Chrome 124 and Edge 124 can't handle TLS connections due to quantum-resistant encryption key
In fact, the problem is not the browser, but the web server
3 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
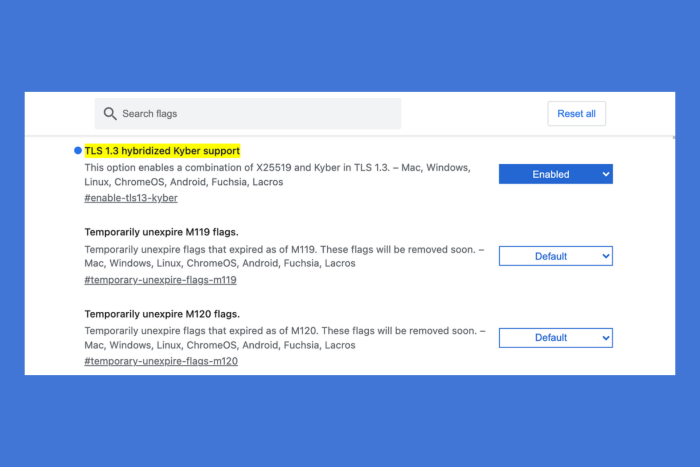
Chrome’s latest version, 124, comes with a new, quantum-resistant encryption mechanism known as X25519Kyber768. This feature, designed to protect against future quantum computer attacks, might be a double-edged sword, causing more immediate connectivity issues than it aims to prevent.
An admin posted this issue on Reddit, pointing to the TLS 1.3 Hybridized Kyber Support:
Apparently Chrome 124 changed a setting “TLS 1.3 Hybridized Kyber Support” from disabled to enabled as the default. This appears to break the TLS handshake for servers that do not know what to do with the extra data in the client hello message.
If you mysteriously have a broken web application and the server is sending a reset directly after the client hello, try turning this setting off. In our testing IE mode works as well, probably because this extra data is not transmitted in IE mode while it is in normal Edge.
Later in the thread, another user confirmed that he has the same problem on Edge version 124.
Why do we need TLS key encapsulation in Chrome and Edge?
Google embarked on this quantum-resistant journey back in August, testing waters with a post-quantum secure TLS key encapsulation mechanism. Fast forward to now, and it’s a standard feature in Chrome 124, aiming to shield users from potential store now, decrypt later attacks. This type of attack is where bad actors collect encrypted data with the hope of decrypting it in the future when quantum computing or new decryption methods become available. The idea is to future-proof our digital communications against quantum cryptanalysis, a noble goal, indeed.
However, as with any major technological shift, there are growing pains. System administrators from various corners of the digital world have reported dropped connections post-update, a problem stemming not from a bug in Chrome, but from web servers that can’t handle the new, larger ClientHello messages required for post-quantum cryptography. This issue isn’t isolated to obscure parts of the internet; it affects a wide range of devices and services, including those from big names like Fortinet, SonicWall, Palo Alto Networks, and AWS.
The solution is a bit of a patchwork for now. Users experiencing these connectivity issues can disable the TLS 1.3 hybridized Kyber support in Chrome via the chrome://flags/#enable-tls13-kyber flag. System administrators, on the other hand, are encouraged to reach out to their vendors for updates to make their servers and network devices post-quantum-ready. Microsoft Edge users, facing similar troubles, have been given guidance on controlling this feature through Edge group policies.
It’s clear that the road to quantum-resistant encryption is a bumpy one, with immediate challenges overshadowing long-term benefits. Google has hinted at a future where disabling this feature won’t be an option. And let’s face it, security in the digital world is a race around the clock to counter present and even future attacks.
We’ve heard about this story from Bleeping Computer. If you encountered this issue yourself and have a better solution, share it with other readers in the comments below.


User forum
0 messages