TPM Windows devices aren't that safe, according to researchers
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- Even though Microsoft preached the enhanced safety we were going to receive via TPM chips, an attack is not even remotely impossible.
- If one of our windows 11 devices were to fall into the wrong hands, the device itself and the network it's connected to would be compromised.
- Experts proved that, with the right set of skills, even the TPM 2.0 security chips can become easy prey for malicious entities looking to extract our data.
- Microsoft might want to take a closer look at these security features and maybe even revise its strategy, while there is still time do so.

Needless to say, ever since the Redmond tech company first announced Windows 11 as the future OS, there has been endless talk about some of the hardware requirements that devices need to fulfill.
Many didn’t agree with the imposed TPM 2.0 restrictions and this subject has sparked reactions of all kinds from Windows users.
Microsoft held its ground and kept reassuring people that this TPM requirement is for their own safety, because of the enhanced level of protection it was going to offer.
However, some experts recently found that even with these security chips in place, we still can’t be entirely safe from malicious entities, on the off chance that someone gets their hands on our Windows 11 device.
We’re not as safe as Microsoft wants you to think
The tech giant showed an iron will when it came to not cracking under public pressure, especially after the backlash that the TPM 2.0 requirement brought with it from the community.
They advertised this hardware feature as it if was their own and said that users were going to be protected because of this tiny chip.
Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper-resistant, and malicious software is unable to tamper with the security functions of the TPM.
Experts from Dolos Group found out that, in fact, if one of us were to lose his laptop or have it stolen, TPM could do little to prevent hackers from wreaking havoc.
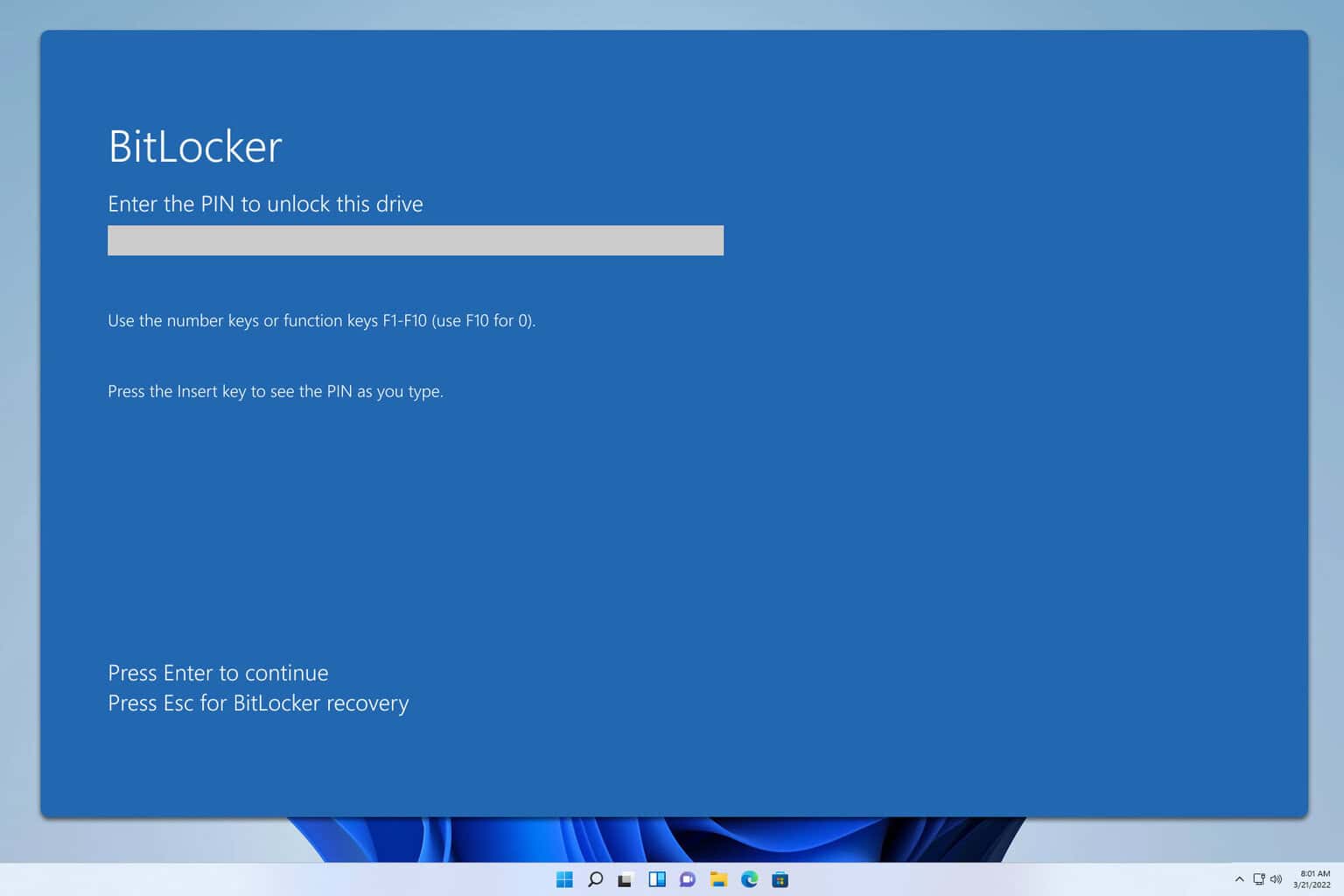
At the time of this writing, BitLocker does not utilize any encrypted communication features of the TPM 2.0 standard, which means any data coming out of the TPM is coming out in plaintext, including the decryption key for Windows. If we can grab that key, we should be able to decrypt the drive, get access to the VPN client config, and maybe get access to the internal network.
By using this exploit together with other ingenious schemes, researchers were able to take a stolen corporate laptop (as a scenario) and effectively gain access to its associated corporate network, leaving data exposed and vulnerable.
As they further described, after cracking open said laptop, a pre-equipped attacker would use a SOIC-8 clip instead of individual probes, in order to compromise the TPM security chip.
The clip would make it extremely simple to connect to the chip and shave a couple of minutes off a real-world attack.
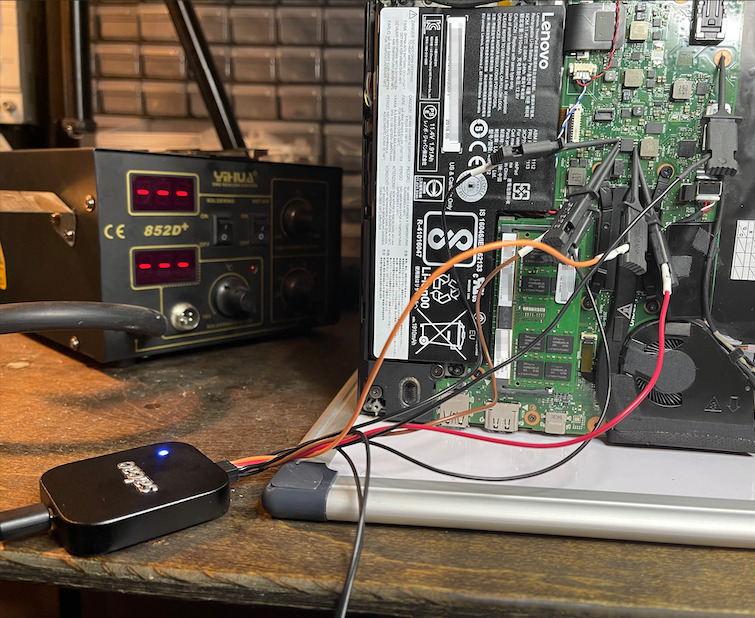
The entire process is explained in full detail and it is an interesting read if you have a vast technical background and are into this kind of knowledge.
This is disconcerting news, considering that Microsoft made such a big deal about us upgrading to devices that already have such security features integrated.
With that being said, the Redmond-based tech company could do a better job at offering a more secure future for BitLocker, one where such hacking methods are no longer possible.
You might also like to know that you can install Microsoft’s upcoming operating system even without the imposed TPM requirement.
What is your take on this whole situation? Share your opinion with us in the comments section below.








User forum
0 messages