Fix: Event ID 4663, An Attempt Was Made to Access An Object
Remove unfamiliar event logs from the system for a quick fix
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The Event ID 4663 could indicate your system/server is at risk because an unauthorized account is trying to access files.
- The user account that is attempting to access the system is not permitted to do so or does not have the necessary permissions.
- You can easily check the event logs for any suspicious users and remove them.
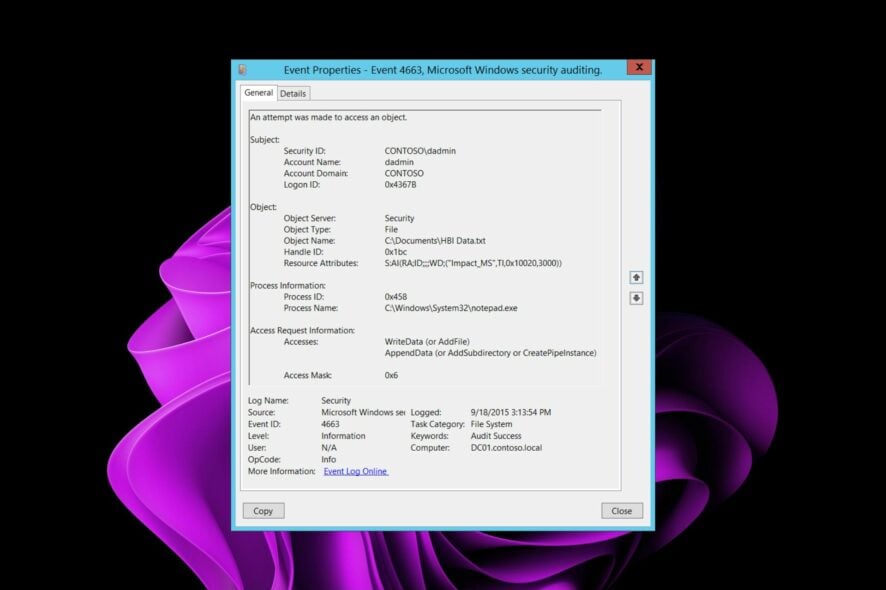
Event 4663 may indicate that a user has logged on to a domain computer using an account that is not authorized to be used to log on to the domain. This can occur if the account was disabled or removed from the Domain Admins group.
If you see this error regularly, it could be related to permissions on shared folders or drives and/or improperly configured user accounts with insufficient access rights. Still, it’s worth checking out because if left unattended, the user may gain access.
What is Event ID 4663?
Event ID 4663 is logged when a particular operation is performed on an object. This event can be viewed in the Security log and has a target of the security log. The Event ID 4663 will be recorded in the security log when a user attempts to perform an operation that requires administrator permissions.
The main categories of object types are as follows:
- File system objects (for example, files, folders, or printers)
- Kernel objects (for example, processes and threads)
- Registry objects (for example, keys and values)
- System objects (for example, drivers)
- Objects on removable storage or devices
An attempt was made to access an object could mean:
- Object is no longer present on the server – If you are having trouble accessing a file or folder, it means that this file or folder was deleted from the server.
- The object is present on the server, but its name is not valid – It’s possible that the object may have been deleted or renamed since it was last accessed.
- Object is present on the server, but in a different location – This error can occur if you try to access a file or folder that has been moved or renamed.
- The object is present on the server, but your account does not have access rights – This error occurs when your user account does not have sufficient read/write privileges for you to do so.
How can I fix Event ID 4663?
First off, ensure you check the following:
- Turn on your firewall to ensure unauthorized access is limited. Also, check out what to do if you’re unable to turn on Windows Firewall.
- Check whether there’s a misconfiguration of the SACL (System Access Control List), which prevents users from accessing objects they should be allowed to.
1. Check and remove Event logs
- Click on the Windows Search icon on the taskbar, type Event Viewer and click Open.
- Navigate to the left-hand pane, expand the Windows Logs menu and select Security.
- Scroll through the various logs and locate one with Event ID 4663.
- Once you locate a log with Event ID 4663, make note of the Account Name that attempted to log in
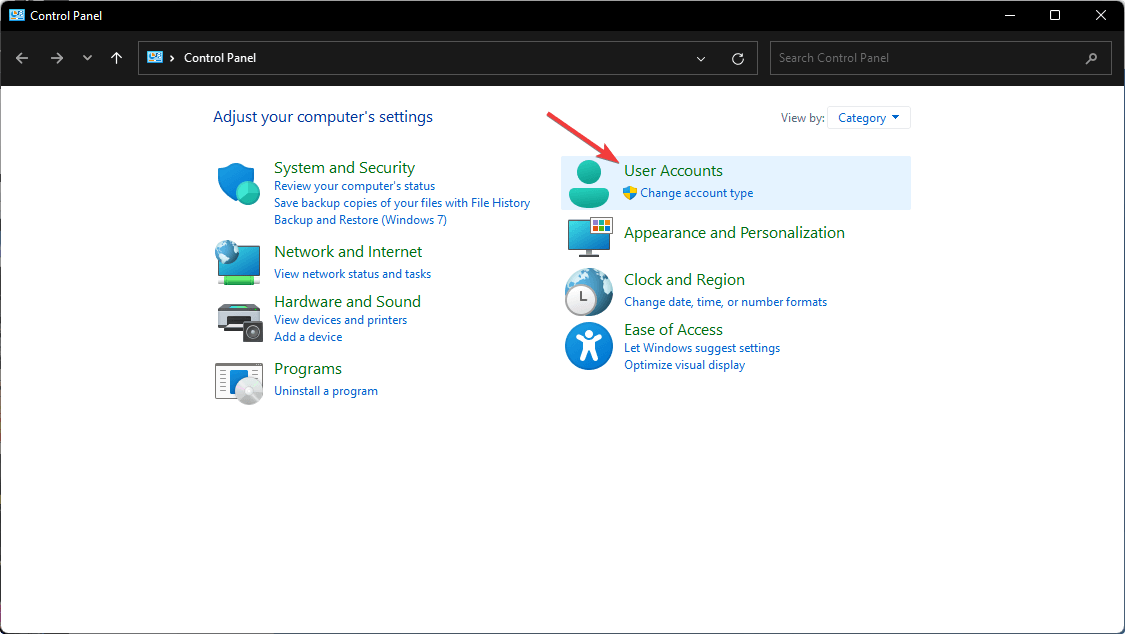
- Bring up the Search icon again, type Control Panel and click Open.
- Select User Accounts.
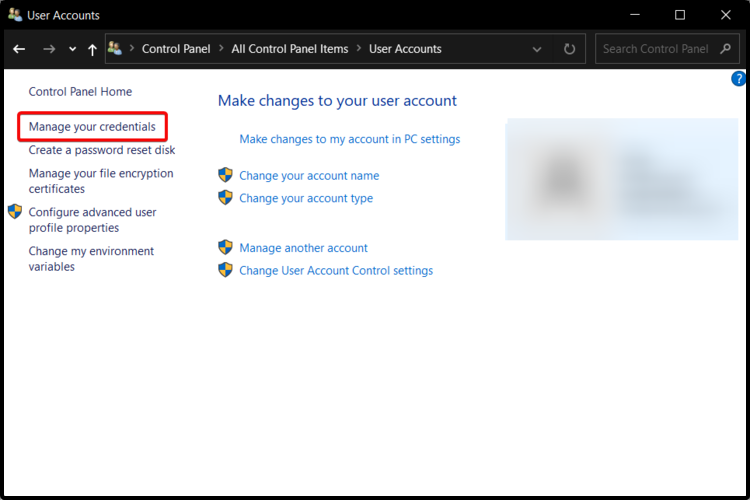
- Click on Manage your credentials on the left-hand side.
- Select Windows Credentials in the new window.
- Expand the unfamiliar user account, and in the drop-down menu, click Remove to get rid of that user.
The Event ID 4663 attempt may be due to an internal or external security breach, and a user account is being used by malicious software to access the system. This account may have been created by malware or by an attacker exploiting a vulnerability in network services.
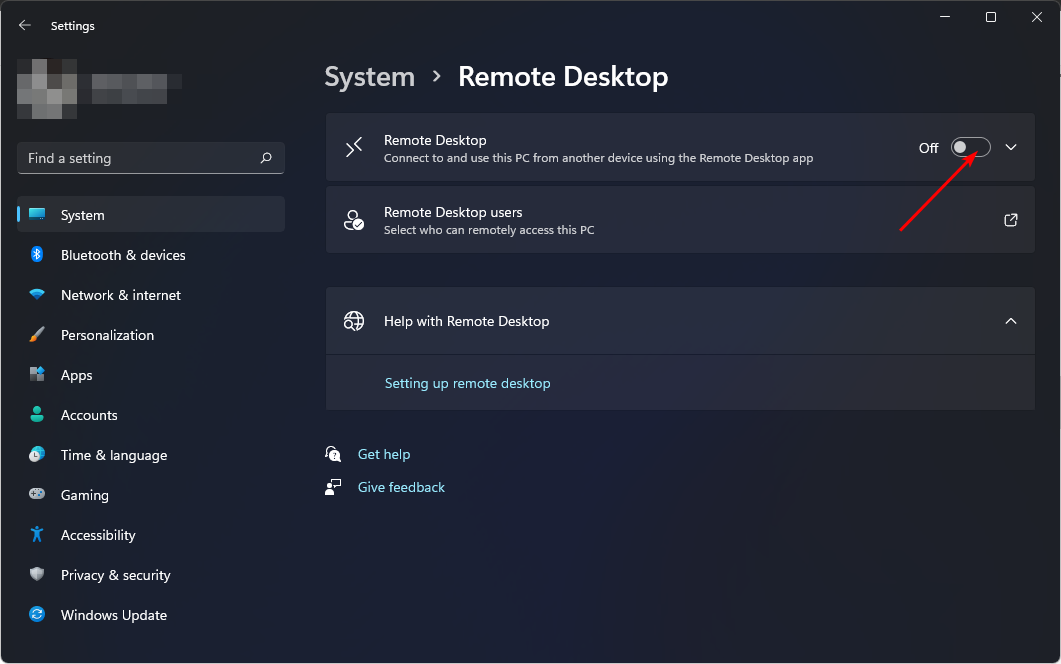
2. Disable remote access
- Hit the Windows key and click on Settings.
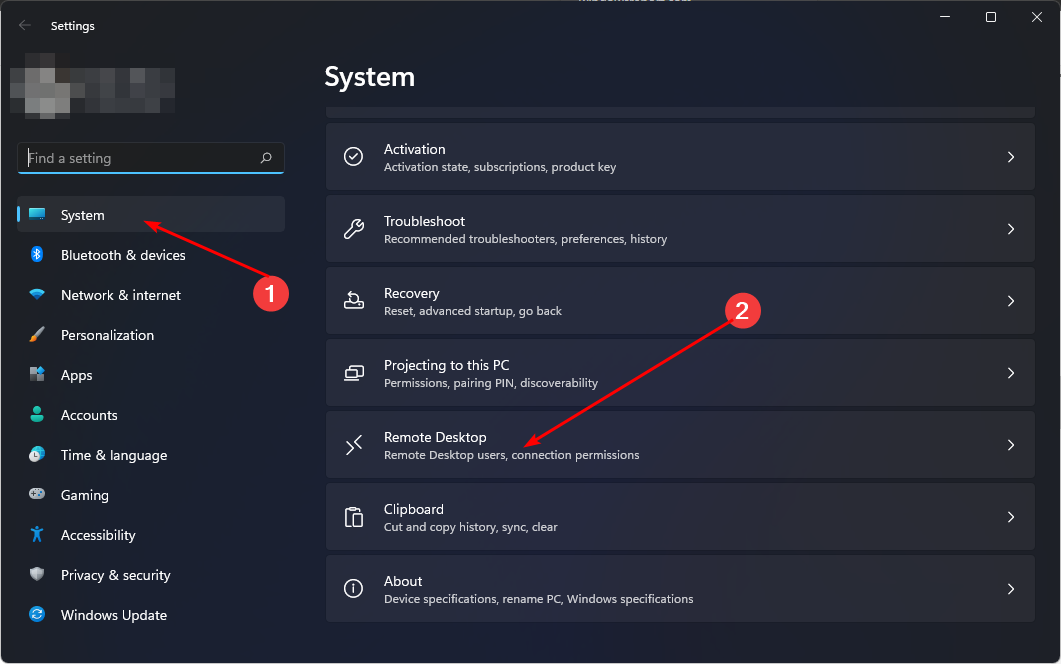
- Click on the System tab and scroll down to Remote Desktop.
- Toggle the switch next to Remote Desktop to disable the feature.
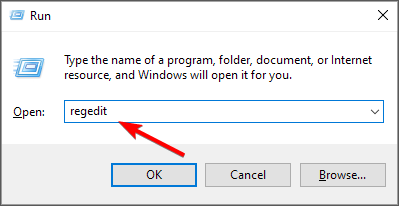
- Next, hit the Windows + R keys to open the Run command.
- Type regedit in the dialog box and hit Enter to open the Registry Editor. Select Yes if the User Account Control asks if you want to make any changes.
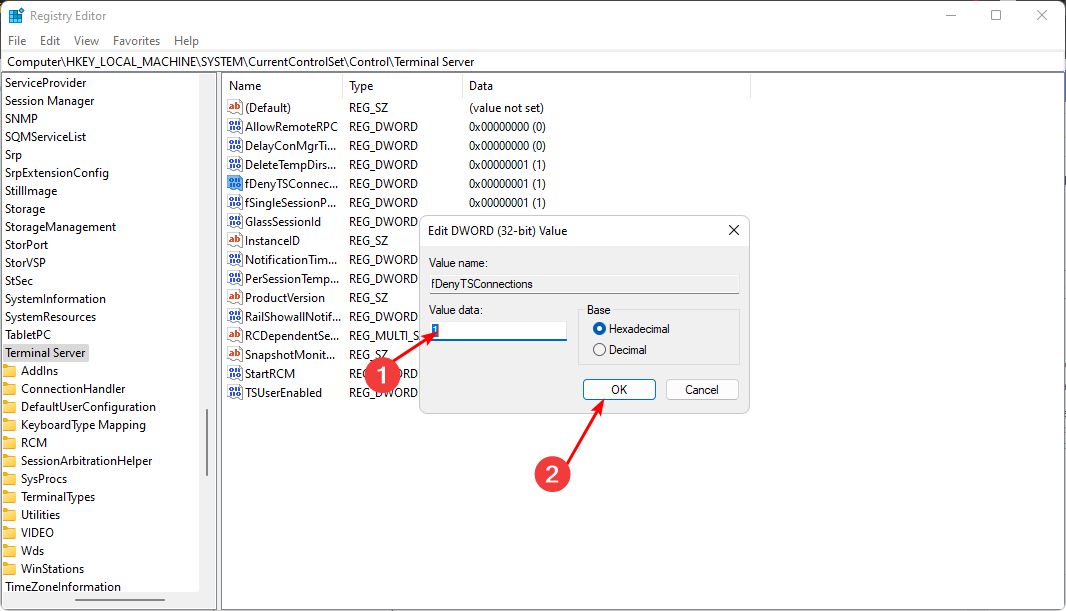
- Navigate to the following location:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server - Double-click on fDenyTSConnections on the right pane to open it.
- Set the Value data to 1, then click OK to finish up.
A Windows server can be accessed remotely if it is running a service. For example, if you want to access your server via Remote Desktop, you need to enable this feature.
Disabling remote access should be a temporary security measure until you determine whether the Event ID 4663 is a brute-force attack.
That’s all we had for this Event ID, but check out what we have in store. For instance, the Event ID 4648, where a logon using credentials was attempted, or Event 4502 that is related to WinREAgent.
Share any additional thoughts on this topic in the comment section below.


User forum
0 messages