Before opening PDF attachments, check it for embedded links
The attacked started on March 7, 2024 and continued till March 11, 2024
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

According to a recent report by Proofpoint researchers, the Iran-aligned TA450 hackers, who also go by MuddyWater, Static Kitten, and Mango Sandstorm, reportedly used a pay-related social engineering lure, i.e., embedded links in PDF attachments in their phishing campaigns.
The phishing campaign started on March 7, 2024, and continued until March 11, 2024. During this time, TA450 sent emails with PDF attachments that contained malicious links. This isn’t an unusual method for the TA450 hackers; earlier, they used to add malicious links to the email body directly.
This time, they evolved and added an extra step to make it undetectable. They used malicious links in this one as well but employed a slightly different technique. They sent multiple phishing emails with malicious PDF attachments and other embedded links to the same victims.
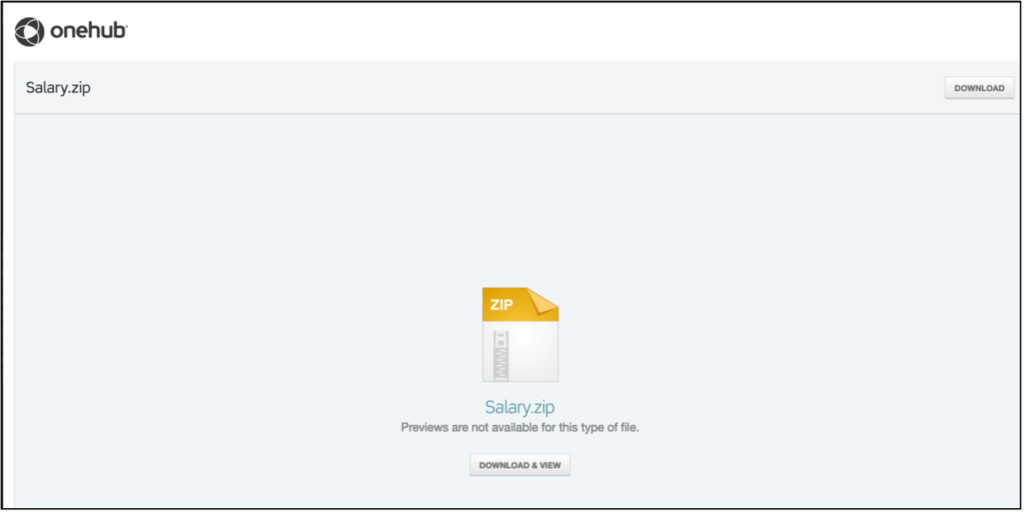
The links led to several file-sharing websites, such as Onehub, TeraBox, Egnyte, and Sync, and the researchers suspected that the email had also been compromised.
Suppose a victim opens the attachment and clicks on the link. In that case, it will download the Zip archive file, which consists of a compressed MSI that would install AteraAgent, a remote administration software that TA450 exploits.
Once installed, the software grants TA450 access to the victim’s device, leading to potential data theft and other malicious acts.
This method worked effectively on targeted Israeli employees at large multinational organizations, and the hackers’ group has been targeting Israeli entities specifically since at least October 2023 with the start of the Israel-Hamas war.
The campaign’s success can be partially attributed to the use of sender email accounts that align with the lure’s content, thereby increasing the authenticity of these phishing emails.
This is the first time the group has used this method, which can be marked as an escalation of the sophistication of the attacks, making it quite difficult for average users to spot.
If you consider the impact, sending multiple phishing emails to the same targets increases the probability of successful infiltration.
Other new attacks also surfaced. One campaign employed an Office trick to fool the victims, and Perception Point spotted it; read the full story here.
With rising risks and increasing attack sophistication, we, the users, must always be cautious when opening unsolicited emails and documents. And, as for security researchers, they must also look out for these types of attacks more aggressively.
What are your thoughts on the matter? Share your opinions with readers in the comments section below.