Windows Audit Policy: Best Practices for Secure IT Systems
Learn to do Windows auditing right
11 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The Audit Policy process controls various value changes in several domains, including Active Director and the network’s file systems.
- Any firm may comply with the full range of data security regulations and lessen the damage a data breach can have with the help of a Windows auditing procedure.
Want to learn about Windows Audit Policy best practices? Here is all you need to know. An essential element of Windows auditing is the so-called file integrity monitoring service, also called Windows changing auditing.
Quick access to best practices for a Windows Audit Policy makes a difference in the long term. So, read through this guide.
What is an Audit Policy?
This process manages a variety of value changes across multiple domains. Some include Active Directory, Exchange, SQL, and the file systems found on your network.
Covering these aspects and analyzing security and system events allows companies to reduce the possibility of unauthorized access to data. It also improves the company’s overall capability to deal with system security and management threats.
What does the Audit Policy enable?
A thorough Windows auditing process ensures that any organization can respect the entire set of data protection requirements. They also will preemptively react to possible threats and dampen a data breach’s impact.
As in the case of other complex processes, a few key elements will ensure that the process goes smoothly and that the chosen implementations/changes are managed from one central hub.
Today’s guide will uncover all the secrets to achieving a well-rounded Windows Audit Policy without too much hassle. We also simplify the process considerably using specialized software.
In which order should we enable auditing?
The order in which the auditing process should be enabled will depend on the exact type of threat. There is, thus, no single answer to this question.
It is essential to note that the auditing process has two critical areas to cover:
- Active Directory Auditing– This feature allows users access to specific information, topics, folder, files, and data based on their identity. Active Directory will be the preferred target for cyber-attacks and malicious third parties.
- Windows Policy Auditing – Tracking this feature mainly covers the Windows Policy changes using Group Policy Objects. These can be set up and used depending on the circumstances. An overview of all access points and privileges by specific users helps hone in on the problem and eliminate it.
Generally, Microsoft has created a set of 10 laws of security administration, which should be respected entirely for business-wide coverage of any external threats.
What are Windows Audit Policy best practices?
1. For Active Directory
1.1 Manage and edit the Active Directory Security Groups
The most common attacks are targeting members of Domain Admins, Administrator Groups, and Enterprise Admins in Active Directory. However, this is because a domain account with admin-level access can even modify the access of VIP accounts,
So, you should limit access to these groups to avoid any issues.
1.2 Remove any inactive users in AD
Suppose any inactive users still have access to your Active Directory environment. In that case, it is best to remove them ASAP. This is a standard method malicious third parties use to access critical data without causing suspicion.
1.3 Keep track of Local Administrators
Users with administrator rights have access to a significant part of your organization. So, keeping track of their access level and managing it accordingly can have a considerable impact.
- Domain accounts that have administrator-level access to a variety of computers – Even though sometimes these accounts might not have access to high-privilege groups on Active Directory, they might have admin access to many servers inside the Windows infrastructure.
- VIP domain accounts – These have access to various intellectual property and other sensitive information from network users. Any account enabling the attacker to access vast data can be considered a VIP domain account. Some examples include executive accounts with wide-range access and accounts from help-desk employees, legal staff, product planners, or researchers.
1.4 Avoid using GPOs to set passwords
Group Policy Objects, can create accounts and set passwords for regular users and Local Administrators within Active Directory.
Also, attackers can use them to gain access to the data found within Active Directory, causing a large-scale data breach.
It is of paramount importance that system admins have the capability of spotting and reporting these situations.
1.5 Audit DC (Domain Controller) logons
As mentioned in the previous step, having system admins that can have an overlook over the entire domain controller structures is of paramount importance.
Lastly, most organizations focus on Enterprise and Domain administrators, but having access to other groups through the DC is a huge threat as well.
1.6 Use protection for the LSASS
As attackers can use various hacking tools to target the Local Security Authority Subsystem Service (LSASS) to steal users’ credentials, it is recommended that security measures are taken concerning this.
1.7 Manage your password policy with care
A firm password policy for your users will ensure that hackers will not have the time to gain access.
Essential elements regarding password policies:
- Need to change passwords frequently
- Use an automated system that allows passwords to expire
- Employ a password expiration reminder software
- Use easy-to-remember passphrases instead of complex passwords (which pose a security threat when being stored on the HDD or paper)
1.8 Carefully manage any Nested Groups
Administrators tend to create groups nested in other groups to control users’ access levels quickly, but this can cause a variety of security risks.
A complicated security tree structure can confuse admins and thus may lead to data breaches.
Lastly, to successfully manage this element, it is crucial always to keep track of how many groups there are and how many groups are nested within them.
1.9 Remove Open Access for users
Suppose open access identifiers like Everyone, Domain Users, or Authenticated Users are utilized when creating group policies. In that case, that can lead to privileges being added to users without intent by elements such as file sharing.
Hackers can use these security identifiers to hone in on the exact user with the most significant access level and thus cause the possibility of a security breach.
1.10 Audit server logon rights
Because Local Security Policies are under the control of Group Policy, it is essential to manage user rights accordingly.
So, this principle applies directly to situations where non-admins can access a function that the admins should cover.
If these functions are not constantly monitored and managed, hackers can use them to gain access to sensitive information across the organization.
1.11 Employ the principle of Least Privilege for AD Security
To employ this principle correctly, you must configure your AD Security to allow users only the minimum amount of access to the database and other essential functions.
1.12 Use a backup for your AD directory
A stable and robust backup process is critical to avoid any data loss that can endanger your entire organization.
1.13 Enable security monitoring for AD
Proactively keeping an eye out for any changes that appear in your Active Directory setup is extremely important.
To do this most efficiently, we will need to employ some useful tools, which we will cover in the next section:
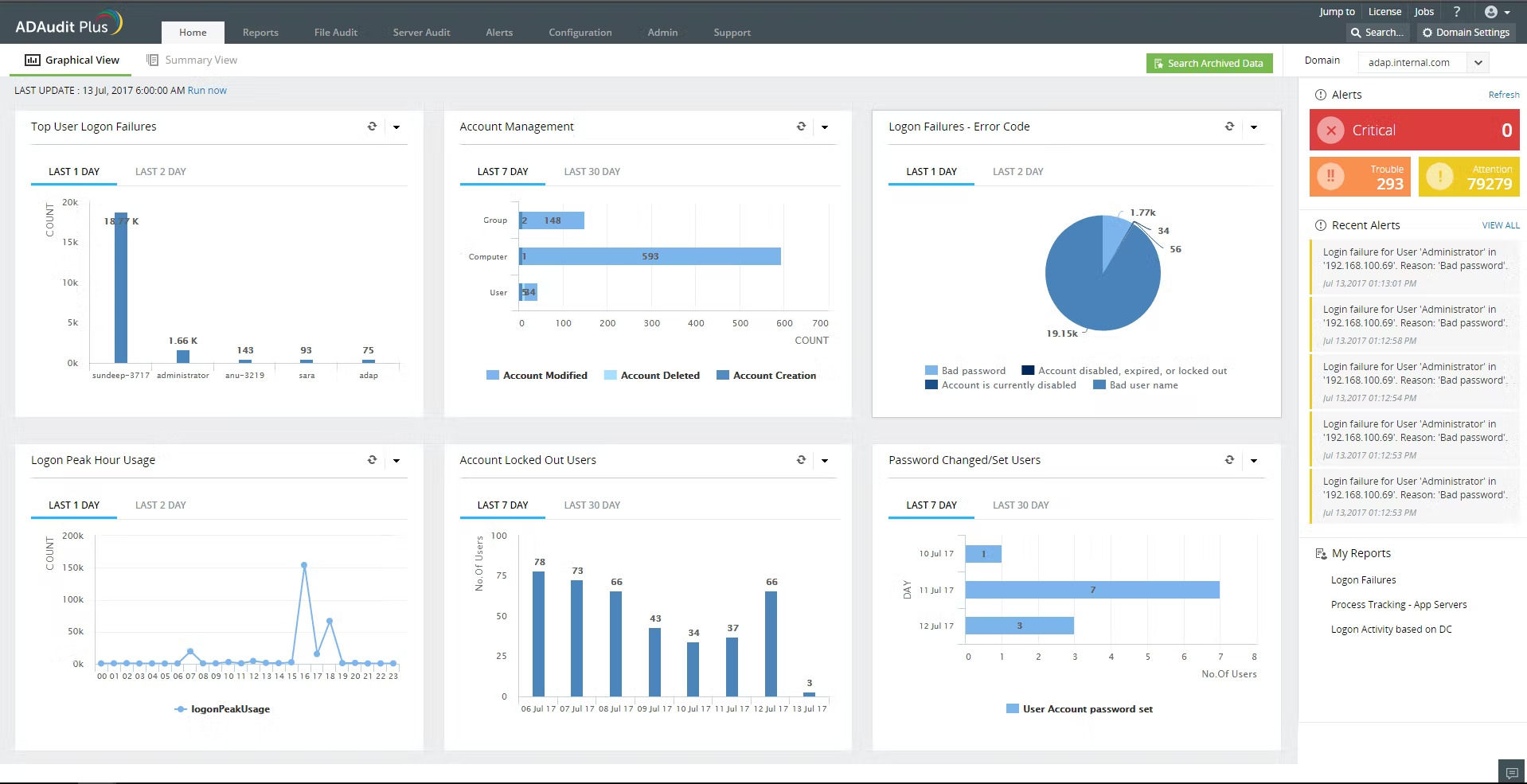
What software tools can I use to simplify the process of monitoring Active Directory?
ADAudit Plus – Excellent all-round AD monitoring options
ADAudit Plus simplifies the process of monitoring Active Directory by providing a centralized and automated platform for tracking and reporting on user and group activity, security changes, and resource access.
It eliminates the need for manual log reviews and multiple tools to accomplish the same task. With ADAudit Plus, administrators can view real-time and historical data on user logins, group memberships, permissions, and GPO changes and receive alerts on suspicious activity.
Additionally, the software provides an easy-to-use interface with detailed and customizable reports and the ability to export data to various formats.
It also allows for monitoring multiple domains and forests from a single console, making it easier to manage and monitor large-scale AD environments.
Overall, ADAudit Plus streamlines the process of active directory monitoring by providing a comprehensive and user-friendly solution that allows administrators to identify and respond to potential security threats easily.

ADAudit Plus
By offering a consolidated and automated platform for tracking, ADAudit Plus streamlines the process of active directory monitoring.ADManager Plus – Great all-in-one AD management
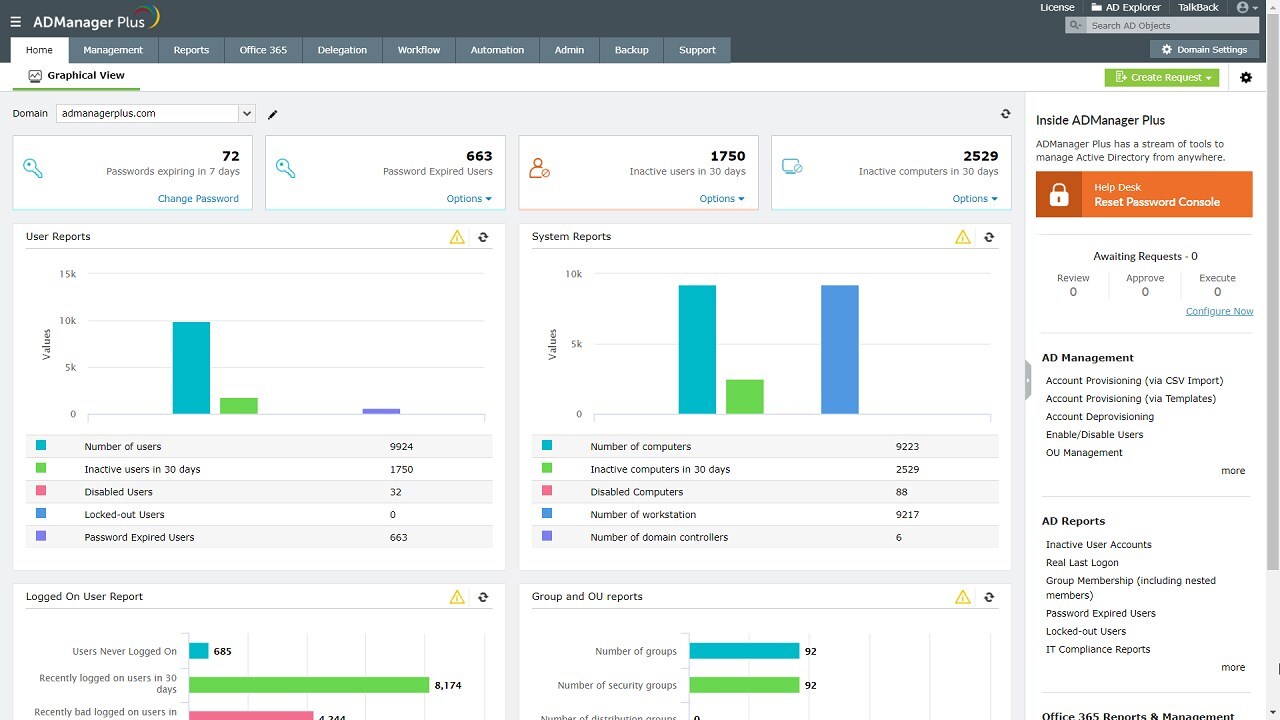
AD Manager Plus is a tool that simplifies the process of monitoring Active Directory by providing a centralized platform for managing and monitoring AD environments.
It allows administrators to easily view and manage user accounts, groups, and other AD objects and monitor and track changes to the AD environment.
Additionally, it provides various reporting and auditing capabilities to aid compliance and security.
With ADManager Plus, administrators can perform everyday AD tasks such as creating and managing users and groups, resetting passwords, and delegating permissions with just a few clicks. It also allows for bulk actions, saving time for repetitive tasks.
Overall, ADManager Plus aims to make the process of monitoring and managing Active Directory more efficient and streamlined.

ADManager Plus
This solution simplifies monitoring Active Directory by offering a consolidated platform for administering and monitoring AD deployments.ADSelfService Plus – Perfect for real-time monitoring
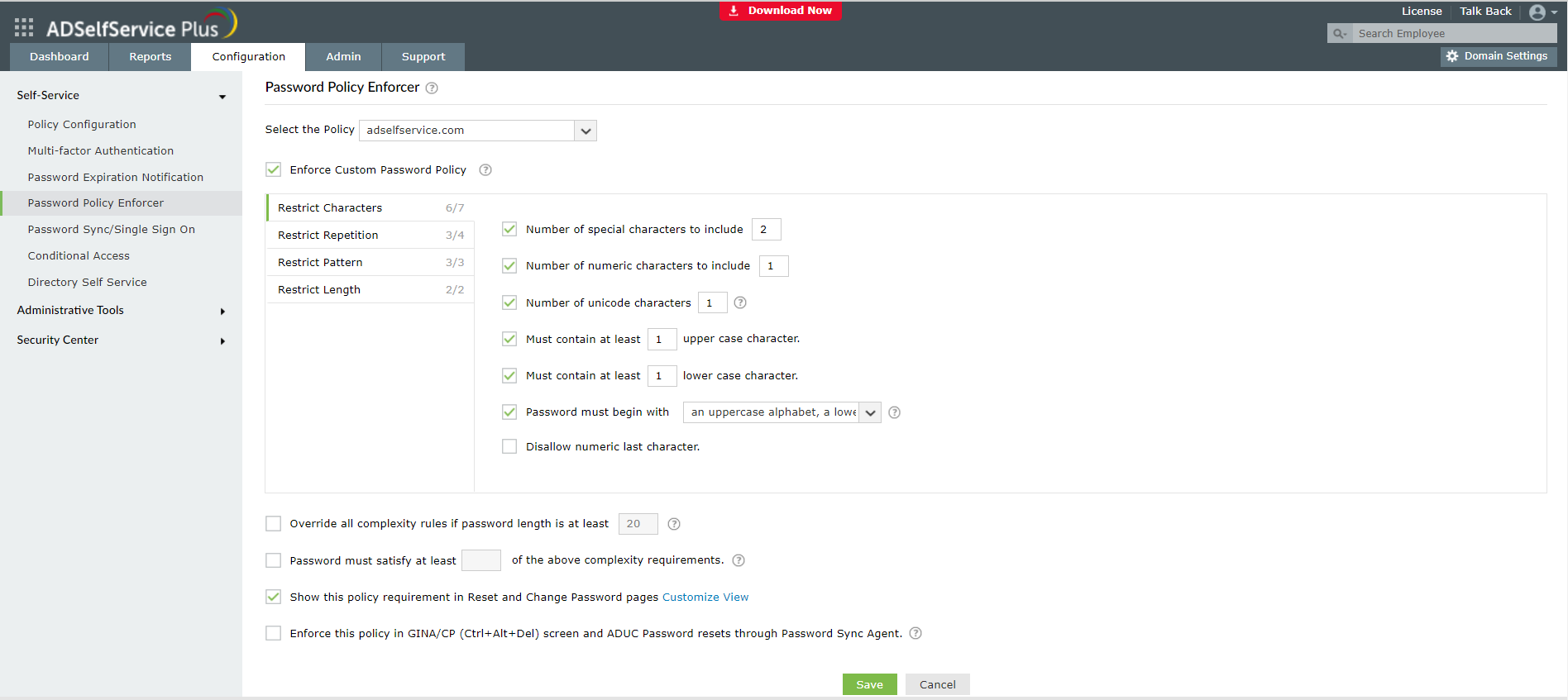
ADSelfService Plus simplifies the process of monitoring Active Directory by providing a centralized platform for monitoring and managing various aspects of AD.
This includes real-time monitoring of user login and logoff activities, tracking user account changes and password resets, and generating detailed reports on AD user and group information.
Additionally, it provides automated alerts and notifications for specific events, such as failed login attempts or password expiry, which can help IT administrators quickly identify and resolve issues.
Overall, ADSelfService Plus helps streamline the process of monitoring AD by providing a comprehensive set of tools and features that allow IT administrators to monitor and manage AD users and groups easily.
ADSelfService Plus
By offering a consolidated platform for controlling and monitoring different parts of AD, ADSelfService Plus streamlines the monitoring process for Active Directory.2. For Windows Policy Auditing
2.1 Regularly review and update audit policies
Windows Policy Auditing is an ongoing process, and it’s essential to periodically review and update audit policies to ensure they are still relevant and appropriate.
This includes identifying new threats and vulnerabilities and determining which events should be audited based on the current security needs of the organization.
2.2 Use built-in audit policies
Windows has several built-in audit policies that monitor many events, including logon/logoff events, object access, system events, etc.
These policies are designed to be comprehensive and provide a good starting point for most organizations.
2.3 Enable auditing for sensitive areas
It’s essential to enable auditing for sensitive areas, such as the system registry, security event logs, and privileged user accounts.
Because, this will allow you to monitor and track activities related to these areas, which can help detect and respond to security incidents more quickly.
2.4 Use centralized log management
Centralized log management is a best practice for Windows Policy Auditing.
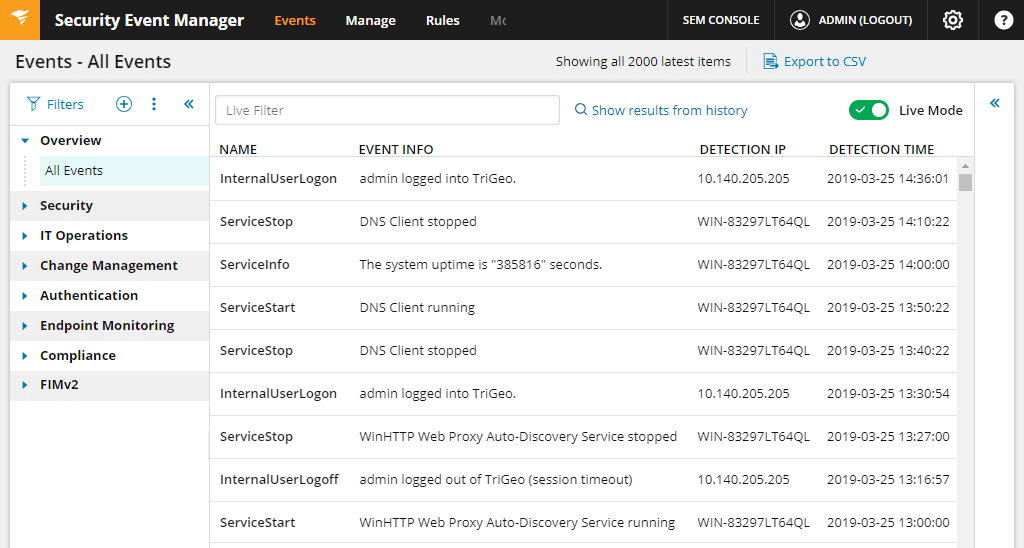
This allows you to collect, store and analyze all logs in a single location, which makes it easier to identify and respond to security incidents. This is one of the fundamental Windows Audit Policy best practices.
2.5 Test your audit policies
Regularly testing your policies can help ensure they are configured correctly and capture the events and information needed to detect and respond to security incidents.
This can include testing the policies in a lab environment or simulating different security incidents to see how the audit policies respond.
2.6 Monitor and review logs
Monitoring and reviewing the logs generated by the audit policies regularly is essential. This can help identify potential security incidents early and allow IT administrators to respond quickly and effectively to minimize the impact of the incident.
2.7 Regularly backup the audit data
Regularly backing up the audit data helps Windows Policy Auditing in several ways. First, it provides a historical record of events that can be used to investigate past security breaches or other issues.
Also, this can help identify patterns or connections between different events, which can aid in determining the cause of a security incident.
Additionally, regular backups can ensure that the data is not lost in case of system failure or other unexpected issues. And finally, this can be critical for maintaining an accurate record of events and can be necessary for compliance reporting.
2.8 Keep software updated
Finally, keeping software updated helps Windows Policy Auditing by reducing the risk of security breaches and other issues.
Software updates usually include security patches that address known vulnerabilities or bugs that attackers can exploit. By updating software, organizations can reduce the risk of these vulnerabilities and minimize the potential for a security incident.
Additionally, software updates can include new features and improvements that can help enhance the system’s security. Furthermore, it will add new auditing capabilities or improved logging functionality.
In conclusion, Windows Audit Policy best practices are essential for ensuring the security and integrity of an organization’s IT systems.
Hence, by implementing these best practices, organizations can ensure that they are capturing the necessary information to detect and respond to security breaches. Also, they are complying with industry standards and regulations.
Lastly, adopting these best practices can help organizations simplify the process of Windows Audit Policy and improve their overall security posture.

User forum
0 messages