What is Ryuk ransomware and how to protect yourself from it?
5 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Key notes
- The scamming industry has evolved so you do need protection from Ryuk ransomware.
- This scheme is based on stealing your data and threatening to destroy it if you don’t pay a certain amount of money.
- You can try to get rid of this problem by installing a malware removal tool from ESET.
- Protecting your business data with a 3-2-1 backup strategy will prevent losing your data.

Cyber criminals are using a new form of ransomware for targeting large businesses and getting money from them.
Ryuk group ended up earning $4 million by installing malicious encryption software on high-value targets in a very short period.
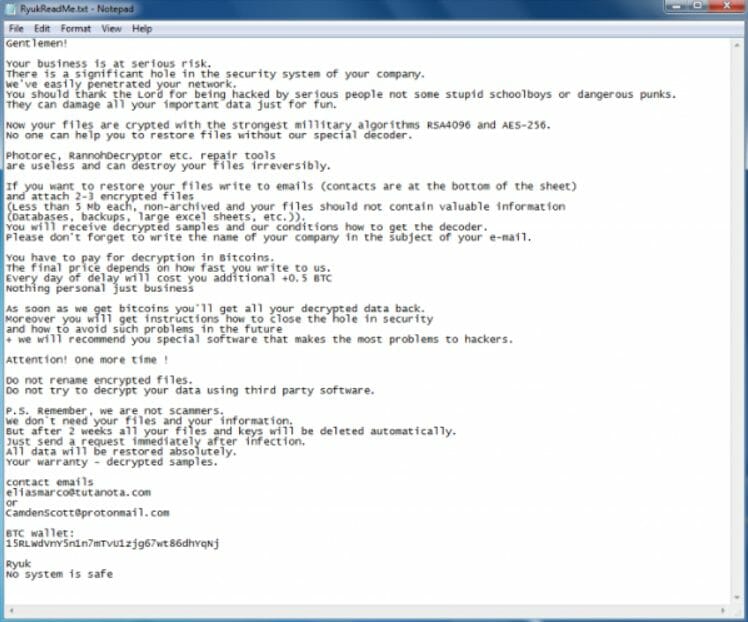
Several notable attacks have been reported during the past few months. Take a look below at how this ransomware note looks like.
Users should be trained to use an email protection platform that is able to recognize the malicious spams in the first attempt.
These malicious scripts should be stopped from installing on the system by using anti-exploit technology.
The companies should also invest in effective security solutions and update them frequently.
Network segmentation is another approach that can be used to reduce the damage from a ransomware attack.
In this way, protection can be provided to stop Ryuk ransomware and hence prevent serious damage to the systems.
How do I protect my PCs against Ryuk attacks?
1. Use a dedicated malware-removal tool
When it comes to dealing with any type of ransomware, the security solution recommended below is the go-to tool for the job.
Not only is it easy-to-use by pretty much anyone around, but it is highly effective at keeping malware attacks at bay and fixing malware that was already on your system.
This includes, but is not limited to Ryuk ransomware, thus helping your business from having its data encrypted.
What’s more, the program is also very resource-efficient, so no need to worry about a lagging PC, not even during scans

ESET HOME Security Premium
Get rid of any ransomware and malware and stop all threats before getting into your PC.2. Backup your data with religiousness
A lot of companies use a strategy called a 3-2-1 backup plan and it’s called that way because it has three big steps to implement.
- Create at least 3 copies of your important data, including the original.
- Save the 2 copies on different storage devices or media. That will add another layer of security because if one of those fails, you will still have the other one. You can even use different types of storage for each copy.
- Save one of the copies to another location than your business site, disconnected from your local network. You can physically store them in another place or use a cloud backup solution. This way, the hackers or a natural disaster won’t be able to reach and destroy the data.
Of course, you can tailor this strategy to your own business requirements and to the amount of data that you need to back up.
How does Ryuk attacks its victims?
The ransomware named Ryuk ransomware works by encrypting the important data that is available on the network.
The attackers then provide the decryption key to users in return for ransom in cryptocurrency.
The attackers usually aim to hack as many machines as possible, but Ryuk ransomware works in a unique way. The way hackers prepare for the strike makes the attack rare and unique in its nature.
The trickbot trojan is first installed on the system. The trojan basically aims to stay on the system for longer periods of time.
The organizational network is mapped at the next step, and now the attackers can steal the credentials by compromising the network.
Now one of the two standard ransomware notes is sent to the victim’s system just after compromising the system.
The target company is politely advised through the ransom note to decrypt their systems by paying a specific ransom amount in Bitcoin.
The message further threatens the victims to destroy all the files if they fail to pay the ransom. Finally, a contact email and a Bitcoin wallet address are shared with the victims.
If the victim ignores the first ransom message the second ransom note is sent to the victim that threatens him about the consequences.
It is worth mentioning that the new ransomware is alarming for users and might compel them to pay the ransomware.
Half a Bitcoin is added to the amount to be paid with each passing day. The amount to be paid is estimated to be roughly $224,000.
The attackers need to have a clear idea about the financial condition of the target network before launching the attack.
The main reason behind implanting Ryuk into the target systems is the identification of the most important computers and datasets.
Experts still don’t have any idea about the origin of Ryuk. Some of the attackers claim it to be from Russia while others are of the view that it’s originally from North Korea.
We hope that our solutions above helped you protect against Ryuk and you managed to remove it.
You can also try one of the best antiviruses for Windows Server in case that your company uses this type of OS.
Has your company been a victim of this Ryuk ransomware or other such threats? Tell us your story in a comment below.

User forum
0 messages