Turns out themed Microsoft Word Documents are actually malware
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- There is a new Microsoft malware document masking itself as one made with Windows 11 Alpha.
- The malicious documents exploit VBA macros to successfully infiltrate the system.
- The FIN7 group is suspected to be behind this attack, given their previous history in similar cases.
Microsoft users have one more thing to worry about. A security research firm has discovered a new Microsoft Word document malware. The maldoc masks itself as a document made on Windows 11 Alpha. Anomali Threat Research has discovered six similar malicious malware and warns users to be vigilant as Microsoft tries to stay on top of the situation.
Microsoft has been facing malware attacks in the recent past where attackers have been impersonating familiar and commonly used productivity tools to launch an attack. The malware document discovered is named “Users-Progress-072021-1.doc”.
Attack took place in late June
According to Anomali, the attack likely took place in late June and ended in late July. The firm affirms that the FIN7 group is behind the attack and the main aim was to deliver a variation of Javascript through the backdoor as they have been trying since 2018. FIN7 is considered the longest-running cyber-attack group since 2013.
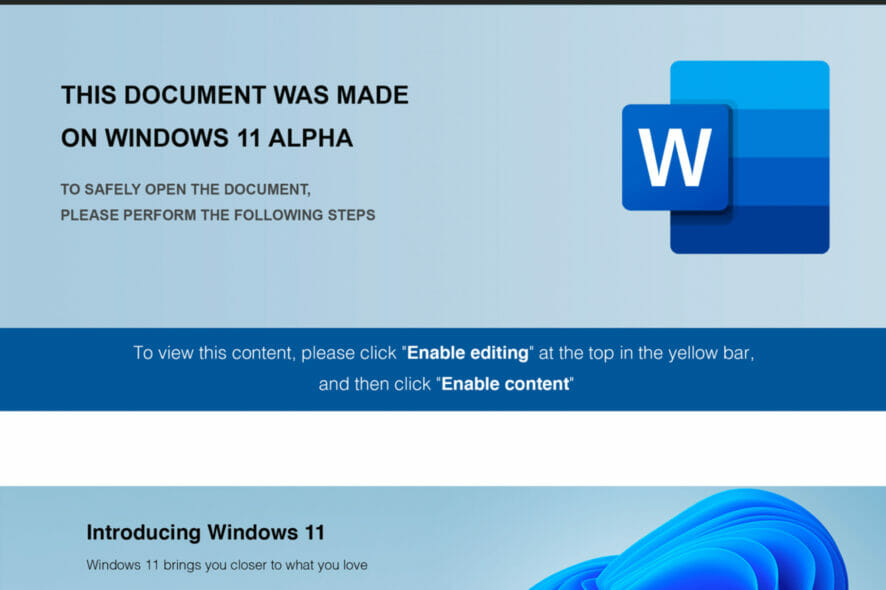
The chain of infection first started with an image that masqueraded to have been made with Windows 11 Alpha. The image tasked users to ‘Enable content’ or ‘Enable editing’ for the next step.
A Twitter user named NinjaOperator took to Twitter to question whether FIN7 was behind the attack when the news broke out.
Users are lured using instructions on document’s cover
The malware document is using Visual Basic for Application macros. Once successful, a javascript payload is dropped. The macro becomes executed when a user performs basic functions such as ‘enabling editing’ or ‘enabling content,’ just as the instructions say on the cover.
Users familiar with Windows 11 builds and variations are less likely to suffer from the attack, but others may fall for this trick and run the file.
The malware document can perform several checks such as:
- Memory capacity
- Language
- VM check
- CLEARMIND check
CLEARMIND is a domain for a POS service provider. FIN7 is known for targeting such domains to gain access to large-scale data.
The group continues to be active despite measures taken to bring the attacks to an end. Users are warned to remain extra vigilant on all files.
Have you suffered from any malware attacks in the recent past? Share any tips you found helpful in the comment section below.