Event ID 4740: A User Account Was Locked Out [Fix]
Finding the source of the event is important to resolve the issue
4 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Event ID 4740 comes up in the security log when a user account is locked out in Windows.
- Here we will discuss the event and how we can find out what caused it.
![Event ID 4740 A User Account Was Locked Out [Fix]](https://cdn.windowsreport.com/wp-content/uploads/2022/12/Event-ID-4740-A-User-Account-Was-Locked-Out-Fix-886x590.png)
If a user account is locked out, event ID 4740 is added to domain controllers, and event ID 4625 appears on client computers. It is generated when an account is locked due to too many failed attempts.
The event has all the information about the user account that was locked out, the time of the lockout, and the source of the failed login attempts (caller computer name).
In this guide, we will discuss all the reasons for the event ID 4740 and how to find the source of account lockouts.
 Tip
Tip
What causes Event ID 4740, a user account might be locked out?
There are various reasons for the event to be generated. Some of the popular ones are mentioned here:
- Too many failed login attempts – If a user inputs an incorrect password several times, their account may be locked out to stop further attempts.
- Password expiration – The account may be locked out if a user’s password has expired until they reset their password.
- Group Policy settings – Your organization may have set Group Policy settings that lock out the user accounts after a specific number of failed login attempts or after a particular time.
What can I do to determine the source of the Event ID 4740 account lockout?
1. Enable Auditing for event 4740
- Click on the Search icon, type Group Policy Management, and click Open.
- Under Domain, right-click on Default Domain Controllers Policy and select Edit.
- Now on the next window, follow this path:
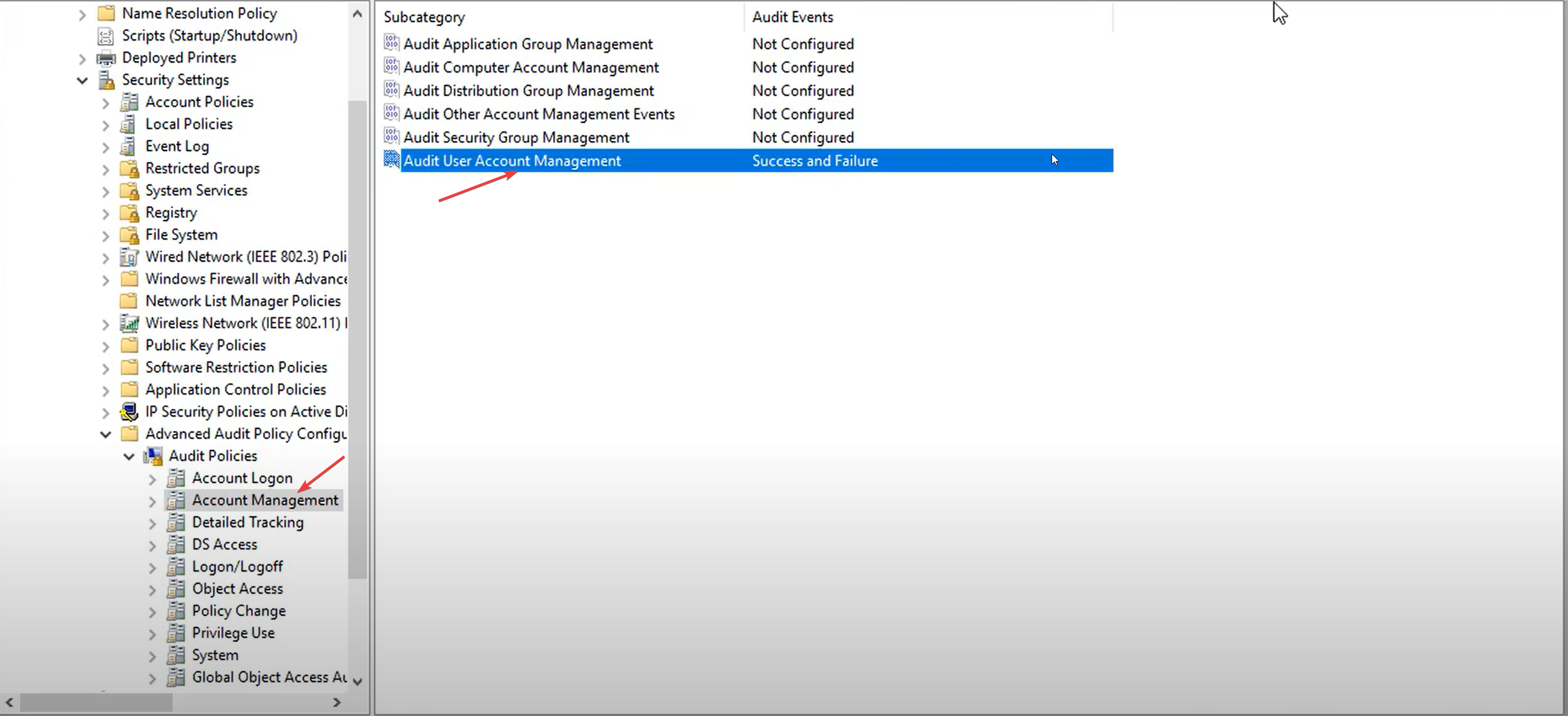
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Account Management - On the right pane, double-click on Audit User Account Management.
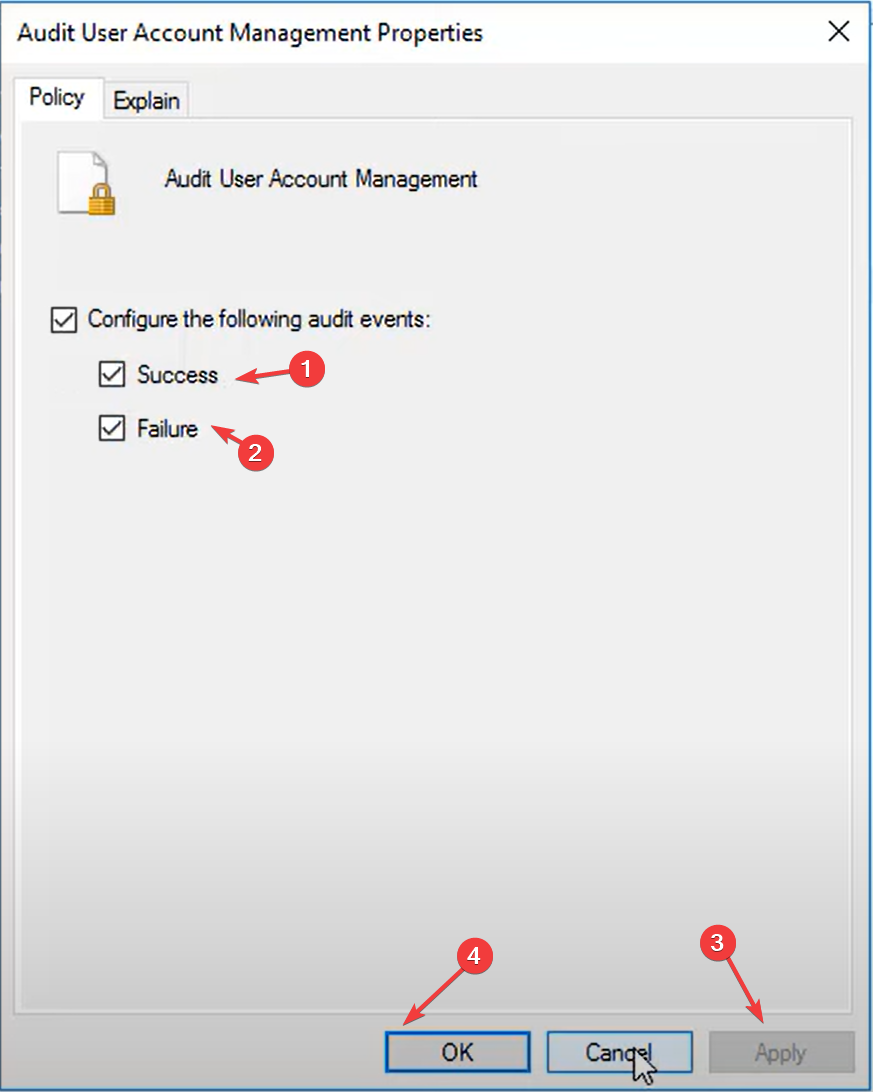
- Put a checkmark on Success and Failure on the Audit user account management properties window.
- Click Apply and OK.
2. Use PowerShell to find the PDC emulator role
- Click on the Search icon, type PowerShell, and click Open.
- Type the following command to know the domain controller that holds the PDC role and press Enter:
get-addomain | select PDCEmulator - To search the lockout events, copy and paste the following command and press Enter:
Get-WinEvent -FilterHashtable @{logname=’security’; id=4740} - To display event details, copy and paste the following command and press Enter:
Get-WinEvent -FilterHashtable @{logname=’security’; id=4740} | fl - You will get the list of logon events.
3. Use Event Viewer
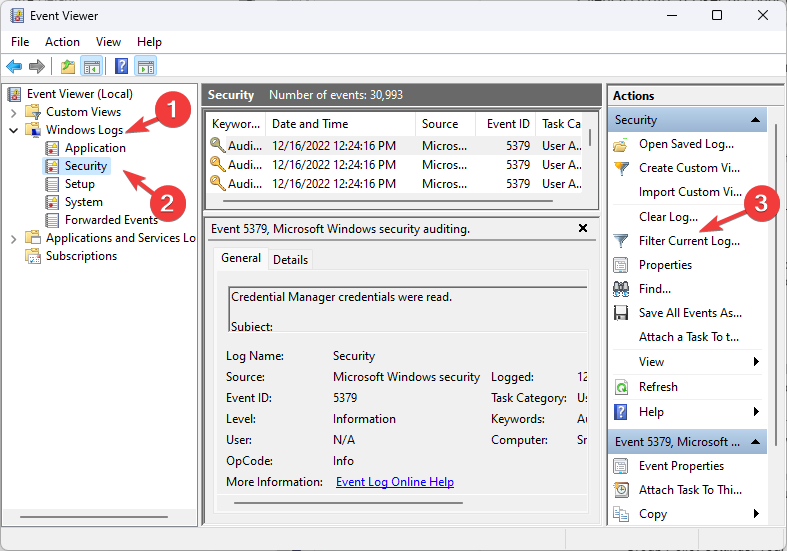
- Click on the Search icon, type Event Viewer, and click Open.
- On the left pane, go to Windows Logs, then click Security.
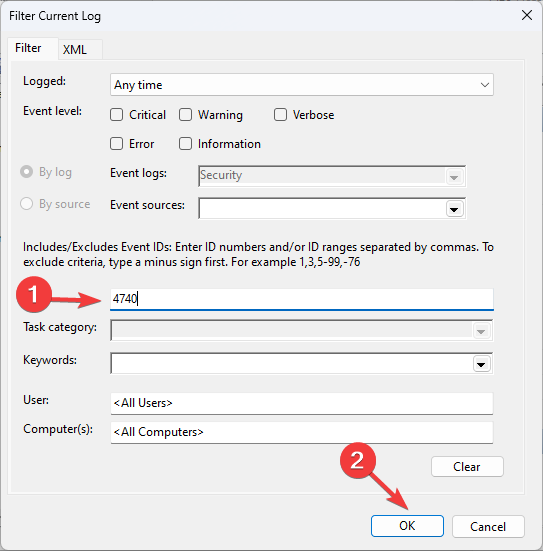
- From the right pane, select Filter Current Log.
- Search 4740 and click OK.
- You will get a list of events Click on the event and check out the details of the source.
4. Use the Microsoft Lockout Status tool
- Download and Install LockoutStatus.exe
- Click the Search icon, type lockoutstatus, and click Open.
- The app will check all the lockout events with all the instances, sources, and additional details.
5. Use a third-party tool
Using a free Active Directory troubleshooting tool like NetTools helps to troubleshoot, update queries, and report Active Directory and other Lightweight Directory Access Protocol directories. It is a portable executable file that allows you to view and troubleshoot Active Directory permissions.
NetTools searches the event logs to locate events relevant to the account on the selected domain controller. Also, it can find the event logs of any member servers in the authentication chain and can display the information related to the reason for the lockout. To know the source, follow these steps:
- Download NetTools.
- Extract the zip file and run the executable file.
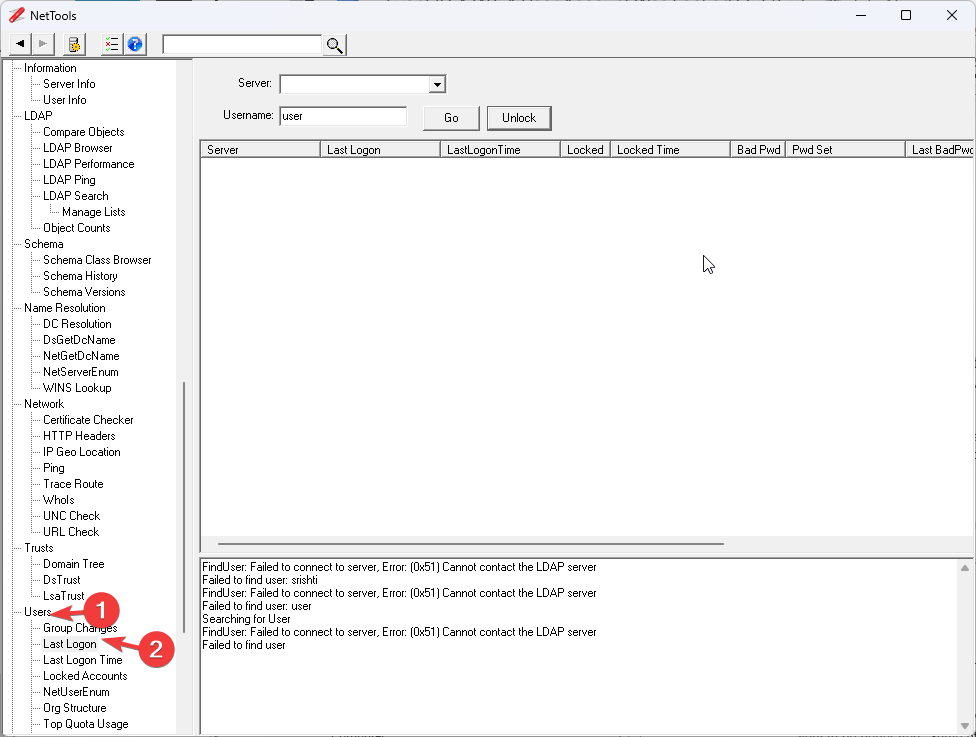
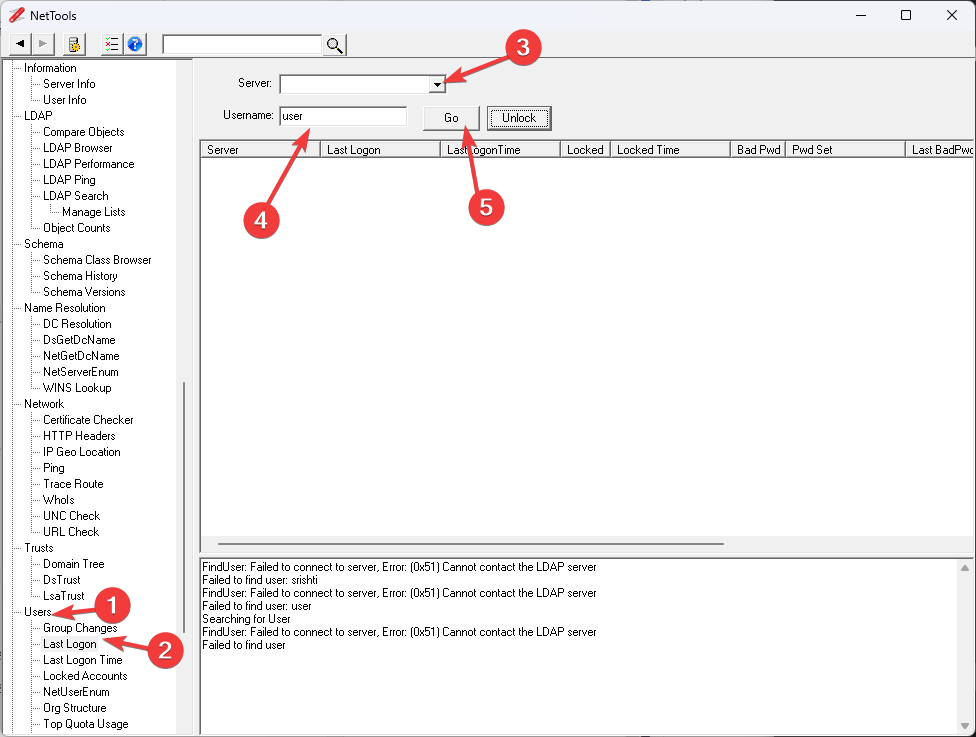
- The tool will launch on the left pane; under Users, select Last Logon.
- Enter the Username and Server, and click Go.
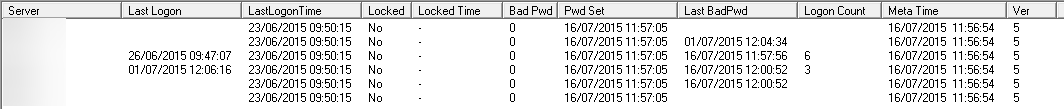
- NetTools will show you all the login details.
- Sort the results using the BadPwd column. The first entry on the list will be when the account was last locked.
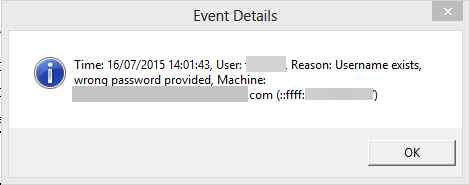
- To get details, right-click the domain controller with the previous lockout time and choose Display Event Details.
So, these are the easiest ways to find out the source of account lockout event ID 4740. Once you get the source, you can easily take steps to prevent it from happening.
Have you already tried some of these solutions? Or maybe you know of other methods to solve this Windows event ID? Feel free to share your expertise with us via the comments section below.