Malware using Microsoft installers has started spreading through Google Cloud Run outside the LATAM region
More than 300 institutions across 15 Latin American countries are affected.
3 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

15 LATAM countries have been targeted in recent months by malware distribution campaigns that use Microsoft installers and Google Cloud Run to infect devices with banking trojans that steal sensitive information, such as banking credentials.
While they have been initially targeting LATAM countries, these campaigns are now spreading to several European countries using the same method: phishing emails containing Microsoft installer links that are distributed through Google Cloud Run, or Google Cloud storage bucket.
Cisco Talos, one of the largest cybersecurity companies in the world, recently released a report detailing these malware distribution campaigns which include the banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban.
Victims usually receive phishing emails containing corrupted links that can easily compromise devices once accessed. These phishing emails make it seem as if they are sent by official institutions and can be easily mistaken if those targeted are not paying attention.
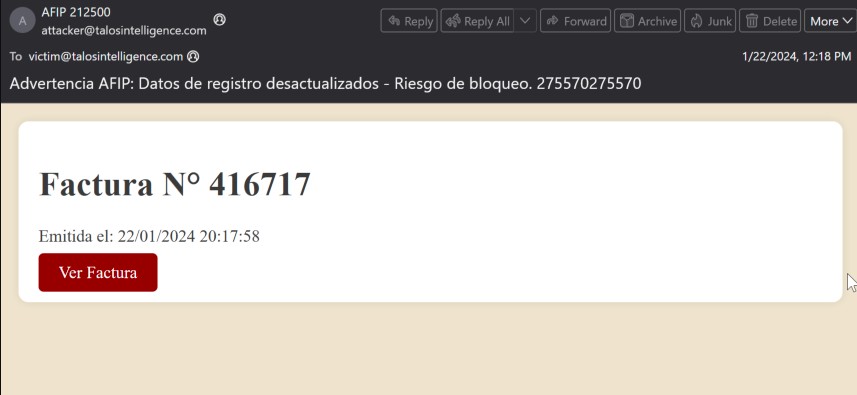
In most cases, these emails are being sent using themes related to invoices or financial and tax documents, and sometimes pose as being sent from the local government tax agency in the country being targeted. In the example below, the email purports to be from Administración Federal de Ingresos Públicos (AFIP), the local government tax agency in Argentina, a country frequently targeted by recent malspam campaigns.
Cisco Talos
The threat actors use a combination of Google Cloud Run and Microsoft installer tools to make sure the malware reaches its targets, as Cisco explains:
When victims access these hyperlinks, they are redirected to the Cloud Run web services deployed by the threat actors and delivered the components necessary to initiate the infection process. As previously stated, we have observed Astaroth and Mekotio being distributed in this manner in the form of malicious Microsoft Installers (MSI) files as the Stage 1 payload to begin the infection process. We’ve observed two recent variations in the way the MSI files are being delivered. In many cases, the MSI file is being delivered directly from the Google Cloud Run web service deployed by the adversary as shown in the case of Mekotio below.
Cisco Talos
According to the cybersecurity company, the threat actors have already infiltrated the European market, as several European institutions noticed suspecting emails written in Spanish or Italian. Those European institutions that are affected by it, should take immediate action, and for good reason too. Cisco says the Astaroth variant already caused damage to over 300 institutions across 15 Latin American countries.
Google and Microsoft haven’t released any official statements on the matter, but Microsoft recently updated its Copilot for Security to assess the new AI-based cyber threats that are starting to become popular and efficient.
However, the classic phishing-based attacks are just as dangerous.
You can read the full report here.