Best Ransomware Decrypt Tools to use to Stay Protected
Find out the best options on the market right now
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Your computer files have been encrypted with the AES algorithm and you need to pay $294 to recover your data.
If this line rings a bell to you, that’s because you might have probably been a victim of ransomware before. As ransomware attacks continue, you can avoid paying for the decryption key using the following tools.
Or if you don’t want to use a third-party tool, we got other fixes for you in case you can’t decrypt files in Windows 10/11.

Secure your devices with award-winning cybersecurity technology.

Maximize your PC's security and performance with top-notch digital threat detection.

Keep secure with groundbreaking AI detection and prevention technology.

Browse the web securely for up to 3 devices across Windows, Mac, iOS or Android systems.

Best security tool for intense browsing activity.
How to decrypt files encrypted by ransomware?
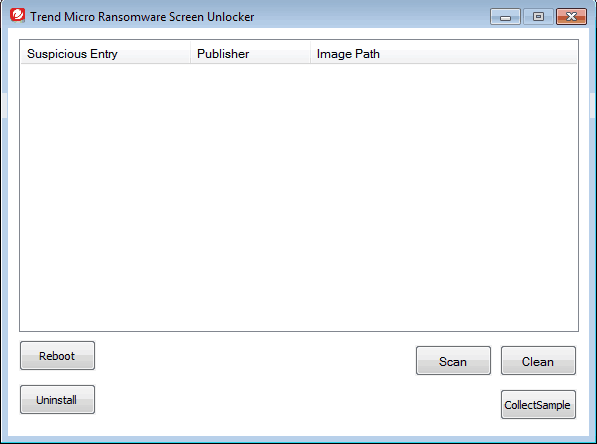
Trend Micro Ransomware Screen Unlocker Tool
Ransomware performs an attack in two different methods: lock screen and crypto. By locking the PC screen, ransomware limits a user from accessing the computer. The crypto method uses encryption algorithms such as AES to encrypt files. Trend Micro’s Ransomware Screen Unlocker Tool works to disable the lock screen types of ransomware.
The tool performs this in two different scenarios. In the first scenario, the tool could block normal mode while leaving safe mode with networking accessible. Here’s how to perform this operation:
- Open your PC in Safe mode with Networking.
- Download the Trend Micro Ransomware Screen Unlocker Tool and run the executable file.
- Extract the download file to install and reboot your PC in normal mode.
- Trigger the decryptor by pressing the following keys: Left CTRL + ALT + T + I. You may need to perform this key presses several times.
- If you see the Trend Micro Ransomware Screen Unlocker Tool screen, click scan to remove the ransomware files from your PC.
In another scenario, the tool may block both these modes.
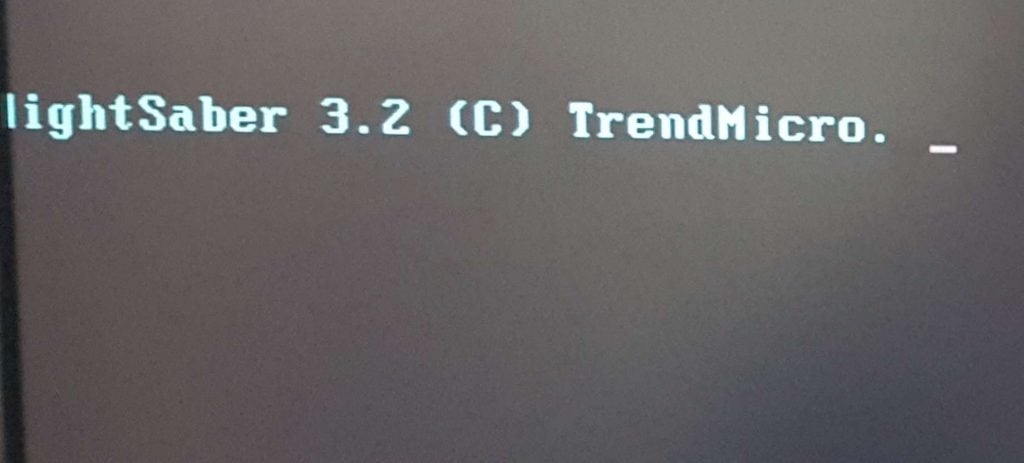
- Download the Trend Micro Ransomware Screen Unlocker Tool for USB on a non-infected computer.
- Insert a USB drive and run the executable file.
- Click Yes when you see the User Account Control window and select the USB drive before clicking Create.
- Insert the USB drive on the infected PC and boot that PC from the external drive.
- Upon reboot, the following screen will show up:
- If the infected PC fails to detect the USB drive, perform the following:
- Insert the drive to another USB port and reboot the PC.
- If the above step fails, use another drive.
- Open the infected PC and wait for the decryptor to remove the lock screen.
- Click Scan and then Fix Now.
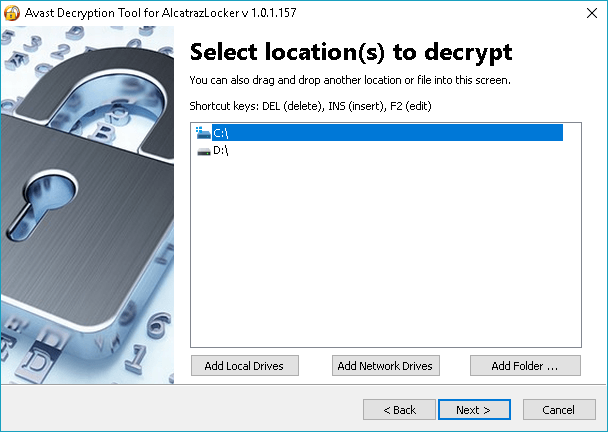
Avast Free Ransomware Decryption Tools
Avast’s decryption tools target many forms of ransomware. Earlier this month, the security vendor expanded the list with the addition of the decryptors for Alcatraz Locker, CrySiS, Globe, and NoobCrypt. Here’s a complete list of Avast’s decryption tools:
- Alcatraz Locker
- Apocalypse
- BadBlock for 32-bit Windows
- BadBlock for 64-bit Windows
- Bart
- Crypt888
- CrySiS
- Globe
- Legion
- NoobCrypt
- SZFLocker
- TeslaCrypt
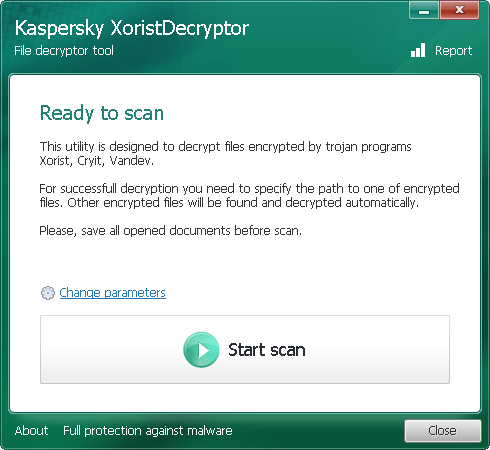
Kaspersky Ransomware Decryptor
Security firm Kaspersky designed a number of decryption tools for various ransomware threats, including Wildfire, Rakhni, Rannoh, and CoinVault.
- WildfireDecryptor tool
- ShadeDecryptor
- RakhniDecryptor
- Decryptor for Rannoh and associated ransomware
- CoinVault and Bitcryptor
- Xorist and Vandev
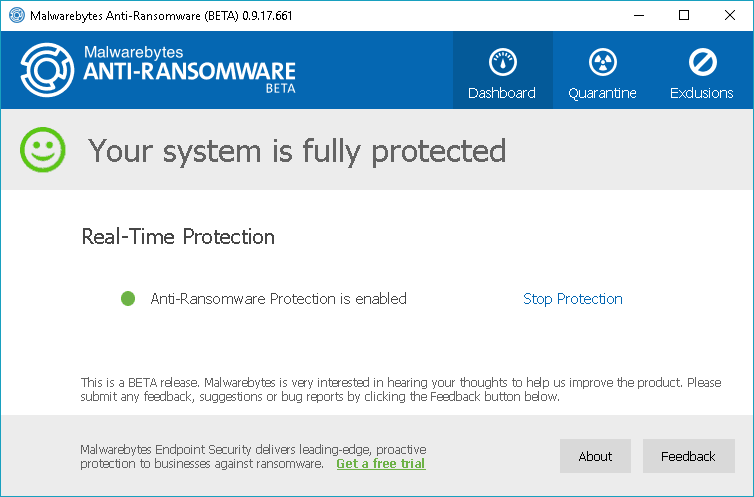
Malwarebytes Anti-Ransomware Beta
Malwarebytes Anti-Ransomware Beta runs in the background to analyze the behavior of file encrypting ransomware programs. The tool terminates threads on the computer that attempt to encrypt files. The program might contain a few bugs as it is still in beta stage.
The decryptor works for some of the notorious ransomware threats including Cryptowall, TeslaCrypt, and CTB-Locker. Download Malwarebytes Anti-Ransomware Beta.
Emsisoft Decryptors
Emsisoft, one of the leading security vendors today, also offers various free decryption tools to recover encrypted files without paying the ransom.
- NMoreira
- OzozaLocker
- Globe2
- Al-Namrood
- FenixLocker
- Fabiansomware
- Philadelphia
- Stampado
- 777
- AutoLocky
- Nemucod
- DMALocker2
- HydraCrypt
- DMALocker
- CrypBoss
- Gomasom
- LeChiffre
- KeyBTC
- Radamant
- CryptInfinite
- PClock
- CryptoDefense
- Harasom
Leostone Decryption Tool for Petya Ransomware
One of the most recent ransomware threats that hit many victims this year is Petya. The Petya Ransomware encrypts parts of a hard drive to prevent the victim from gaining access to the drive and the operating system.
Fortunately, Leostone has created a portal for Petya victims to generate the decryption key based on information that they provide from the infected drive. However, the tool works only if the Petya-affected drive is attached to another computer, from which the threat data will be extracted. It seems the tool is for advanced users only. But you can give it a try by downloading the tool from GitHub.
Final words
The number of victims is growing. Securelist’s KSN report indicates the total number of ransomware victims rose to 2,315,931 in March 2016 from 1,967,784 in April 2015. The financial implication of ransomware attacks could not be underestimated as well. According to Symantec’s Ransomware and Businesses 2016 report, the average ransom demand has now reached $679 from $294 last year. Thanks to the abovementioned free decryption tools, retrieving your files is only a few clicks away. If we missed any of the best ransomware decrypt tools, tell us about them in the comments.






User forum
0 messages