New phishing campaign is after your credentials, Microsoft warns
4 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Microsoft is warning its users and advising them to take immediate action in order to stay protected.
- A new phishing campaign has been discovered by the Microsoft 365 Defender Threat Intelligence Team.
- Attackers combine these links with social engineering baits that impersonate well-known productivity tools.
- To make everything seem normal, hackers use Google reCAPTCHA to block any dynamic scanning attempts.

The Redmond-based tech company issued a warning for all its users, urging them to take appropriate actions in order to stay protected.
Experts have been tracking a widespread credential-phishing campaign that relies on open redirector links, while simultaneously suggesting it can defend against such schemes.
This is just one of multiple such schemes attempted by malicious third parties in the last few months, so we should really take this warning seriously and do everything we can to protect our sensitive data.
Microsoft raises awareness on new phishing attack
Even though redirect links in email messages are a vital tool to take recipients to third-party websites or track click rates and measure the success of sales and marketing campaigns, there are other ways to go as well.
An open redirect is when a web application allows an HTTP parameter to contain a user-supplied URL that causes the HTTP request to be redirected to the referenced resource.
This same technique can be abused by competitors in order to redirect such links to their own infrastructure, at the same time keeping the trusted domain in the full URL intact.
This helps them evade analysis by anti-malware engines, even when users attempt to hover on links to check for any signs of suspicious content.
The Microsoft 365 Defender Threat Intelligence Team developed on this subject and explained how these attacks are conducted, in a detailed blog post.
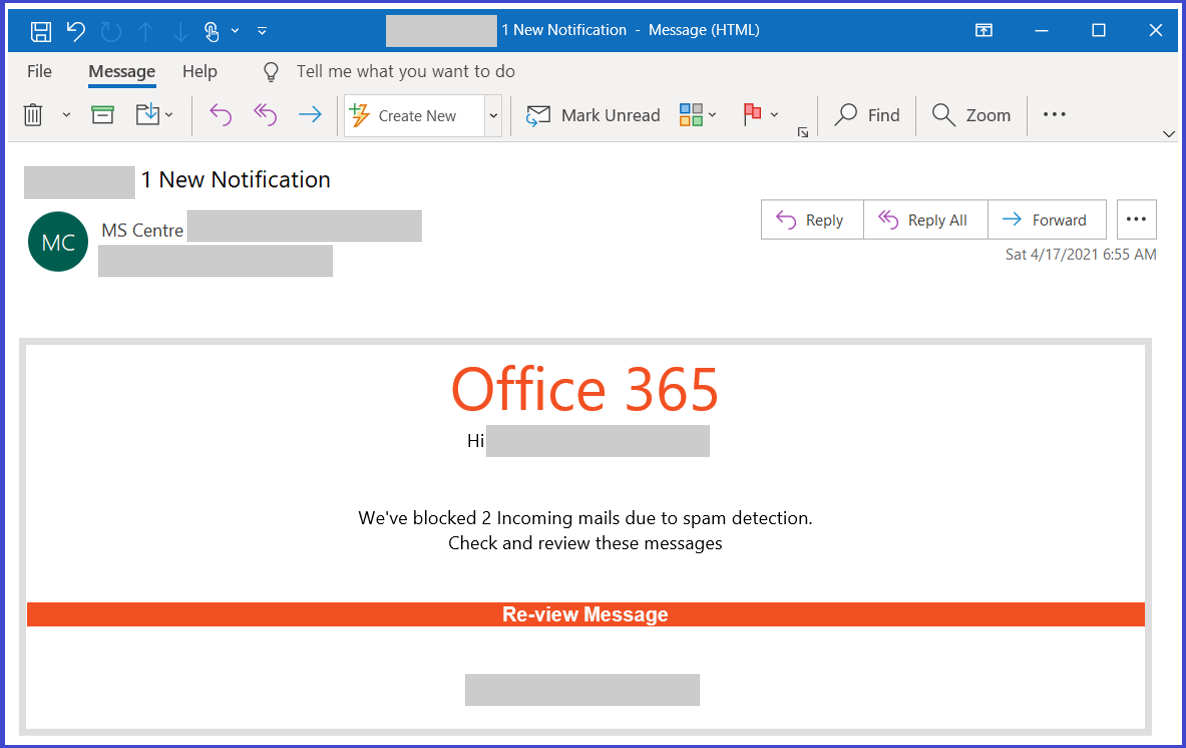
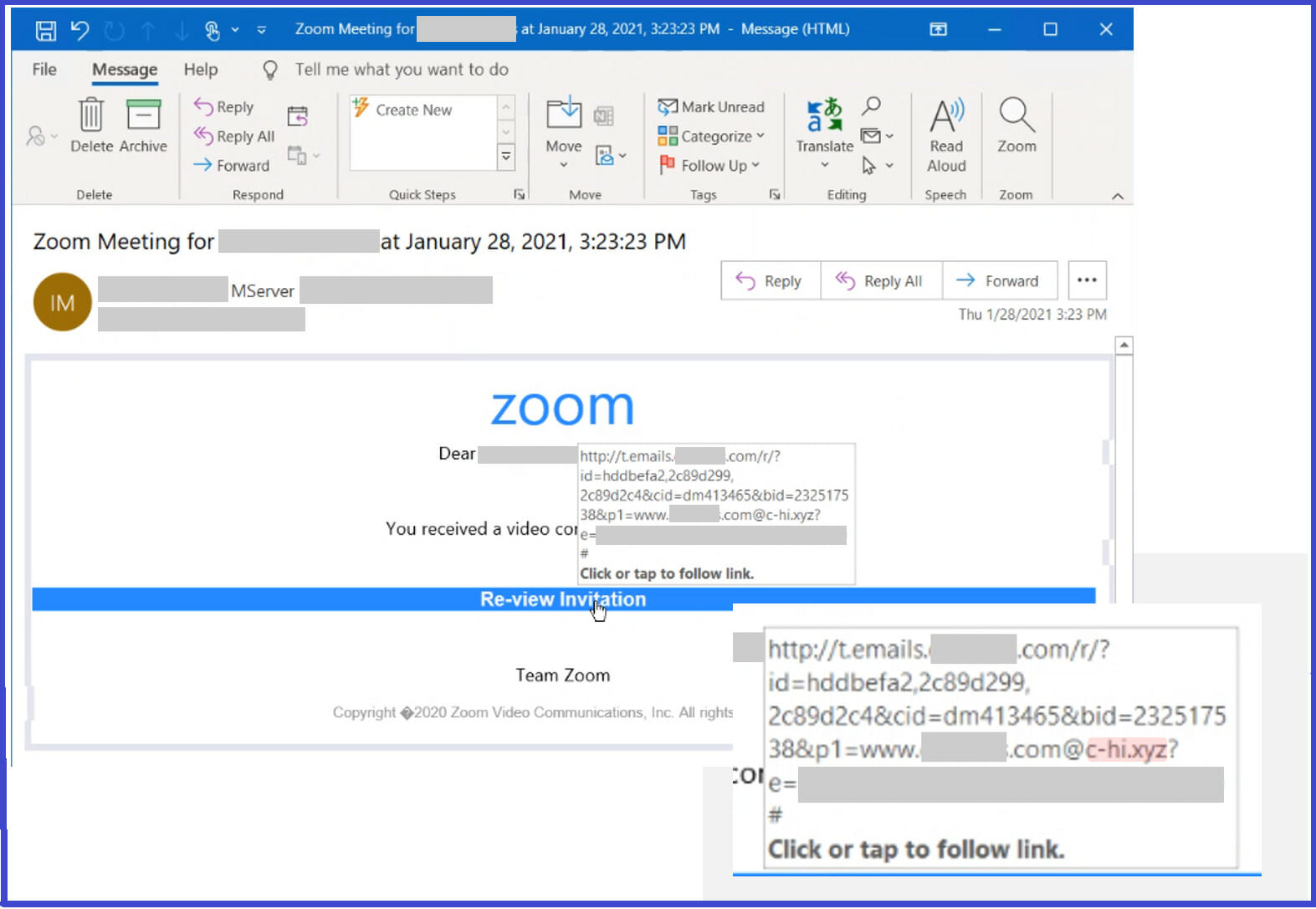
Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking. Doing so leads to a series of redirections — including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems — before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks.
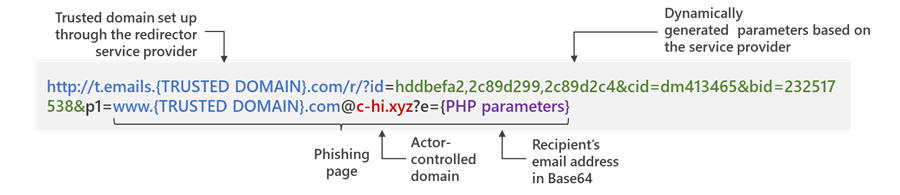
In order to successfully lead potential victims to phishing sites, the redirect URLs embedded in the message are set up using a legitimate service.
In fact, the final actor-controlled domains contained in the link leverage top-level domains .xyz, .club, .shop, and .online, but which are passed as parameters so as to sneak past email gateway solutions.
Microsoft stated that it discovered at least 350 unique phishing domains as part of this hacking campaign.
The most effective tool hackers have is convincing social engineering lures that purport to be notification messages from apps like Office 365 and Zoom, a well-crafted detection evasion technique, and a durable infrastructure to carry out the attacks.
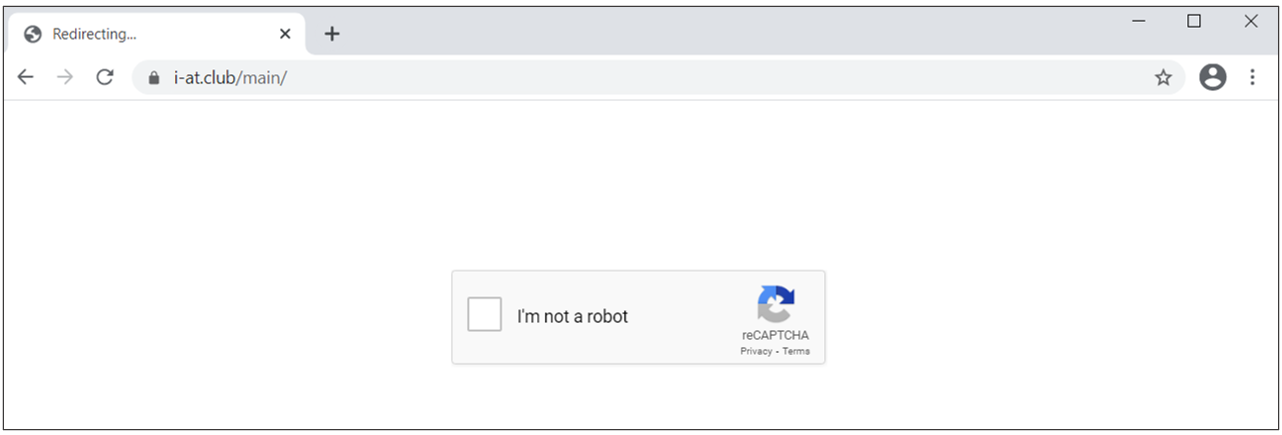
And in order to further bolster the attack’s credibility, clicking the specially-crafted link redirects the users to a malicious landing page that employs Google reCAPTCHA to block any dynamic scanning attempts.
After completing the CAPTCHA verification, the victims are displayed a fraudulent login page mimicking a known service like Microsoft Office 365, only to swipe their passwords upon submitting the information.
If the victim enters a password, the page then refreshes with an error message declaring that the session timed out and directing the visitor to enter the password again.
This is a data validation practice not unlike the double opt-in ritual used by email marketing list services to ensure compliance with spam laws.
Phishing victims get redirected to a legitimate Sophos security website indicating, falsely, that the email message that they were notified to retrieve has been released.
Now that we are aware of the danger, we can go ahead and take immediate appropriate actions, reducing the risk of becoming another statistic in this cyberwar.
Are you doing everything you can to stay protected from phishing attempts? Let us know in the comments section below.







User forum
0 messages