Microsoft is investigating an Outlook security vulnerability that could eventually reveal your Windows passwords
CVE-2023-35636 is not so dangerous but stay alert for any updates
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
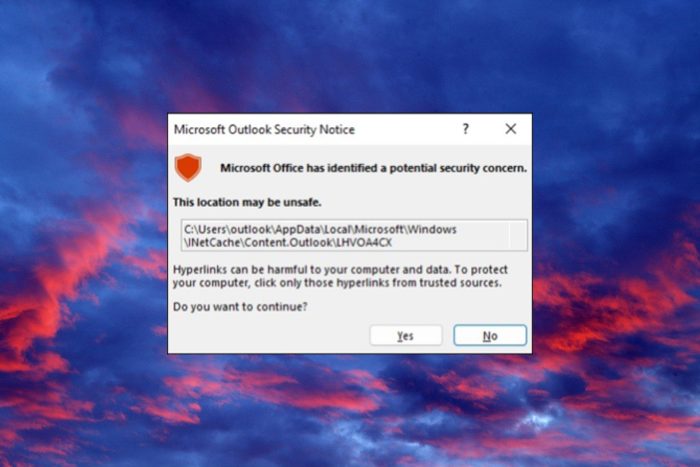
Microsoft prompted a security notice in Outlook that occurs after installing the December security updates.
This issue is classified as the CVE-2023-35636 which is listed as important and it’s less likely to be exploited, although if it is, it could allow the disclosure of NTLM hashes.
A NTLM hash is a cryptographic format used by Windows to store passwords, and we don’t need to tell you how important it is to keep them safe. They are stored in the Security Account Manager or the NTDS file of a domain controller.
What is the Outlook vulnerability all about?
The error occurs when you click an .ICS file and you will be prompted with the following message: Microsoft Office has identified a potential security concern. This location may be unsafe.
However, the security notice or the vunerability itself is not threatening unless you open a specific file comming from an attacker.
Microsoft also issued a recommendation on how to stop getting this message, by changing a registry key. Open the Registry Editor by typing regedit in the Run console (Ctrl + R). Then, go to the following path: HKEY_CURRENT_USER\software\policies\microsoft\office\16.0\common\security
Now, look for the DisableHyperlinkWarning DWORD and change its value to 1.
The only issue is that by changing this DWORD in the registry, you will disable all the security warnings in Office, not only the one for the .ICS files.
Microsoft recognized this issue and it will be addressed in a future update so make sure you install all the latest Microsoft 365 updates whenever you get them. Also, after the update retrace the steps above to reenable the Hyperlink Warning. Just change the DWORD value to 0 to do that.
Did you get the vulnerability warning in Outlook? Tell us about the problem in the comments section below.



User forum
0 messages