Microsoft reports Dirty Stream vulnerability impacts popular Android apps
The vulnerability was detected in two popular apps with billions of combined downloads
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Researchers at Microsoft have detected a security vulnerability dubbed Dirty Stream in several Android apps. The security research team detected the vulnerability in the filesharing mechanism of several file-sharing Android apps as reported by BleepingComputer.
Vulnerabilities are a boon to cybercriminals and provide an easy pass to target naive users. Given the availability of over 3.5 billion active Android phones globally, preventing them is the need of the hour.
Users are often asked to prevent visiting shady websites or using apps downloaded from unofficial app stores. But, deep down you’d agree that it is the responsibility of the platform owners to protect its users from any frauds.
Microsoft security research team detects ‘Dirty Stream’ vulnerability in two popular Android apps
Talking of responsibility, Microsoft has a dedicated security research team for the same. Security researchers are responsible for detecting and negating possible threats posed by any vulnerabilities.
More recently, security researchers at Microsoft have detected a vulnerability in the filesharing mechanism of several Android apps. They have detected a vulnerability dubbed Dirty Stream in popular apps like Xiaomi File Manager, WPS Office, and more.
Dirty Stream malware lets malicious apps send a file with a manipulated filename or path to another app’s home directory. It misleads the target to trust that filename or path and stores the file in the critical directory.
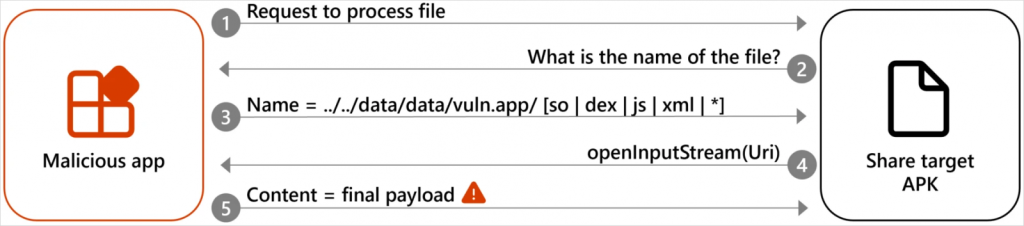
This eventually manipulates the data stream between two Android apps and possibly leads to unauthorized code execution, data theft, and more.
In a recent blog post, Dimitrios Valsamaras, Microsoft’s security researcher adds that such incorrect implementations unfortunately exist in large amounts. He adds:
We identified several vulnerable applications in the Google Play Store that represented over four billion installations. We anticipate that the vulnerability pattern could be found in other applications. We’re sharing this research so developers and publishers can check their apps for similar issues, fix as appropriate, and prevent introducing such vulnerabilities into new apps or releases.
Valsamaras says both companies responded to the findings and teamed up with Microsoft to fix the vulnerability. Google also published Microsoft’s report on the Android Developers website to draw developers’ attention to mitigate similar vulnerabilities down the line.
From the user’s point of view, there’s nothing much you can do other than update the apps regularly or avoid downloading APKs from unofficial third-party stores or shady websites.
You can check further details here.