New Office 365 Phishing Campaign uses multi-factor authentication
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Office 365 users are again targeted by malicious third parties in phishing campaigns.
- Microsoft uncovered one such campaign that has been going on since September 2021.
- This time around, cyber attackers are using the multi-factor authentication features.

We haven’t touched the topic of malware and cyberattacks in some time, so we’re going to get back on that horse and blow the whistle.
You might not be aware of it yet but top security researchers and engineers at Microsoft actually stumbled upon a massive phishing attack that has been targeting more than 10,000 organizations since September 2021.
We’ve talked about a similar phishing campaign targeting Office 365 users late last year as well, a sign that attackers just won’t relent.
Yes, that is a lot of targets, and we are about to elaborate on the matter and tell you exactly what to look out for when using Office.
Microsoft experts pull the covers off new phishing campaign
The cybercriminals involved in this scheme used adversary-in-the-middle (AiTM) phishing sites to facilitate stealing passwords and related session data.
As a result, this allowed the malicious third parties to bypass multi-factor authentication protections to access user email inboxes and run follow-up attacks using business email compromise campaigns against other targets.
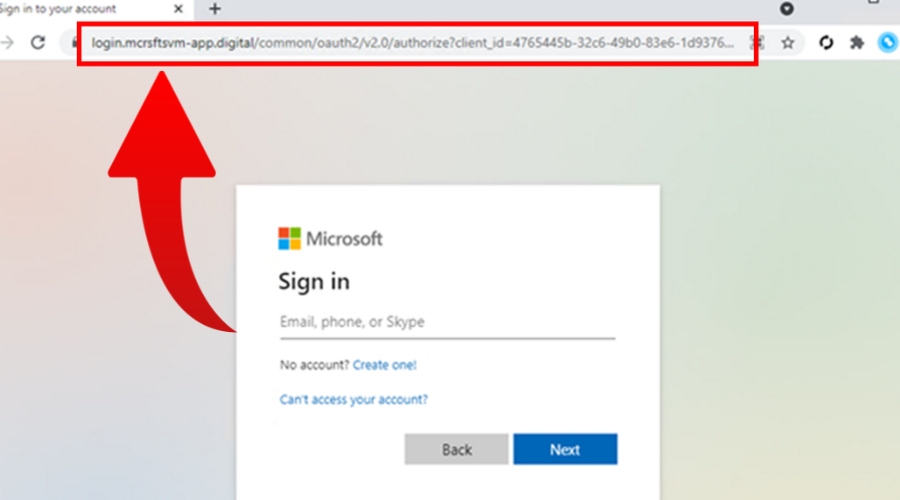
The above-mentioned main cyberattack targeted Office 365 users and spoofed the Office online authentication page using proxies.
Hackers used emails with HTML file attachments that were sent to multiple recipients of an organization, in which recipients were informed that they had a voice message.
From there, clicking to view the included attachment would open the HTML file in the user’s default browser, informing the specific user that the voice message was being downloaded.
Nothing further from the truth, as the victim was actually redirected to a redirector site from where the malware would latch on.
This phishing site looked exactly like Microsoft’s authentication site, with the exception of the web address.
The next step was for the victims to be redirected to the main Office website once successfully entered their credentials and completed the second step of verification.
Once this was done, the attacker would have already intercepted the data, and therefore all the information he needed, including the session cookie.
It goes without saying that after that, malicious third parties have disastrous options such as identity theft, payment fraud, and others.
Microsoft experts state that the attackers used their access to find finance-related emails and file attachments.. while the original phishing email that was sent to the user was deleted to remove traces of the phishing attack.
Providing your Microsoft account details to cybercriminals means that they have unauthorized access to your sensitive data, such as contact information, calendars, email communications, and more.
The best ways to stay protected against such attacks is to always double-check the source of any emails, not click on random stuff on the internet, and not download from shady sources.
Remember them, as these simple precautionary steps might just save your data, your organization, your hard-earned funds, or all of them at once.
Have you also received such a shady email from attackers pretending to be Microsoft? Share your experience with us in the comments section below.