Microsoft will soon block more files extensions on Outlook on the web
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
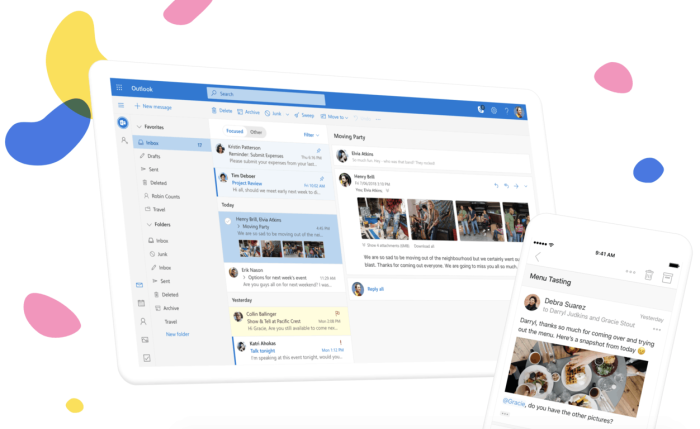
In a move that appears to be focused on security, Microsoft’s Outlook on the web will be increasing the number of blocked file extensions that can be accessed through the online email service.
Last week the company explained in a post on its Exchange Team Blog, that its BlockedFileType property will now be “adding several additional file extensions.”
For those interested, the following file extensions being added to the list are as follows:
“.py”, “.pyc”, “.pyo”, “.pyw”, “.pyz”, “.pyzw”
“.ps1”, “.ps1xml”, “.ps2”, “.ps2xml”, “.psc1”, “.psc2”, “.psd1”, “.psdm1”, “.cdxml”, “.pssc”
“.appref-ms”
“.wsb”
“.cer”, “.crt”, “.der”
“.jar”, “.jnlp”
“.appcontent-ms”, “.settingcontent-ms”, “.cnt”, “.hpj”, “.website”, “.webpnp”, “.mcf”, “.printerexport”, “.pl”, “.theme”, “.vbp”, “.xbap”, “.xll”, “.xnk”, “.msu”, “.diagcab”, “.grp”
Microsoft is assuring users that the newly blocked file extensions were rarely used by organizations and shouldn’t affect most of its user base. Going forward though, anyone who sends or received any of the above file extensions through attachments will relieve a notification that will not be able to download the attachment.
However, for any person or organization fearful of being accidentally blacklisted, Microsoft does offer a manual whitelist ability for file extensions to be added to AllowedFileType lists with the following script:
$policy = Get-OwaMailboxPolicy [policy name]
$allowedFileTypes = $policy.AllowedFileTypes
$allowedFileTypes.Add(“.foo”)
Set-OwaMailboxPolicy $policy -AllowedFileTypes $allowedFileTypes
Users can also leverage the following shortcut, Set-OwaMailboxPolicy -Identity “<Policy Name>” -AllowedFileTypes @{Add=”.foo”}
Lastly, for anyone looking to salvage their file extensions from Microsoft’s predetermined blacklist, users can apply the following script to bump the file extensions out of lock and key in the future.
$policy = Get-OwaMailboxPolicy [policy name]
$blockedFileTypes = $policy.BlockedFileTypes
$blockedFileTypes.Remove(“.foo”)
Set-OwaMailboxPolicy $policy -BlockedFileTypes $blockedFileTypes
If, you’re still confused by the change or wondering why a certain file extension was added to the Outlook on the web’s blacklist, read the company’s individual explanations on their inclusions here.


User forum
0 messages