What's the difference between WannaCry and Petya ransomware?
5 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

If you’ve been off the grid for some time and somehow managed to skip on all the fuzz about WannaCry and Petya ransomware, we prepared a brief explanation about the subject and enlisted the main differences between Petya (sometimes called GoldenEye) and already restrained WannaCry malicious software.
In the era where computers are governing so many economic, industrial, and social aspects, it’s not strange to expect a cyber criminal to emerge as a worthy and horrifying successor to hijacking and bank robberies that created a havoc in the past times. Data equals money and money equals money, simply put. One of those neo-crimes that’s quite present nowadays is ransomware.
Ransomware is one out of many cyber crimes. It strikes critical and sensitive victim’s data and demands a ransom, and as a leverage holds the decryption key. If you don’t agree to the terms of a cyber-thief, your data is either deleted permanently or published, depending on how secretive or personal is information that’s contained in the hijacked files.
What’s the main difference between WannaCry and Petya ransomware?
Now, as same as with its predecessors, in the ransomware ‘business’ also, we have small tricksters, wannabe hackers, and big, well-equipped and knowledgeable experts. The first group takes on an individual (or group of individuals, if you like) and the other group uses a high-end malicious software as their targets are companies and high-profile victims. We’re talking about millions of dollars in that game of cat and mouse. These folks are not joking, this is a real deal.
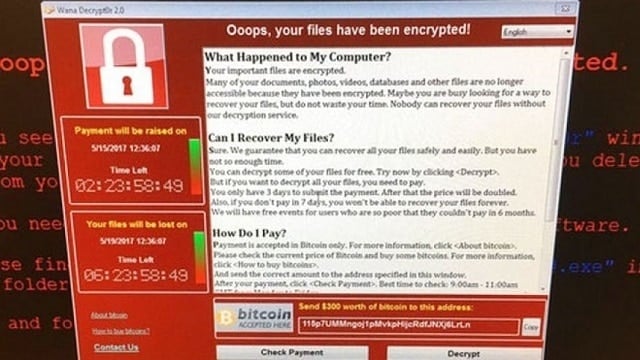
On short notice, about two months ago, a global ransomware event, later known as the WannaCry crisis, emerged. It struck down more than a few companies in various countries around the world, including the National Healthcare Service in England and telecom giant from Spain. With Healthcare it wasn’t just about money, the human lives were involved which makes it even more preposterous.
Hackers used leaked Windows vulnerability called EternalBlue, which, allegedly, was used by NSA for some ghost doings in the Middle East. So, basically, they used a batch file, MS Office update, or third-party program’s update to corrupt Windows-powered computers and encrypt the HDD data with the decryption key as they leverage. They asked for 300$ worth of bitcoins in order to retrieve the sensitive data on each individual’s PC.
Now, one of the reasons attacks were so successful initially is that most of the companies or individuals that were antagonized were running old Windows versions, some even Windows XP (it’s 2017, you guys!), that are not patched with appropriate security updates. And antivirus won’t help you so much (or can it?) when the system flaw is the card those hackers are playing on.
Luckily, there was also a flaw within the WannaCry’s code and it got struck down after Microsoft provided updates a week later. Moreover, the malicious program was programmed to cover a large area and instead of targeting only chosen targets, it flooded the internet. That made it hard for them to track payments. Petya or GoldenEye is similar but seemingly better organized and orchestrated. It has fewer flaws and its perpetrators goal is more a well-aimed shot than a barely controlled burst.
To date, Petya struck only around 2,500 targets and WannaCry struck, in much shorter span, hundreds of thousands before it was put down. Another difference is related to paying validation. Nasty folks behind WannaCry attacks weren’t competent enough to develop a reliable way to confirm payments of their victims. That way they missed on a lot of opportunities to profit. Petya uses a small email provider called Posteo for validation. Once they get the email with the proof of payment, they send the decryption key and that concludes the procedure.
The main difference, however, is in the software itself. It attacks in many different ways so, experts in the matter think it’s much harder to stop it. Updates and security patches won’t help, allegedly. At least not on their own. Petya inflicted malware starts with the system, it comes in different versions and there’s no simple solution that should address it, yet.
Moreover, many companies are deluded into thinking that patches or additional security measures aren’t essential, so the chance is, Petya will be even growing as the time passes until it reaches the worldwide menace levels. This is just the beginning of a massive global ransomware crisis and a test of alertness for major players. It’s a prime example that security measures are a must and that we can expect a lot of other cyber-criminals following this route.
What’s your opinion on the subject? Don’t forget to tell us in the comments section below.
RELATED STORIES YOU NEED TO CHECK OUT: