Attackers are exploiting Office 365 credentials to access organizations’ networks
4 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Attackers can bypass MFA on Microsoft Office 365 by stealing authorization codes or access tokens.
- The Microsoft Threat Intelligence Team has tracked a campaign of malware affecting organizations in Australia and Southeast Asia.
- Hackers are creating new methods of phishing attacks by registering Windows devices with Azure Active Directory through the use of stolen Office 365 credentials.
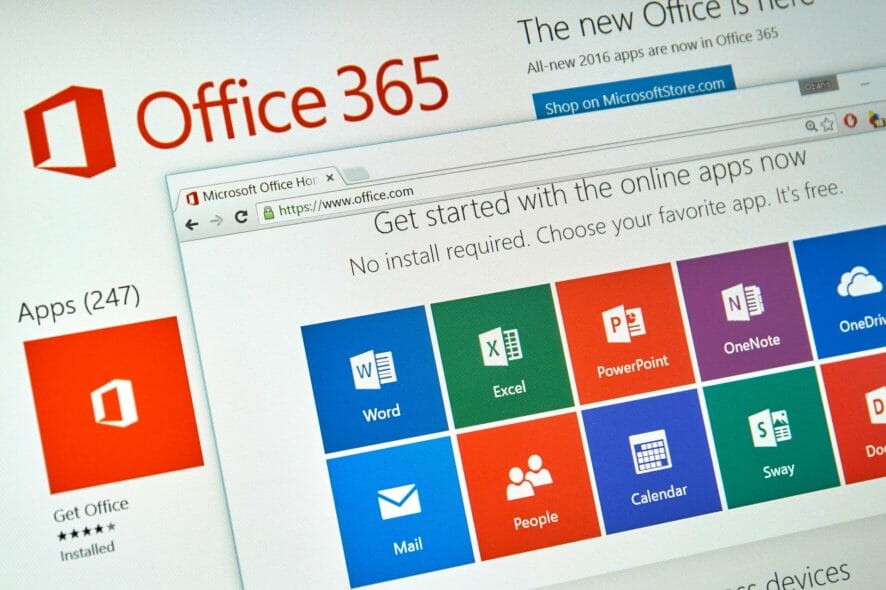
Hackers are attempting a new method of widening the scope of their phishing campaigns by using stolen Office 365 credentials to register Windows devices with Azure Active Directory.
If attackers are able to access an organization, they will launch a second wave of the campaign, which consists of sending more phishing emails to targets outside the organization as well as within.
Target areas
The Microsoft 365 Threat Intelligence Team has been tracking a malware campaign targeting organizations in Australia and Southeast Asia.
To get their targets’ information, the attackers sent out phishing emails that looked like they were from DocuSign. When users clicked on the Review Document button, they were taken to a fake login page for Office 365, already pre-filled with their usernames
“The victim’s stolen credentials were immediately used to establish a connection with Exchange Online PowerShell, most likely using an automated script as part of a phishing kit. Leveraging the Remote PowerShell connection, the attacker implemented an inbox rule via the New-InboxRule cmdlet that deleted certain messages based on keywords in the subject or body of the email message,” the intelligence team highlighted.
The filter automatically deletes messages containing certain words related to spam, phishing, junk, hacking, and password security, so the legitimate account user will not receive non-delivery reports and IT notification emails they might otherwise have seen.
The attackers then installed Microsoft Outlook on their own machine and connected it to the victim organization’s Azure Active Directory, possibly by accepting the prompt to register Outlook when it was first launched.
Finally, once the machine became part of the domain and the mail client was configured like any other regular use within the organizations, the phishing emails from the compromised account fake Sharepoint invitations pointing again to a fake Office 365 login page became more persuasive.
“Victims that entered their credentials on the second stage phishing site were similarly connected with Exchange Online PowerShell, and almost immediately had a rule created to delete emails in their respective inboxes. The rule had identical characteristics to the one created during the campaign’s first stage of the attack,” the team indicated.
How to bypass
The attackers relied on stolen credentials; however, several users had multifactor authentication (MFA) enabled, preventing the theft from occurring.
Organizations should enable multifactor authentication for all users and require it when joining devices to Azure AD, as well as consider disabling Exchange Online PowerShell for end users, the team advised.
Microsoft also shared threat hunting queries to help organizations check whether their users have been compromised via this campaign and advised that defenders must also revoke active sessions and tokens associated with compromised accounts, delete mailbox rules created by the attackers, and disable and remove malicious devices joined to the Azure AD.
“The continuous improvement of visibility and protections on managed devices has forced attackers to explore alternative avenues. While in this case device registration was used for further phishing attacks, leveraging device registration is on the rise as other use cases have been observed. Moreover, the immediate availability of pen-testing tools, designed to facilitate this technique, will only expand its usage across other actors in the future,” the team advised.
Loopholes to lookout for
Microsoft’s threat intelligence analysts recently flagged a phishing campaign that targeted hundreds of businesses, this one an attempt to trick employees into granting an app named “Upgrade” access to their Office 365 accounts.
“The phishing messages mislead users into granting the app permissions that could allow attackers to create inbox rules, read and write emails and calendar items, and read contacts. Microsoft has deactivated the app in Azure AD and has notified affected customers,” they indicated.
Attackers can also bypass Office 365 Multi-Factor Authentication by using rogue applications, stealing authorization codes, or otherwise obtaining access tokens rather than their credentials.
Have you fallen victim to these attacks by hackers before? Share your experience with us in the comment section below.


User forum
0 messages