Midnight Protocol game review: Feel like a real hacker
9 min. read
Updated on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Key notes
- Midnight Protocol is a tactical narrative-driven RPG with unique keyboard-only controls.
- It lets you live out your hacker fantasies in a futuristic world where everything is controlled by computers
- It has a surprisingly emotional story to tell and offers enough ways for even inexperienced players to fully experience it

Midnight Protocol is a tactical narrative-driven RPG with unique keyboard-only controls. Hack into servers, beat security systems, and discover encrypted secrets while you try to find answers to why and how you got doxxed.
When I was first introduced to Midnight Protocol at 1UP Conference, a local Belgian gaming expo that I helped organize, I have to say that it didn’t manage to draw my attention in the same way most games would. The vast majority of games out there try to pull your attention with fancy visuals and cool animations, but with a text-based hacking game, you really need to sit down and let yourself become immersed in its world.
I[M]MERSIVE HACKING EXPERIENCE
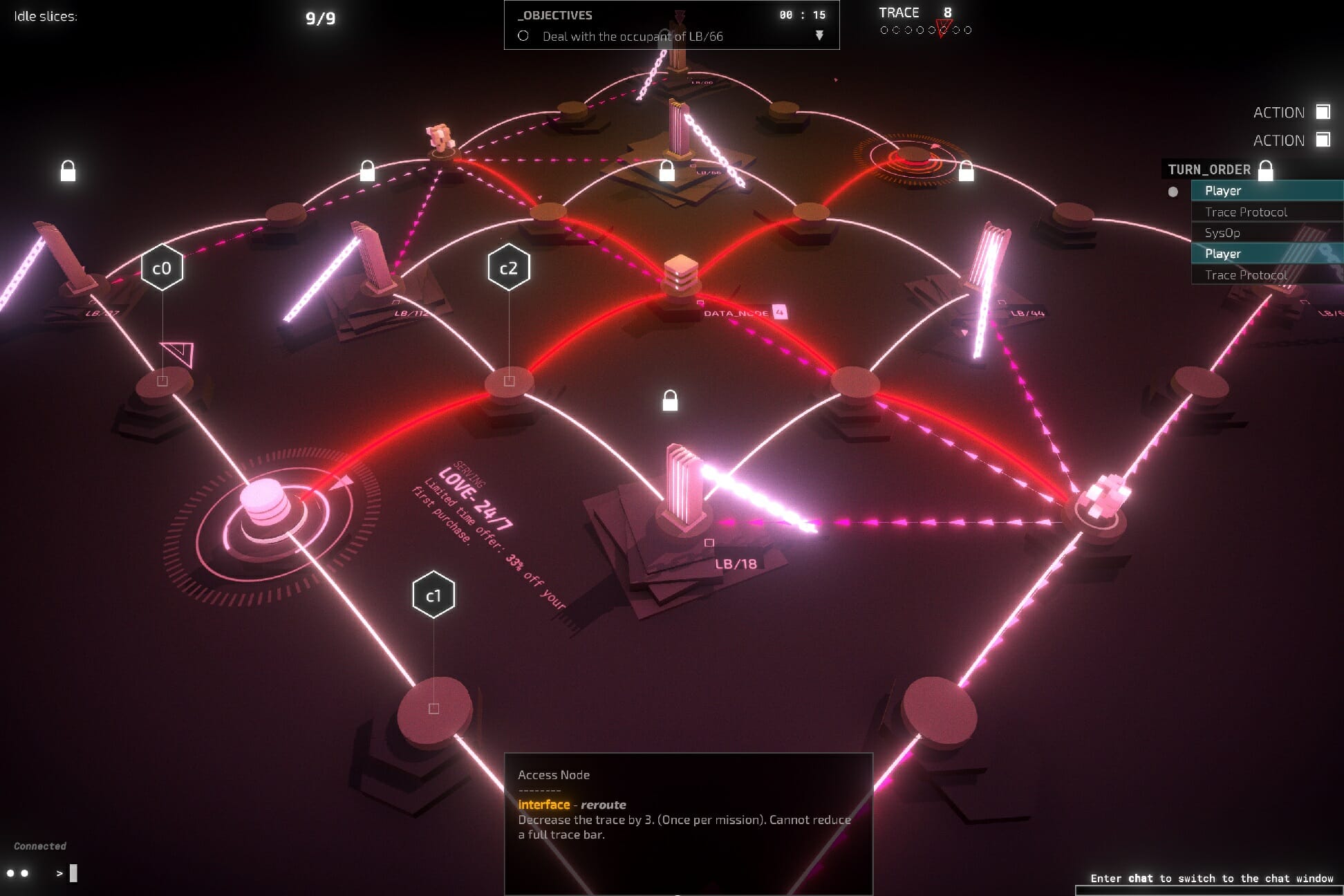
Immersing players into feeling like a true hacker is where Midnight Protocol excels. You control the entire game by keyboard only, no cursor is visible at any time, and it feels… glorious!
There is something oddly satisfying about typing commands and seeing a computer execute them, and that’s basically what you’ll be doing the entire game. Typing Move S3 (or . S3 if you want to speed things up) moves you to that node on a digital network board.
Need to break a firewall that’s blocking your path? Type Dagger, Shuriken, or Jackhammer to tear it down. Want to avoid it altogether? Tunnel your way to the other side.
Almost every network address has multiple ways to approach the puzzle: if you encounter a safe, you can go look into data nodes for the password, or you can strongarm it with a Rainbow program. Is an encryption node blocking you from interfacing with it? Then you’ll need to decrypt it first.
[E]MOTIONS WITH NOTHING BUT TEXT
The game starts off great with some cool ideas like allowing you to enter the username Data yourself (you don’t get to pick a custom handle) and your password. It doesn’t really matter what you type here, the game will autocomplete each character with every keystroke you make.
It’s a nice little touch that I could really appreciate and this level of attention to detail is maintained throughout the game.
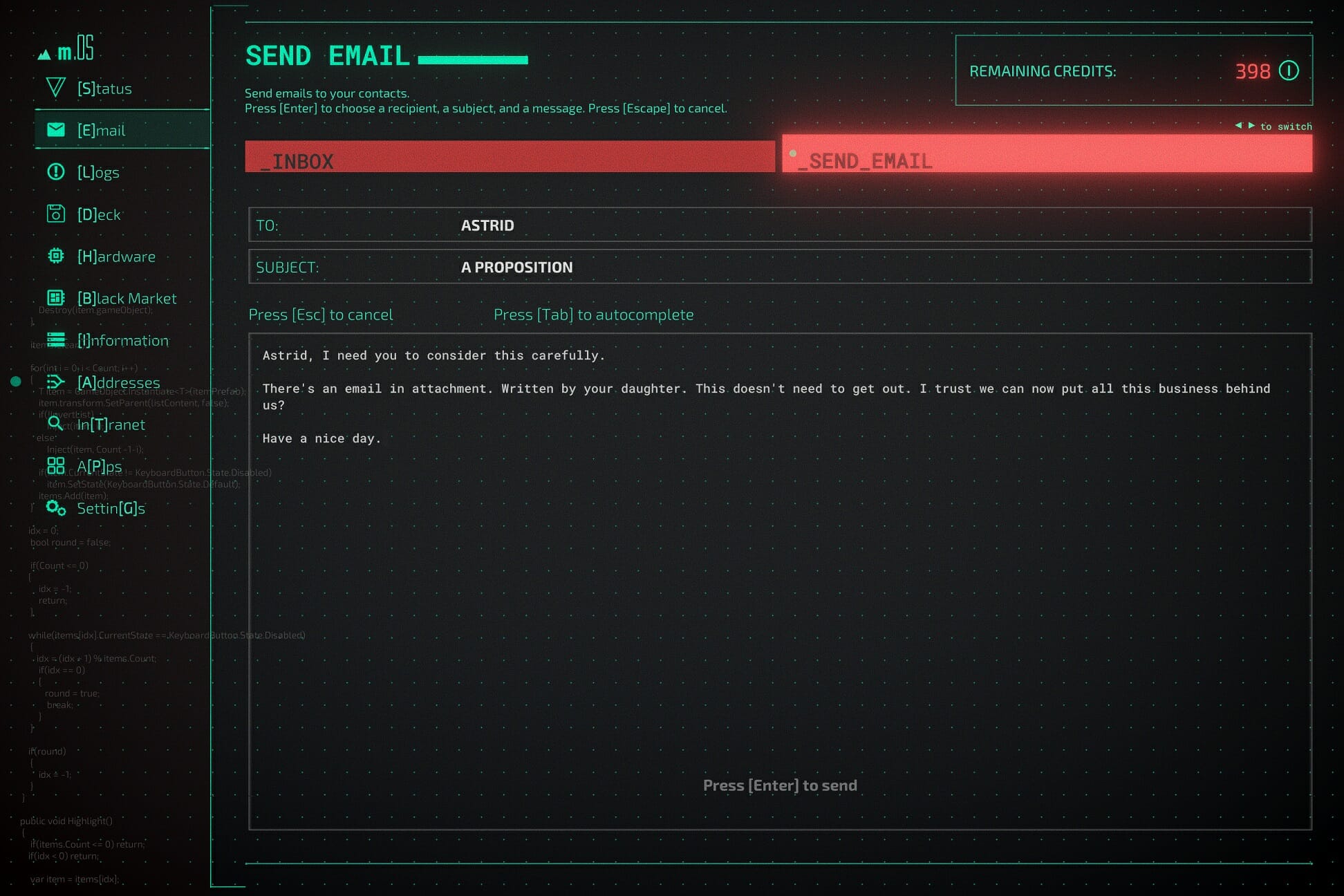
It’s further used in the communication by email or chat, which accounts for the majority of the storytelling: just type away on your keyboard and the game will fill in the actual message, including backspaces and moments where the protagonist seemingly changes their mind.
At a later point in the game, when I delivered a harsh message to a person on the other side of a chat, you could see their […] appear on screen a few times and then disappear again, indicating that they are also reconsidering what to say. It’s only text and icons, yet it conveys a lot of emotion.
[S]TORY TIME
To set the binary stage: Midnight Protocol takes place in the near future where the online world has grown to become even more important and with key operations all relying on digital information. It’s no surprise then that there is an equally increased activity from hackers who are either out to make a profit or those who use their skills to make the world a better place.
The story centers around a hacktivist called Data, who recently got doxxed after their personal information was shared for all to see. It’s up to you to set things right and uncover the many mysteries in this digital world. Luckily you won’t have to do this alone and you can count on fellow hackers to lend you their 10 digits.
Even though you never even see their faces, you quickly grow a certain attachment to your hacker friends and some of them even join you on the network to assist in taking down the evil corporations that think they own the net.
[R]PG ELEMENTS
Each person playing Midnight Protocol will probably approach challenges in a different way. There are quite a few things you can customize, like the programs in your deck. some examples:
- Cloak helps you move through networks unnoticed
- Spoon lets you chip away at encrypted nodes instead of manually interfacing with it multiple times
- Leech does the same, but drains money to your personal account
- There is even a variety of offense moves that each have their pros and cons
Your deck has a finite amount of slots but you can buy Hardware upgrades that increase your deck size or ones that slow down how quickly you are traced on a network.
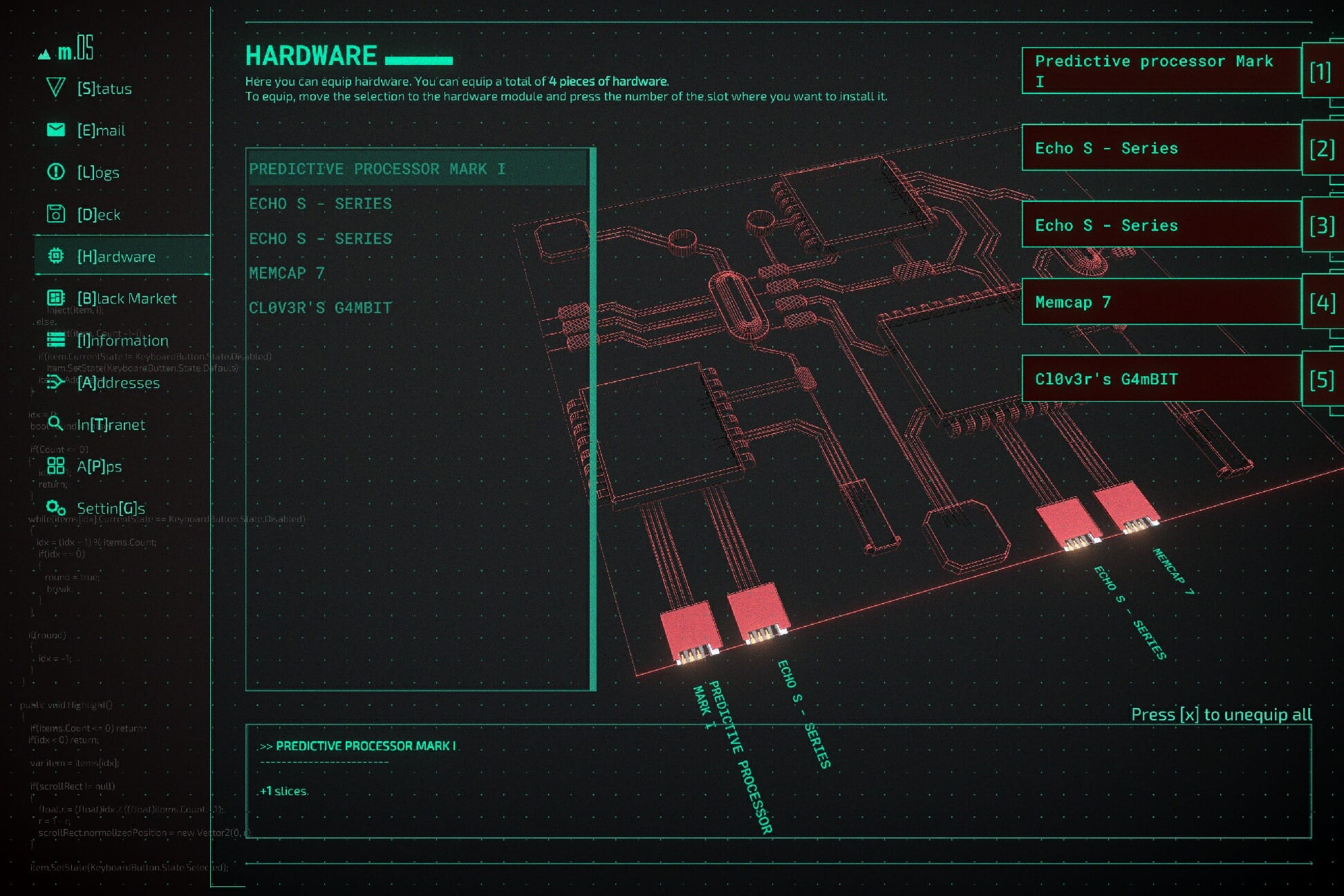
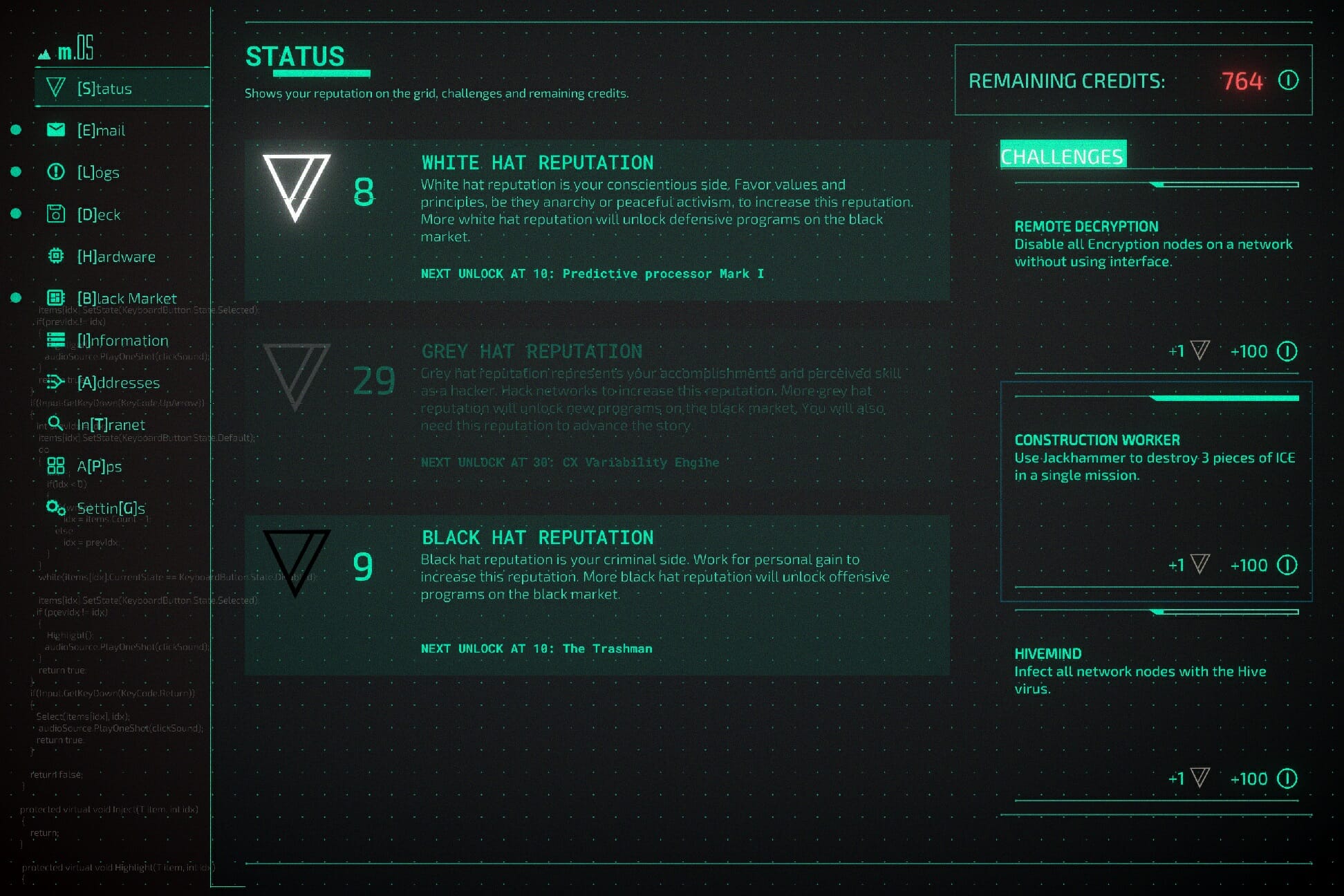
Which programs you can add to your deck are in part decided by how you play: if you gain more Black Hat reputation by stealing money, you’ll get more offensive tools at your disposal whereas Open Sourcing data can give you White Hat rep and opens doors to more ways to stay below the radar.
[S]CREENSHOTS DON’T DO THE GAME JUSTICE
Just taking a look at some of the above screenshots will probably not be enough to convince you to buy the game. While it doesn’t look bad by any means and has some impressive effects, most of the time you’ll be looking at text and UI elements, which take up a large part of the screen space.
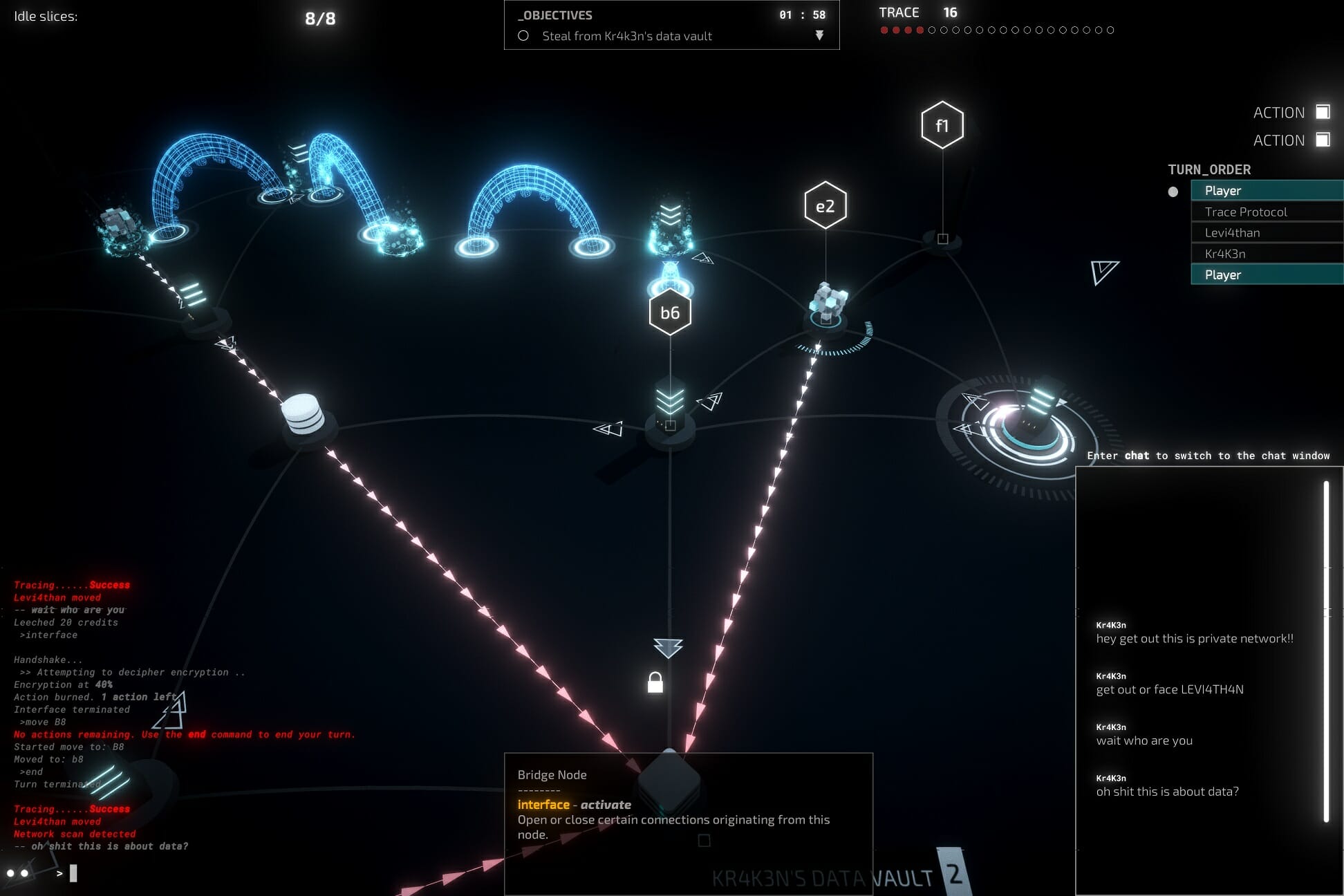
But the animations that are present more than do their job, especially combined with the intense soundtrack. The image below shows a program called LEVI4TH4N which slowly chases you through the level. It looks great and there certainly is a feeling of dread as the tentacles creep closer to your current location.
[G]OD MODE ACTIVATED
While Midnight Protocol is turn-based and you can take however long you want to plan your next move (in the default settings at least), it’s not exactly what I would categorize as an easy game. Sure it introduces you to new systems in a clear way and you soon understand most of the inner workings, but I still couldn’t shake the feeling I wasn’t working optimally.
Luckily the game has a lot of accessibility options for people who just want to experience the story and for whom the challenge isn’t as important. You can make it easier on yourself by giving you more time before the enemies can trace you and you can even decrease the hit points on the ICE (firewalls and other traps).
You can also retry any level as many times as needed, with different programs installed, but I grew a bit impatient from all the trial and error myself. Especially because losing means having to replay the entire level from scratch.
That’s why I quickly decided to turn on the God Mode, which never increases your trace, giving you all the time in the world to explore the networks and letting you focus on the story developments. This certainly pays off, because there are a ton of hidden secrets and I wanted to uncover them all!
[B]ONUS CONTENT
If you go for the main story and most of the side quests, it should take you around 20 hours to complete the game. I had about 11 hours of game time on the clock when I beat it, but that’s mostly because I ignored opportunities to gain some quick bucks and the God Mode saves me a lot of time as well.
But all the side content is very much worth exploring. The tweet from above and the screenshot below are probably my favorite example, with an entire mission told in rhyme (some returning readers will already know I’m quite fond of that ) and feeling like a Dungeons & Dragons campaign, with poisonous traps and a big boss fight waiting for you at the end.
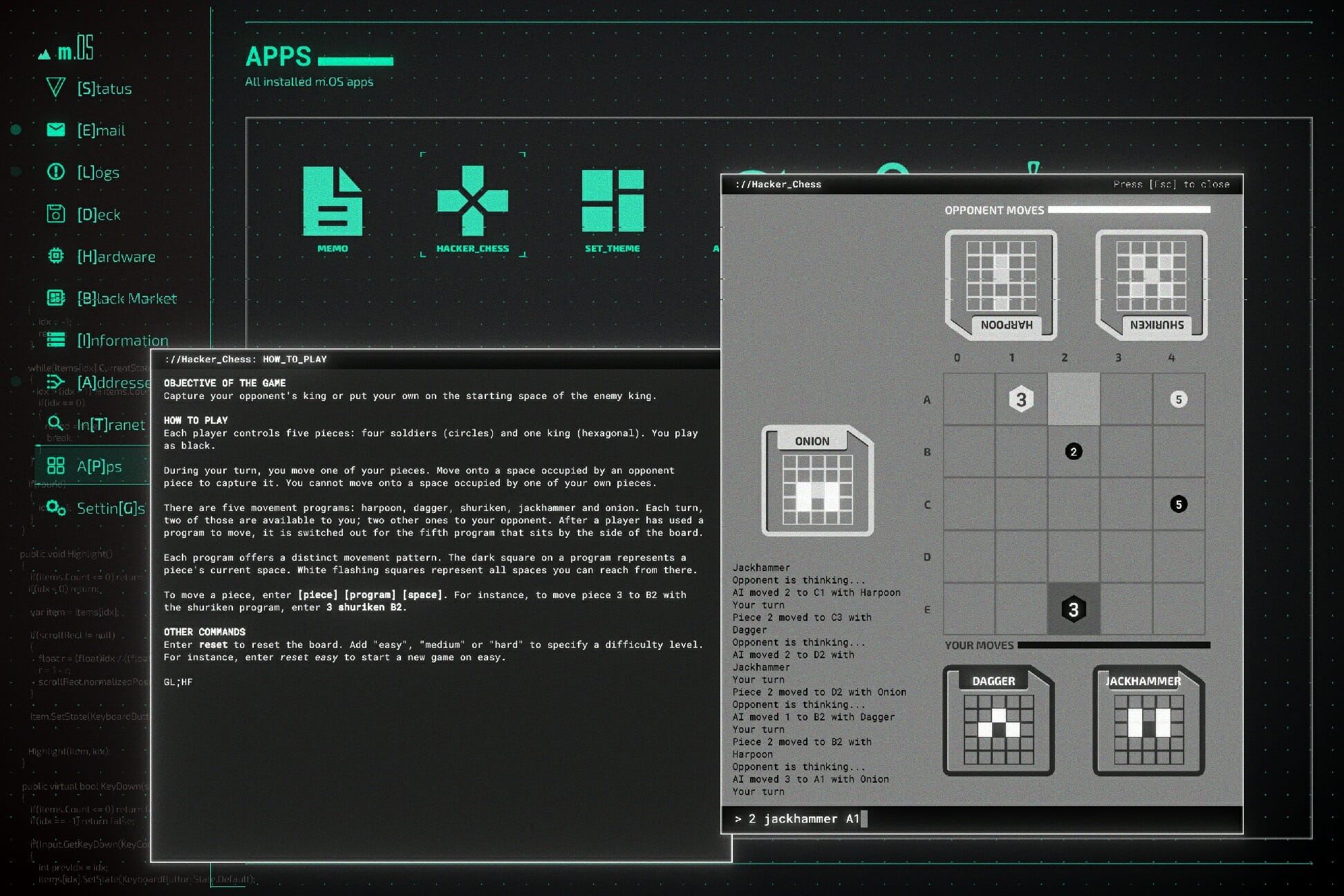
To even get to that level, I had to follow a sidequest up to a point where a Wizard dropped a hint to move my soldier to B5 which was a hint to play a game of Hacker_Chess, a fully working chess minigame where your pawns move based on patterns and attacks from the main game.
There are a ton of little things like this hidden in the game (and even in the game files, *wink-wink*) that somehow unlock secrets, from extra content to extra cosmetics that alter the font colors on your screen. It’s absolutely delightful uncovering these so I won’t spoil any more than I already have.
[F]INAL THOUGHTS ON MIDNIGHT PROTOCOL
- Pros
- Midnight Protocol genuinely makes you feel like a real hacker
- It has a great story with lots of twists and turns along the way
- It lets you experiment and create your own customized playstyle
- Cons
- A bit too unforgiving without God Mode on
- Making a mistake can mean replaying an entire level from scratch
Final Score: 4/5
Midnight Protocol lets you live out your hacker fantasies in an engrossing cyberpunk world. It’s got a gripping story full of unexpected twists and turns which surprisingly managed to convey a lot of emotion through text alone.
Because of the game’s difficulty options, even people who lack the skills or patience to hack their way to the credits can still enjoy the narrative work. Even if you’re on the edge, I’d definitely recommend playing the demo as nothing you read or see in online coverage will do quite as good a job at selling the game than experiencing it firsthand.
Midnight Protocol costs $14.99 and is currently only available on PC. Because of its typing gameplay, we won’t soon see a console release. It’s not very demanding graphically, so you should be able to play it on lower-end hardware as well. You can check the requirements on Steam.
*Disclaimer: Reviewed on Windows 10. Steam review copy provided by the publisher.