Protect your PC: Ransomware attack increases by two fold in 2017
2 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Ransomware is undoubtedly getting a lot of attention these days especially after wide spread WannaCry episode. For the uninitiated, the ransomware is a piece of code that encrypts the files on your computer and demands a ransom to give away the decryption code. Yes, we have seen a variety of Ransomware plaguing the machines and invariably organisations and enterprises figure out on the top of the list.
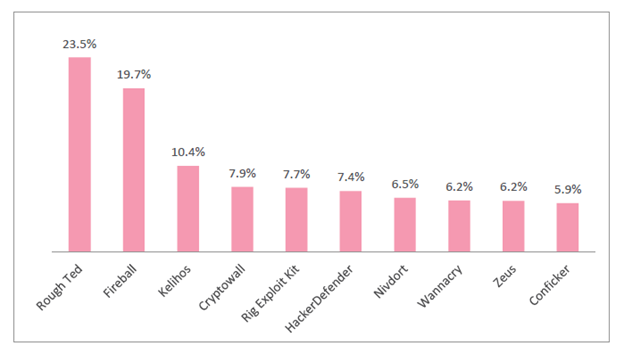
As per a mid-year cyber attack, trends report from security analyst company CheckPoint the percentage of ransomware has doubled in the first half of this year as opposed to 2016. Furthermore, the report finds that 23.5 percent of the organisations were affected by the RoughTed malvertising campaign while 19.7 percent of the organisations were affected by the Fireball malware during the same time frame.
The report further sheds light on how the attackers are devising new methods to exploit Microsoft Office, in fact, we recently reported on how attackers were using PowerPoint files to gain access to the machine. The attackers are also introducing new methods to offload the malware and this will not require the user to open a backdoor for the attackers. The ransomware is also being disguised such that the anti virus/malware protection suite find it difficult to detect.
The report also mentions the cascading effects of “nation-state level malware” which is usually aimed for the masses and it can virtually hunt anyone instead of specified targets. Such attacks can be prevented by using the available solutions like network micro-segmentation, threat emulation and endpoint security. In fact, it is for this very reason that security solutions from company’s like BitDefender include ransomware protection.
The worst part, however, is that the Mobile malware developers are also actively developing malware. They usually use these malicious codes to control any activity on the device and also create a one-stop attack in order to fraud, steal information and also disrupt apps. The graph above represents the percentage of enterprises/organisations that were affected by the malware.
RELATED STORIES YOU NEED TO CHECK OUT:
- Windows 10 virus removal tools to vanquish malware for good
- Protect your PC from ransomware and malware with Windows Defender’s new Controlled Folder Access
- 5 best malware tracker maps to see security attacks happen in real-time




User forum
0 messages