49 million affected in Dell's latest breach, data was reportedly put on the dark web
Dell says, there's no significant risk
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

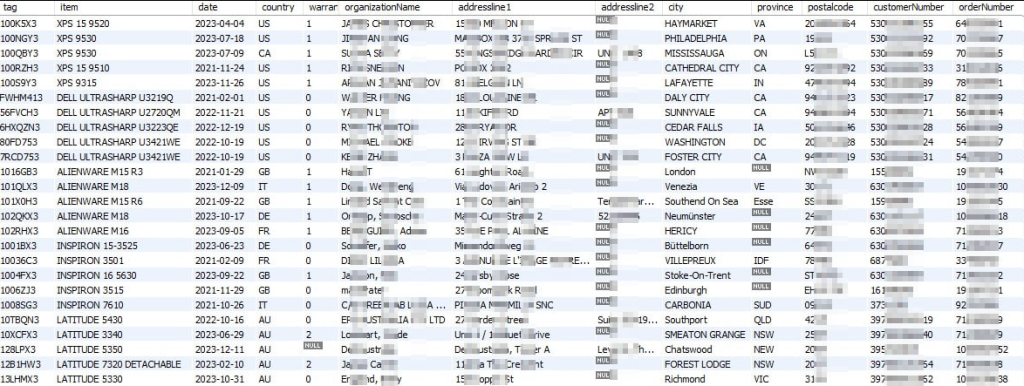
Dell became the latest victim of a data breach, and the personal details of roughly 49 million users were exposed to threat actors. The details available to threat actors include name, address, service tag, date of order, item description, and warranty information.
Dell started sending out emails to affected customers yesterday, acknowledging the breach. The notification letter reads,
We are currently investigating an incident involving a Dell portal, which contains a database with limited types of customer information related to purchases from Dell. We believe there is not a significant risk to our customers given the type of information involved.
It did not include financial or payment information, email address, telephone number or any highly sensitive customer data.
While Dell did not disclose the actual number of customers whose data was stolen or what caused the breach, the email sent to users suggests that one of the Dell portals was compromised.
Stolen data was reportedly put for sale on the dark web
In the last week of April’24, much before Dell admitted to the breach, Daily Dark Web reported about a threat actor selling customer records from Dell on a dark web forum.
In a post titled This data includes 49 million customer and other information systems purchased from Dell between 2017-2024, the threat actor claimed to be the only one in possession of the details.
The screenshot of the data shared by Daily Dark Web aligns with the information Dell confirmed was stolen from one of its portals.
BleepingComputer reports that the data has since been taken down from the forum, suggesting that it might have been purchased by someone. However, we can’t independently verify that!
While Dell has downplayed the data breach and claims that there are no significant risks involved, we recommend that you remain wary of any too-good-to-be-true promotional offers received via physical posts. That’s a standard practice by threat actors!
Previously, in a similar instance, threat actors, after acquiring the mailing addresses of customers, sent malware-loaded USB drives. As soon as it was connected, the malware transferred to the PC.
If you have any similar tips for our readers, share them in the comments section below.

User forum
0 messages