the eyes of many security experts.
- Cybersecurity firm Zscaler pulled the covers off a new AiTM phishing campaign.
- The targets are Microsoft Mail users, and we're about to show you how it works.

Read very carefully what we’re about to write in this article, as nobody is safe from attackers and the methods they are presently using.
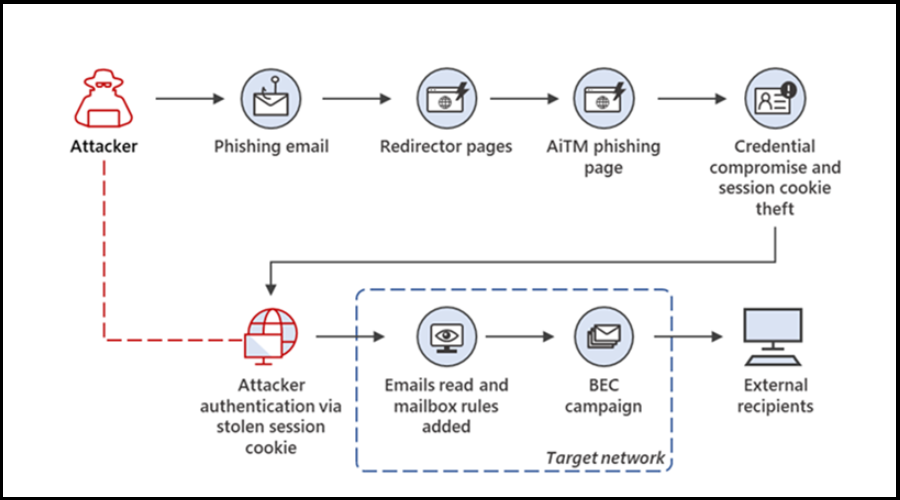
To be more specific, Microsoft email service users need to really be on the lookout because Zscaler, a cybersecurity research company, just discovered a new ongoing phishing campaign targeting Microsoft email users.
Not to scare you but, according to the firm, corporate users are under attack and the campaign is being run using adversary-in-the-middle (AiTM) technique to bypass multi-factor authentication.
Phishing campaign uses AiTM method to steal your credentials
Even the Redmond tech giant acknowledged this problem back in July when it created a blog post meant to warn users about the impending danger.
To bring you up to speed, this AiTM technique places an adversary in the middle in order to intercept the authentication process between the client and the server.
Needless to say that, during this exchange, all of your credentials are as good as gone, as malicious third parties will have them as a result.
And, as you would have expected, this also means the MFA information is stolen. Therefore, the adversary in the middle acts like the server to the real client and the client to the real server.
| Attacker-registered domain name | Legit Federal Credit Union domain name |
| crossvalleyfcv[.]org | crossvalleyfcu[.]org |
| triboro-fcv[.]org | triboro-fcu[.]org |
| cityfederalcv[.]com | cityfederalcu[.]com |
| portconnfcuu[.]com | portconnfcu[.]com |
| oufcv[.]com | oufcu[.]com |
As the security experts explained, this campaign is specifically designed to reach end users in enterprises that use Microsoft’s email services.
Remember that Business email compromise (BEC) continues to be an ever-present threat to organizations and this campaign further highlights the need to protect against such attacks.
These are some of the key points that cybersecurity experts have summarized, as a result of analyzing the threat at hand:
- Corporate users of Microsoft’s email services are the main targets of this large-scale phishing campaign.
- All these phishing attacks begin with an email sent to the victim with a malicious link.
- The campaign is active at the time of blog publication and new phishing domains are registered almost every day by the threat actor.
- In some cases, the business emails of executives were compromised using this phishing attack and later used to send further phishing emails as part of the same campaign.
- Some of the key industry verticals such as FinTech, Lending, Insurance, Energy and Manufacturing in geographical regions such as the US, UK, New Zealand and Australia are targeted.
- A custom proxy-based phishing kit capable of bypassing multi-factor authentication (MFA) is used in these attacks.
- Various cloaking and browser fingerprinting techniques are leveraged by the threat actor to bypass automated URL analysis systems.
- Numerous URL redirection methods are used to evade corporate email URL analysis solutions.
- Legitimate online code editing services such as CodeSandbox and Glitch are abused to increase the shelf life of the campaign.
Per our analysis of the original emails using the Federal Credit Union theme, we observed an interesting pattern. These emails originated from the email addresses of the chief executives of the respective Federal Credit Union organizations.
Allow us to also mention that some of the attacker-registered domains were typosquatted versions of legit Federal Credit Unions in the US.
Nowadays, the line between online safety and compromising your entire operation is so fine, you’d need an atomic microscope to see it.
That’s why we always preach safety, which means:
- Never download anything from random, unsafe sources.
- Never reveal your credentials or other sensitive information to anyone.
- Don’t let people you don’t trust use your PC.
- Don’t open links received in emails that originate from untrusted sources.
- Always antivirus software.
It’s all up to you to stay safe in this everchanging online jungle, so be sure to take all the safety measures you need, in order to avoid disaster.
Have you received any such emails lately? Share your experience with us in the comments section below.

User forum
0 messages