Microsoft explains the Windows 11 security requirements, tries to hack into Windows 11
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
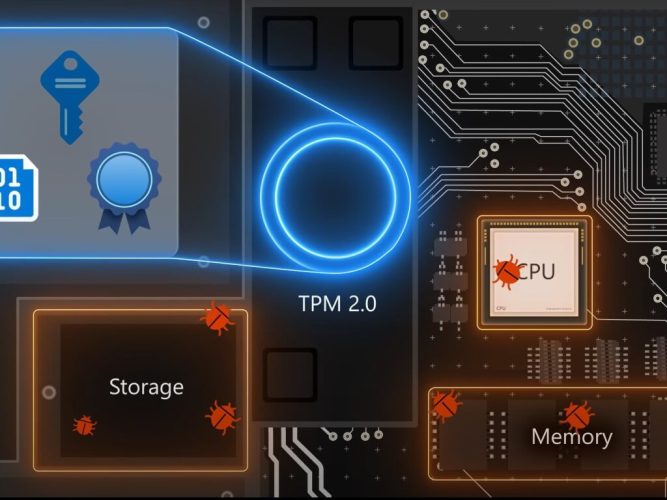
One of the biggest controversies with Windows 11 is the minimum hardware requirements. Microsoft has held that these requirements are for reliability, security, and compatibility, but we haven’t really seen these claims put to the test. A recent Microsoft Mechanics video, though, showcases the security features of Windows 11, with Microsoft even going as far as to show how it works by trying to hack into a Windows 11 PC.
In the 17-minute video, Dave Weston, Microsoft’s own Windows security expert, explains the reasoning behind hardware requirements and how it can protect your Windows 11 PC against modern malware and other attacks. He spends a lot of time focusing on the benefits of TPM 2.0 and the secure boot aspect of Windows 11 by showing off and hacking a Windows 10 system with the features turned off.
The video begins by showcasing how remote desktop connections can leave your PC open to remote hacks if TPM and Secure boot are not enabled. He pulls the IP, username, and password for the remote machine from a database, gets into the system remotely, runs a CMD prompt on a remote system as an admin, unlocks the bootloader, and launches a bootkit. He then remotely shuts down the system, only to maliciously re-write the MBR. Again, this is with Secure Boot turned off, and the system set to Legacy in the BIOS mode.
In addition, the video also highlights the benefits of virtualization-based security and enhanced sign-in security. Weston shows how the features, when turned off on Windows 11, can leave a device open for in-person physical hacking through direct memory access via Thunderbolt. He uses a device connected to the victim’s PC to spoof a fingerprint and then logs into that PC using just a gummy bear.
Essentially, with Windows 11’s virtualization-based security, the encryption keys, signature, and code, are all separated by hardware from the operating system, making the previous physical hack impossible. And, UEFI, Secure Boot, and Trusted Boot help prevent rootkits and boot kits that modify the early boot BIOS by checking the bootloader’s signature to make sure it’s not modified.
User forum
0 messages