Windows Hello will soon be a FIDO2 Certified authenticator
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
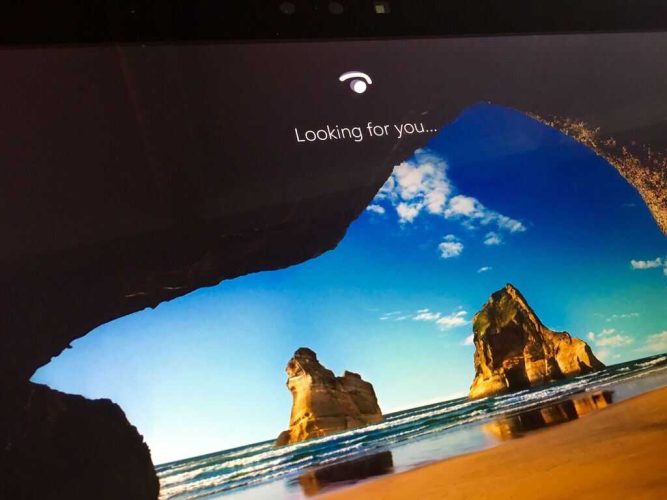
Microsoft’s Windows Hello will officially become a FIDO2-certified authenticator service in the next release of Windows 10. This means that going forward, all Windows 10 devices with Windows Hello biometics will be FIDO2-certified out of the box as long as long as they are running the Windows 10 May 2019 update or later.
For those unfamiliar, FIDO2 project is an effort between the FIDO Alliance and the World Wide Web Consortium with the purpose of creating a simpler yet strong authentication service for web applications. FIDO2-compliant services use cryptographic security that is “far superior to passwords” according to the organization, which it promises will further protect users from phishing and password theft.
Microsoft has been pushing Windows Hello and passwordless login of MSA accounts to greatly boost security and convenience for its consumers. Back in November, the company added support for FIDO2 security keys as a way to authenticate one’s Microsoft account. With Windows Hello now following the same standards, customers should be able to feel more at rest about the security of their private data.
Microsoft is also bringing passwordless login via Windows Hello to the Mozilla Firefox web browser starting in the Windows 10 May 2019 update. The company expects the same functionality to eventually make its way to Chromium-based web browsers, including the new Microsoft Edge that is still under development.
The tech giant also recommends those to use the Microsoft Authenticator app, which it says is “built on secure technology similar to Windows Hello.” While it’s expected to take time for Windows Hello and Microsoft Authenticator to totally replace passwords altogether, the company recommends developers to look into supporting FIDO2 authentication in their web applications as soon as today.

User forum
0 messages