Urgent-response type phishing attack hits Office 365 emails
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- A new phishing attack using a SharePoint document was discovered by researchers.
- A fake SharePoint file was introduced in a fake email to lure users into offering their account credentials.
- There are a few details to watch out for in a regular phishing attack. You'll find them in this article.
- Researchers offer a few recommendations when it comes to preventing phishing scams.

Researchers at phishing platform Cofense discovered a new phishing attack aimed at Office 365 accounts.
The method used isn’t a novelty: the attackers inserted a fake SharePoint document into an email, requesting urgent review and response.
The seriousness of the event is more concerning since it managed to bypass Microsoft’s security layers, the report shows:
The campaign was found in an environment protected by Microsoft’s own secure email gateway (SEG). With thousands of individuals still required to telework, this has created a perfect opportunity for hackers to lure their victims with almost picture-perfect sharing themed emails.
The details to look after in a phishing attack
Similar to other phishing scams, this one was also spread via a seemingly legitimate email.
A first notable detail was the sender’s email address: the name wasn’t clear, nor was a Microsoft reference or the organization’s title.
Then, the email contained a team project document apparently uploaded and shared via SharePoint, plus a general message claiming urgent attention and response.
This type of scams falls into the same category of attacks requesting a change/refill of login credentials.
Besides, emails calling for urgency should be usually considered suspicious, especially when they come from an unknown or undisclosed address.
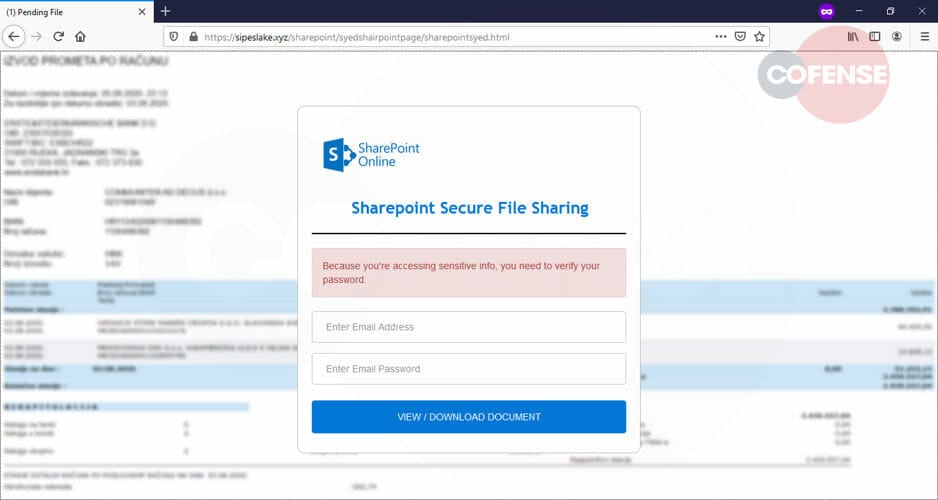
If clicked, the fake link takes to a landing page that displays Microsoft’s SharePoint logo, a blurry background, and a request to log in to view the document.
Of course, upon entering the credentials, the user is taken to an irrelevant document, and only then one realizes the scam.
The entire scam proves that sharing and accessing sensitive documents via email (even using Microsoft’s protocols) is quite risky. A few common-sense ways to prevent falling victim for such attacks would be to:
- Install an antivirus with phishing and/or ransomware shield (most tools have it)
- Make sure the system and all programs are up to date
- Exercise precaution when it comes to revealing credentials or opening suspicious emails or documents
- Block the addresses of potential scammers
Hopefully, this article offered some useful details about phishing scams and how to prevent them. Feel free to leave comments in the section below.