GitHub faces large-scale attack posing threats to millions of projects
Verify the source and legitimacy of a code before using it
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
In a recent development, millions of users and developers on GitHub are on high alert, as the platform is under a large scale attack.
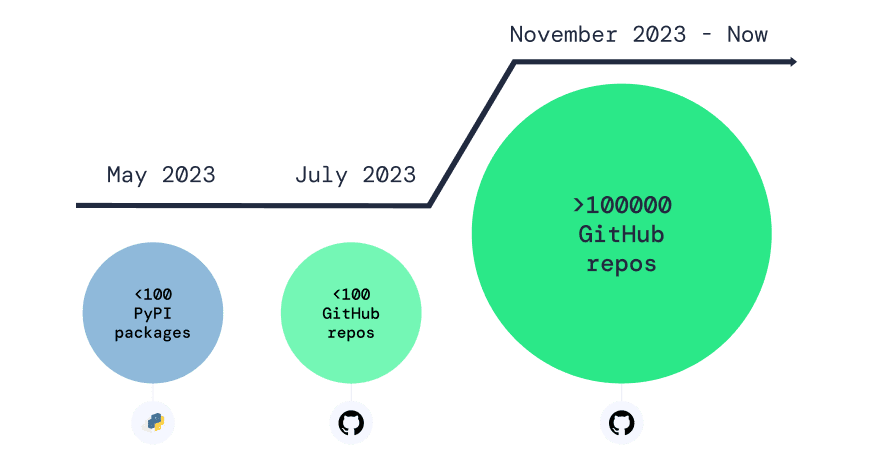
According to security experts at Apiiro, there is a concerning trend which indicates that malicious actors are targeting GitHub repositories, potentially jeopardizing more than 100,000 projects
Apiiro also mentioned steps on how repo confusion attacks happen:
In order to maximize the chances of infection, the malicious actor is flooding GitHub with malicious repos, following these steps:
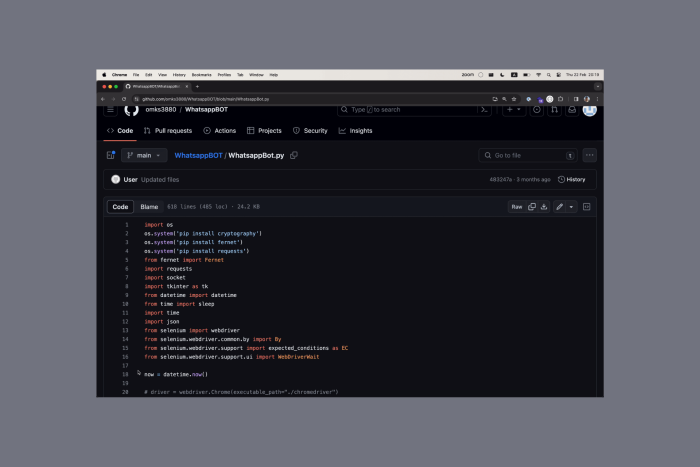
- Cloning existing repos (for example TwitterFollowBot, WhatsappBOT, discord-boost-tool, Twitch-Follow-Bot, and hundreds more).
- Infecting them with malware loaders.
- Uploading them back to GitHub with identical names.
- Automatically forking each thousands of times.
- Covertly promoting them across the web via forums, discord, etc.
The attack uses a technique called malicious repository obfuscation, in which attackers clone legit repositories, inject harmful code, and later re-upload them to the GitHub platform.
Attackers usually target popular and frequently downloaded repositories, and to amplify the impact, they create several counterfeit forks of the compromised repositories using automated methods, which are then spread through social media, online forums and more, which tricks users into downloading these malicious repos.
How does the attack work?
These compromised repositories are a threat as unsuspecting users can download them, which might lead to comprising their devices or exposing them malware.
Once malicious repos are used on your device, the hidden payload unpacks 7 layers of obfuscation, involving pulling malicious Python code and a binary executable. The malicious code, would then collect confidential data, including login ids and passwords for apps, browser passwords and cookies. It sends the data back to malicious actors C&C server.
How do I know if I am infected?
To know if you are infected, look for Python patterns and look into the matches:
- exec(Fernet
- exec(requests
- exec(__import
- exec(bytes
- exec(“””\nimport
- exec(compile
- __import__(“builtins”).exec(
Next, check if any repos related to the automation of actions on social platforms, gaming, and bots are present, and then remove them. You can also reinstall the repositories after carefully verifying the source or running it in Sandbox first.
In case you suspect you are using a cloned repo, then check your browser password and change all of them related to any financial service, streaming service, crypto service, email service, eBay, Twitter, Amazon, Facebook, Instagram, AliExpress, Discord, YouTube, Spotify, Yahoo, TikTok, Twitch, Express VPN, and Telegram.
The report by Apiiro also talks about some factors, including user-friendly interface, the existence of numerous hidden repositories, and easily accessible APIs, which adds to GitHub’s vulnerability to these types of attacks.
This malicious campaign started in May 2023, and several malicious repos were uploaded to GitHub between July and August 2023.
In November 2023, Apiiro detected them and notified GitHub, and the platform was successful in identifying and removing malicious repositories.
However, the campaign still continues and attackers are more presistent to inject harmful code into the supply chain. GitHub is continuously trying to detect and remove these codes once uploaded, however, this is still putting users to risk.
Therefore, while the platform is working to make it safe, we developers and users must also exercise caution while downloading any file or code from it, especially if the repositories are familiar to you. Also, make sure you verify the source and code legitimacy before integrating it into your projects.
In case you encounter any malicious repo, GitHub and Apiiro insist you to report it, to prevent it from doing further harm.
Have you encountered any malicious repos so far? If yes, share your experience in the comments section below.