3 Best SSD Encryption Software [2024 Guide]
6 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Encrypting your HDDs or SSDs and keeping any data safe is essential nowadays.
- Add to this a backup image of your important files and you won't have any headaches in case of data loss.
- See all the options available on the market for data encryption in our Data Protection Hub.
- Don't forget about the utility of strong passwords, so look around in the Password Manager section.

If you work with a lot of data and sensitive information, you should avoid that these fall into the wrong hands. Consider, for example, the files and folders stored on a removable hard disk that gets lost or stolen.
The General Data Protection Regulation requires companies to adopt a series of security measures. Those should be applied for the encryption of data stored on notebooks, external hard drives, and other media.
But how is it possible to protect the files and folders stored on hard disks, external HDDs, or removable drives? How can you make sure that the data stored on these devices can only be accessed by the legitimate owner? How to reassure users that any third party will not access the data?
Luckily there are tools that you can use to encrypt HDDs or SSDs and keep any data safe.
?️ Quick tip:
Before creating the encrypted volume in the chosen unit, it is a good idea to create a backup copy of the unit contents.
This is only as a precaution, should anything happen to your original data. For this purpose, we recommend a free software such as AOMEI Backupper Professional.
This software help with system, disk, partition, and file backup, as well as with file synchronization and mirroring. It is currently one of the best tools to obtain an exact copy of your files.
AOMEI Backupper Professional supports both incremental and differential backups, and there’s also a command-line backup feature for advanced users.
You should store the image or backup on removable support or on another system. In this way, you can easily restore everything in case of problems.

AOMEI Backupper Professional
A simple and powerful solution to back up large files on any local or external drive, as well as in cloud.What software can I use to protect my hard disk?
VeraCrypt

VeraCrypt is a free opensource software considered as the direct successor of the TrueCrypt historian.
As opposed to TrueCrypt, VeraCrypt uses some improvements that allow you to trust on an even higher level of protection.
VeraCrypt allows you to create encrypted containers (volumes) within which you can save personal files and sensitive data. You can create the encrypted volumes on a local hard disk or on any removable hard disk or USB stick. You will only need to take care to mount the container after connecting the outdoor unit and disassembling it before removing it.
So, the application allows you to protect the contents of the hard disk and removable drives by fully encrypting it.
How to encrypt a hard disk with VeraCrypt
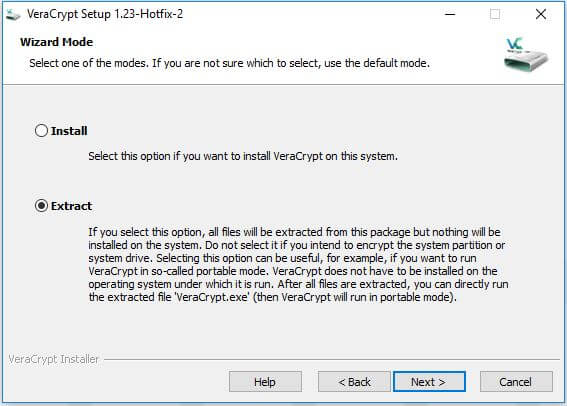
- Launch the VeraCrypt installer by selecting the Install option. You can choose the Extract option if you do not intend to protect the system partition or the system disk. Remember that the system partition is the one hosting the operating system.
By choosing Extract you can still create encrypted containers and protect non-system partitions. In this case, you can save the files necessary for the VeraCrypt operation in a folder of your choice. You will, then, use the program as “portable” software.
In case you decide to install VeraCrypt on your system, the application creates – by default – a recovery point.
2. Connect the removable drive or the hard disk to be protected.
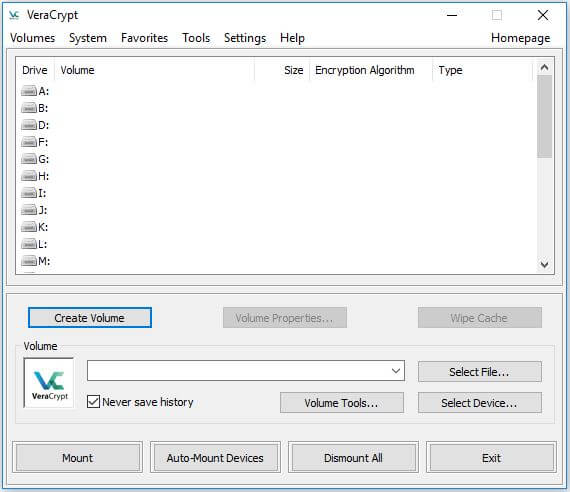
3. Start VeraCrypt.
4. Click on the Create volume button.
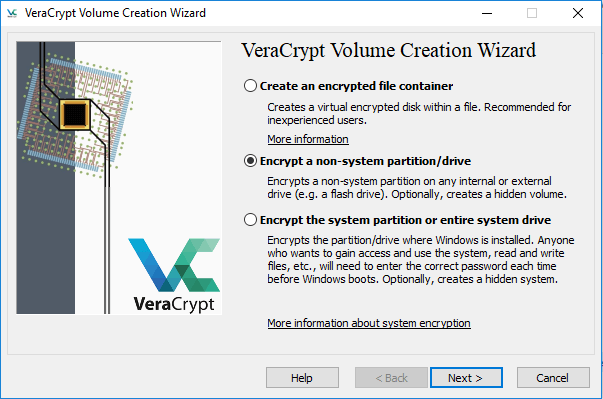
5. Click on Encrypt to non-system partition / drive then follow the instructions.
6. Choose between creating a VeraCrypt Standard volume and a hidden VeraCrypt volume.
For example, after you have encrypted the removable drive, nothing will happen when you connect it to your computer. To access the content of the storage unit, you will need to start VeraCrypt and mount it, using the interface.
You can mount or unmount then the encrypted volumes. If you choose the first option, you can to access the respective content. Vice versa, you make it impossible to access by unauthorized persons.
You should choose an encryption algorithm for data and a keyword (passphrase) that you will take care to keep jealously. Why so? To create a container encrypted volume (Create an encrypted file container option) or to protect a removable drive or an external hard drive.
How do I protect the system partition with VeraCrypt?
Alternatively, you can choose to encrypt the system partition or the entire system drive option by installing VeraCrypt. It protects the contents of the hard disk where the operating system is installed by encrypting all the files and folders.
This way, the content of the hard disk will not be readable by third parties that do not have a personal password.
VeraCrypt will encrypt automatically and completely all files, including temporary files, files used to manage the hibernation procedure (automatically turn on and off the computer), swap files, and so on.
Using encryption on the system partition or disk involves activating a pre-boot authentication mechanism.
Before loading the operating system, VeraCrypt asks to specify the passphrase or the personal keyword chosen when encrypting the unit.
Next:
- Click the Create Volume button.
- Select the Encrypt the system partition or entire system drive.
- Select Normal.
- Choose whether to encrypt only the partition containing the operating system or the entire hard disk.
- Determine whether you want to encrypt the area, if any, located at the end of the hard disk, used by RAID systems, tools for system recovery, troubleshooting, diagnostics, and so on.
- Create an emergency disk (Rescue Disk). You can use this disk to restore the startup of the operating system if you forget the passphrase or in case of malfunctions.
Windows’ built-in BitLocker

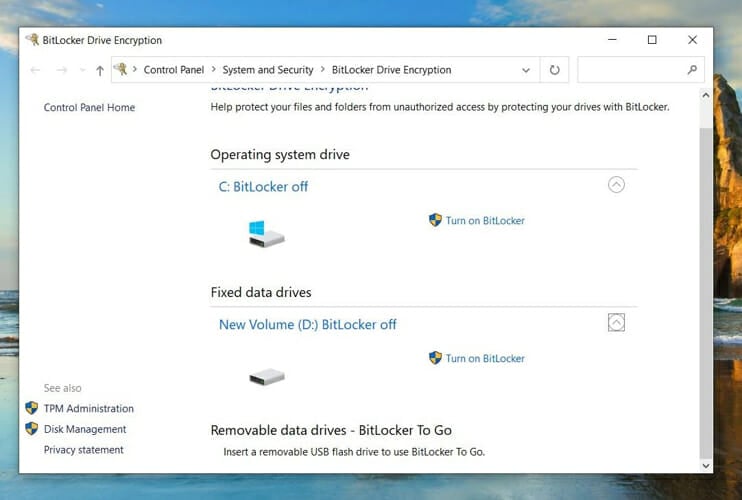
Windows 10, as well as older OS versions such as the Ultimate and Enterprise editions of Windows Vista and Windows 7, in the Pro and Enterprise editions of Windows 8 and Windows 8.1, on Windows Server 2008, you can encrypt and protect your hard disk using a built-in tool, BitLocker.
To enable it on your system, type BitLocker in the taksbar search box, click on Manage BitLocker. Choose to turn on the option on the desired drive.
You should know that Windows Vista and Windows 7 do not allow Bitlocker to start without the Trusted Platform Module (TPM) chip.
During the configuration phase of Bitlocker, Windows will ask you if you want to unlock the system by connecting a USB stick or typing a password.
The following steps are quite clear. They allow requesting encryption of the data actually written on the disk or even the encryption of free space.
There you have, two of the best SSD encryption software solutions available on the market. Let us know which one you installed and why.






User forum
0 messages