Latest .NET updates patch the Visual Studio Remote Code Execution Vulnerability
The CVE-2024-21409 vulnerability can cause data breaches for your organization
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more

Microsoft issued updates for .NET 6, .NET 7 and .NET 8 to address the CVE-2024-21409 listed as an important vulnerability for .NET and Visual Studio Remote Code Execution.
A Remote Code Execution (RCE) attack allows an attacker to execute malicious code on an organization’s computers or network. This capability to run code controlled by the attacker can serve multiple objectives, such as installing further malware or exfiltrating confidential information.
RCEs attacks are very common means for attackers nowadays to steal data and break into Government and organizations systems.
How do I patch my .NET to avoid security issues?
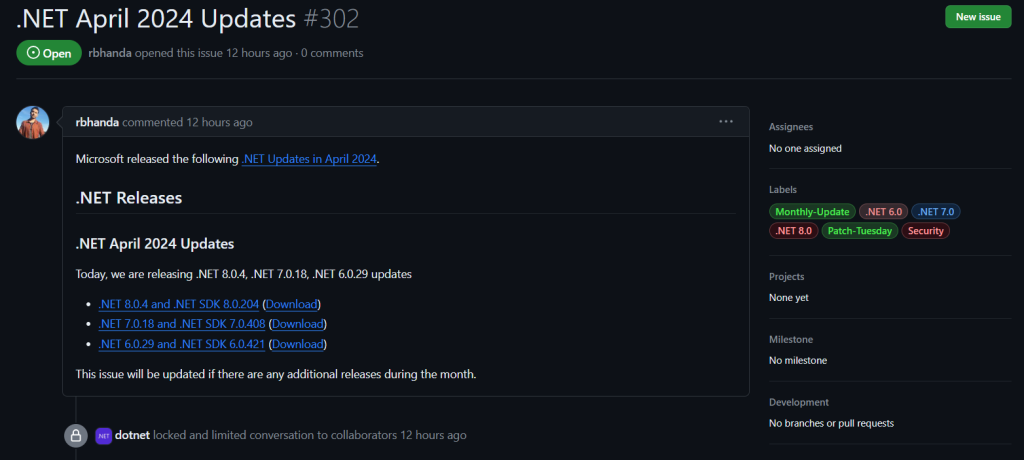
The latest .NET updates, .NET 8.0.4, 7.0.18, .NET 6.0.29 for Windows, macOS, and Linux, for x86, x64, Arm32, and Arm64 are available for download from the dedicated GitHub page.
However, you may also use the Windows Package Manager CLI (winget) commands to install them:
- To install the .NET 8 runtime:
winget install dotnet-runtime-8 - To install the .NET 8 SDK:
winget install dotnet-sdk-8 - To update an existing installation:
winget upgrade
Microsoft also warns about a use-after-free vulnerability in WPF which may result in Elevation of Privilege when just by viewing untrusted documents. We recommend updating .NET as soon as possible to avoid these security issues.
You should also be aware that .NET 7 will soon reach end of support. The apps will still run but Microsoft recommends an upgrade.
Did you encounter any problems with the updates? Let us know in the comments section below.

User forum
0 messages