Multiple Microsoft Azure flaws allow remote code execution
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
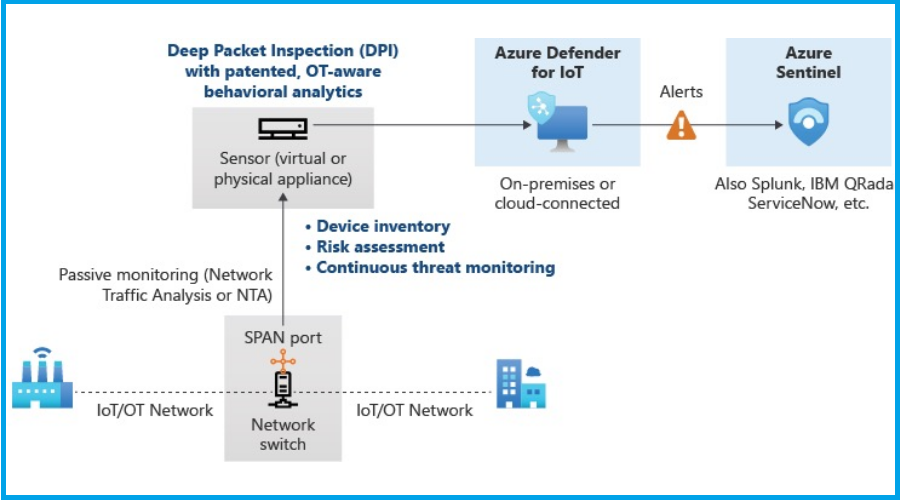
- It might not come as a surprise but SentinelLabsdiscovered a large number of security flaws in Microsoft Azure’s Defender for IoT last year
- Microsoft released various fix patches for all of these bugs, but Azure Defender for IoT users must take action immediately.
- However, you will be pleased to know that no evidence of in the wild exploits has been found in regards to any of the critical flaws mentioned here.

Did you know that SentinelLabs had discovered quite a number of security flaws in Microsoft Azure’s Defender for IoT last year?
Indeed, and furthermore, a few of these vulnerabilities were actually rated as Critical, as far as severity and impact on security go.
The Redmond-based tech giant issued patches for all the bugs, but Azure Defender for IoT users must take action immediately.
No evidence of in the wild exploits has been found yet
The above-mentioned flaws that were discovered by the security researchers over at SentinelLabs can allow attackers to remotely compromise devices protected by Microsoft Azure Defender for IoT.
Exploits based on these vulnerabilities take advantage of certain weaknesses in Azure’s Password Recovery mechanism.
SentinelLabs security experts also claim it proactively reported the security vulnerabilities to Microsoft in June 2021.
The vulnerabilities are tracked as CVE-2021-42310, CVE-2021-42312, CVE-2021-37222, CVE-2021-42313, and CVE-2021-42311 and are marked as Critical, some with CVSS score of 10.0.
That being said, the team hasn’t yet discovered evidence of in-the-wild abuse, if you were looking for the silver lining amidst all the chaos.
Despite the security flaws in Microsoft Azure Defender for IoT being over eight months old, there have been no recorded attacks that were based on the bugs.
Also important to keep in mind is the fact that these vulnerabilities that SentinelLabs discovered, affect both cloud and on-premises customers.
And even though there’s no evidence of in the wild exploits, a successful attack can lead to full network compromise.
Why, you ask? Well, mainly because Azure Defender for IoT is configured to have a TAP (Terminal Access Point) on the network traffic.
It goes without saying that, once attackers have unrestricted access, they can execute any attack or steal sensitive information.
What’s your take on this entire situation? Share your thoughts with us in the comments section below.