Microsoft says Google “put customers at risk” by disclosing Windows vulnerability
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
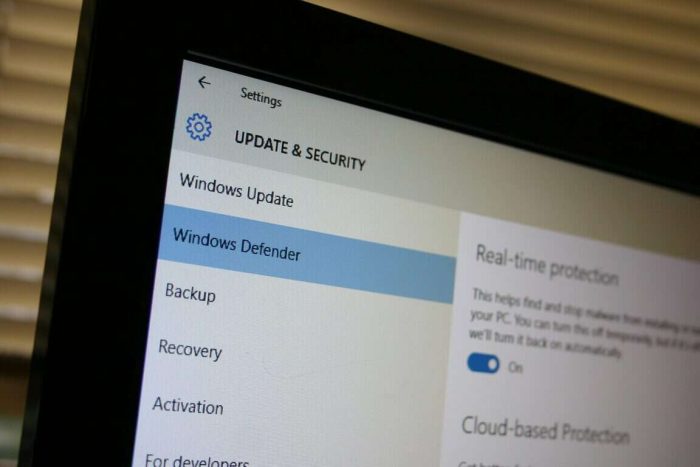
Yesterday, Google published a new blog post on its Security blog to warn Windows users about a critical vulnerability in Windows that hasn’t been addressed by Microsoft seven days after having reported it to the company. According to the Alphabet subsidiary, the 0-day vulnerability is “particularly serious because we know it is being actively exploited.” The company provided the following technical details below:
The Windows vulnerability is a local privilege escalation in the Windows kernel that can be used as a security sandbox escape. It can be triggered via the win32k.sys system call NtSetWindowLongPtr() for the index GWLP_ID on a window handle with GWL_STYLE set to WS_CHILD. Chrome’s sandbox blocks win32k.sys system calls using the Win32k lockdown mitigation on Windows 10, which prevents exploitation of this sandbox escape vulnerability.
In the same blog post, Google also mentioned another 0-day vulnerability in Adobe Flash Player that has already been addressed by the company through new updates via Adobe’s updater and Chrome auto-update. Since Google published its new policy for actively exploited critical vulnerabilities three years ago, the company’s new security stance is to disclose unpatched vulnerabilities if affected vendors don’t provide a fix seven days after being notified about them by Google security researchers.
It’s actually not the first time that Google publicizes a flaw in Windows, as the company did so in January 2015 for an exploit that allowed attackers to run arbitrary code with elevated privileges (Microsoft patched it a few days later when Patch Tuesday arrived). But nearly two years after this event, it seems that Microsoft is still not a fan of Google’s security practices, according to this statement released to VentureBeat yesterday:
We believe in coordinated vulnerability disclosure, and today’s disclosure by Google puts customers at potential risk. Windows is the only platform with a customer commitment to investigate reported security issues and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.
As Microsoft didn’t really acknowledge the security flaw in this statement, it’s not clear if the company is already working on a fix though we hope it is. Recommending users to use Windows 10 and Microsoft Edge for best protection also doesn’t really cut it if this flaw is already being exploited. Instead, Google is recommending Windows 10 users use Chrome on Windows 10 which according to Google “prevents exploitation of this sandbox escape vulnerability.”
With Patch Tuesday only a week a way, we’ll see if Microsoft address this security issue as soon as possible or stick to its usual schedule. While Google may legitimately think that 0-day vulnerabilities should be addressed by companies in seven days, pushing companies to rush these sort security fixes could also in some cases do more harm than good. Sound off in the comments if you think Google did the good thing by disclosing details about this new security flaw in Windows.




User forum
0 messages